117 results for: hack
The best and most amazing Alexa Hacks you should know about
Category : Operating systems 30-06-2023 by Janeth Kent
Android Hidden Codes: unveiling custom dialer codes and their functionality
Category : Mobile 02-06-2023 by Janeth Kent
The ultimate cybersecurity checklist for programmers
Category : Security 02-06-2023 by Silvia Mazzetta
htaccess Rules to Help Protect from SQL Injections and XSS
Category : Security 01-03-2021 by Janeth Kent
Cybersecurity and Data Privacy: Why It Is So Important
Category : Security 26-02-2021 by Janeth Kent
Interesting and Helpful Google Search Features You’ll Want to Start Using
Category : Software 31-01-2021 by Iveta Karailievova
Some Neat Ways to Improve Your Internet Browsing Experience?
Category : News and events 21-12-2020 by Janeth Kent
Making AJAX requests to a REST API using vanilla JavaScript and XHR
Category : Javascript 25-11-2020 by Iveta Karailievova
The BleedingTooth vulnerability and other Bluetooth security risks
Category : Security 10-11-2020 by Iveta Karailievova
How to prevent your neighbor from hacking your Chromecast
Category : Networking 26-10-2020 by Luigi Nori
How to securely access the Dark Web in 15 steps. Second part
Category : Security 08-03-2024 by Janeth Kent
How to securely access the Dark Web in 15 steps. First part
Category : Security 08-03-2024 by Silvia Mazzetta
What cybersecurity professionals have learned from the lockdown experience
Category : Security 26-08-2020 by Silvia Mazzetta
Awesome JavaScript Games and Js Software to create Games
Category : Javascript 30-06-2020 by Janeth Kent
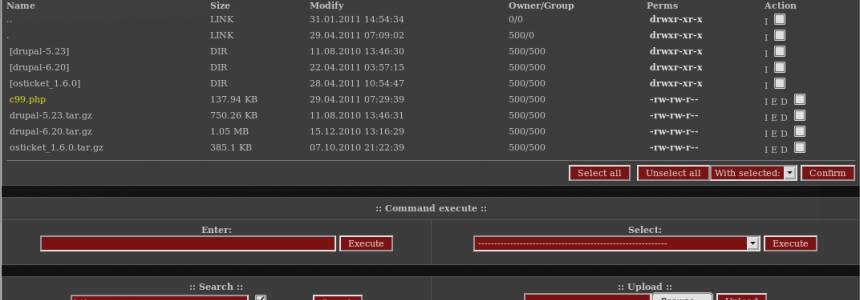
Web shells as a security thread for web applications
Category : Security 04-05-2020 by Iveta Karailievova
The best websites of the Tor Deep Web and Dark Web Network
Category : Security 03-11-2022 by Janeth Kent
How to find everything you need on the Deep Web and the Dark Web
Category : Security 10-05-2021 by Silvia Mazzetta
What Are The Best Methods to Make Money Online
Category : Web marketing 12-06-2020 by Silvia Mazzetta
How They Can Hack You While Navigating: Protecting Your Digital Security
Category : Security 23-06-2023 by Silvia Mazzetta
Layouts with Bootstrap 4: how to create a responsive web
Category : Web design 23-11-2019 by Silvia Mazzetta
Javascript overcomes Java as the most popular programming language of 2019
Category : Javascript 18-09-2019 by Silvia Mazzetta
Best Open-Source Javascript Date Picker Plugins and Libraries
Category : Javascript 23-07-2021 by Janeth Kent
Progressive Web Apps Directory: The Best Collection of Resources
Category : Javascript 20-06-2019 by Janeth Kent
Unlock Hidden SmartPhone Features with these Secret Codes
Category : Security 26-07-2025 by Janeth Kent
How to Get the Most out of Digital Technology in Business
Category : News and events 29-03-2019 by Janeth Kent
The Steps to Take if You're the Victim of a Cyber Hack
Category : News and events 27-03-2019 by Janeth Kent
How to Configure the Mod_Security Core Ruleset in Ubuntu
Category : Servers 04-03-2017 by Janeth Kent
Ubuntu servers security: 25 security tools to armor your system
Category : Servers 14-09-2016 by Janeth Kent
SQLMAP installation and usage in Ubuntu and Kali linux
Category : Security 13-08-2016 by Janeth Kent
PHP7: Guide and References to all the changes between version 5.x and 7 of PHP
Category : Php 27-12-2015 by Janeth Kent
11 Open Source JavaScript Libraries for Web Developers
Category : Javascript 17-06-2020 by Janeth Kent
Becoming a Web Professional: 19 online resources
Category : News and events 18-07-2013 by Janeth Kent
WordPress tips and tricks: how to custumize your theme
Category : Web design 10-07-2013 by Janeth Kent
Mastering JavaScript: Top Resources to Propel Your Learning Journey
Category : Javascript 23-06-2023 by Janeth Kent
Mobile Malware Targets Android Phones: new Kaspersky Lab report
Category : Security 23-05-2013 by Janeth Kent