Let's continue with the 2nd part of our article in which we try to give you some advice on how to safely and securely explore the dark web.
Let's restart from number 6.
6. Changes the security level in the Tor browser
It is also possible to increase the security level of the Tor browser. You can do this by clicking on the Tor logo in the upper left corner. Now select Security Settings. A pop-up window will appear that allows you to change the security level from medium to high.
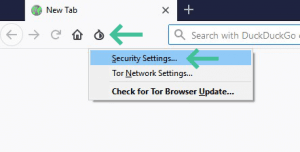
Naturally, the highest configuration is the safest. Unfortunately, this configuration significantly slows down your Internet connection and makes some sites not fully functional. The highest security settings will disable most video and audio formats, some fonts and icons may not be displayed correctly, JavaScript is disabled and some images may not be displayed correctly, among other things.
Tor has included this security setting with the exact intention of protecting its users from the many sites on the dark web that might try to take control of your device or spread malware. However, this setting is restrictive, since it does not allow the unlimited browsing experience of the dark web. In the end, it is a choice between security and access. We recommend using the highest security settings.
7. Check for IP, DNS or WebRTC leaks
It is possible that, even after all these security precautions, an IP or DNS leak may still be occurring. What this means is that through some kind of error or leakage, your IP address is still traceable by third parties. WebRTC is built into most browsers to enable real-time communications such as voice and video calls. This allows you to talk directly from your browser using your webcam, microphone or headset. The problem is that most voice calls are sent over a point-to-point connection, which requires your exact IP address. So, if you're in Google Chrome, for example, and you have WebRTC running, your real IP address will be revealed even when you're using a VPN. This problem is especially common in Google Chrome. To subvert this feature, you can install this Chrome extension.
To check if your connection is really anonymized, go to the following websites:
On these pages you can see if your real IP address is visible. All these sites do essentially the same thing. At the top of the page, you can see your public IP address and below it is your location. If your VPN is working properly, your real address and IP address will not be visible anywhere on the page.
8. Keep in mind the common myths of the dark web
There are many myths about the dark web. Knowing them will give you a better perspective of what you can find and expect to do on the dark web. By being aware of these myths, you are less likely to fall prey to a hacker or scammer. These are some of the most common myths:
All cybercrime happens on the dark web: Most cybercrime takes place on the normal web.
The dark web is immense: Compared to the deep web, the dark web is relatively small. The deep web is composed of academic databases, bank portals, corporate data, company networks, web mail accounts and much more. This is much larger than the 250,000 to 400,000 websites that exist on the dark web.
The dark web is only for professionals or technology nerds: Taking the right precautions, anyone can access the dark web relatively safely. The Tor browser, VPN and Tails or other live operating system are available to anyone and are not too difficult for a beginner to use.
The dark web is illegal: The dark web itself is not illegal: The Tor browser you need to access the dark web; however, it uses very strong encryption that is illegal in some countries. As such, dark web is indirectly illegal in some countries. These countries, however, tend to have more far-reaching Internet restrictions. These are countries such as China, Russia, Belarus, Turkey, Iraq and North Korea
Anything you can do on the dark web is illegal: The dark web itself is not illegal, nor is everything that happens there illegal. Whether something is illegal or not on the dark web depends on the country from which the dark web is accessed. For the sake of clarity, apply this general rule: if something is illegal in the country you are in, it will also be illegal to do the same on the dark web. So, if it is illegal to sell drugs on the street, it is also illegal to sell drugs on the dark web. When in doubt, always make sure you find out what is legal and what is not
9. Use additional anonymous services
Even if you enter dark web completely anonymously, it is still possible to unintentionally disclose your personal information by using some online services such as search engines, extensions, file sharing, messaging applications, emails, etc. Many online services use cookies, trackers and scripts to collect specific data about you. That's why it's best to choose alternative online services that value privacy. Below, you can find a number of services that are good for safeguarding your privacy.
Anonymous search engines
DuckDuckGo is a good private search engine, and you can use it instead of Google. While most search engines don't work on the dark web, DuckDuckGo does. The onion address is https://3g2upl4pq6kufc4m.onion/
Other alternative search engines that will work on the dark web are SearX and Startpage
Secure passwords
Secure passwords are even more important on the dark web than on the normal (superficial) web. If you don't want to suffer the inconvenience of thinking of a decent password every time and keeping it safe, you can use a good password manager. Two good options are Bitwarden and LessPass. Both are free and open source. The best option is to upload these services through your website.
File Encryption
If you are going to download or upload files to the dark web, it may be a good idea to encrypt them. A free, reliable, open source encryption tool is PeaZip. This tool supports 181 different file formats. Unfortunately, PeaZip is not available to MacOS users. An alternative for Mac users is Keka.
Anonymous upload/exchange
If you want to share files anonymously, OnionShare is a very good option. It is available for Windows, MacOS and Ubuntu. Dropbox and other similar file-sharing programs are notorious for not respecting the privacy of their users or data. With OnionShare you can share files of all sizes through a web server. An alternative is Firefox Send. Although it was designed by the creators of Firefox, you can also use it outside the Firefox browser. With this service, you can share files of up to 1 GB or 2.5 GB per upload if you create an account, which we do not recommend.
Anonymous Office Services
If you're looking for an alternative to Google Docs with better security, take a look at Etherpad. This software is completely open source and you don't even need an account to use it. Another option is Cryptpad. You can use it to write text, create spreadsheets or make eye-catching presentations. Only those who receive the passwords can access a file.
Video calls (VoIP)
For (video) calls there are several good services available, such as Linphone or Mumble. Linphone is free and open source, can be used in Windows, MacOS, iOS, Android and GNU / Linux. The software has an end-to-end encryption. Mumble is a little different. It is designed specifically for games, does not keep any records and does not record any conversations. However, it does not have any end-to-end encryption. It is available for Windows, MacOS X, iOS and Ubuntu.
Send anonymous messages
Ricochet or Signal provide more secure text messaging means than your standard messaging application. Another good option is TorChat. This application is part of Tor and allows you to chat with anyone who is also using it. You don't need to sign up. TorChat automatically assigns you a numeric ID to send to the person you want to talk to. You can do this by telling the other person directly (face to face) or by sending your ID number through an encrypted email (see next step). This allows a huge degree of anonymity when chatting, usually you can't go anywhere else.
Send emails securely and anonymously
A highly praised email service is ProtonMail. Their email accounts have standard end-to-end encryption. E-mails sent through Gmail or Hotmail are generally easy to intercept and/or decrypt. Encrypted email services are a much more secure option. These services tend to have more rigid data limits. So if you plan to use only encrypted email accounts, you may want to create more than one. Here's a list of encrypted email providers.
It is also possible to create a temporary (disposable) email address. The advantage of this is that you can create an online account on any website, confirm your registration and then not worry about your inbox being bombarded with useless emails from those websites. Some known temporary email providers are: TempMail, 10minutemail and Guerrillamail.
If you really don't want to switch to a different email address to browse the dark web, at least make sure your standard email account receives additional protection through PGP ("Pretty Good Privacy"). This can be done by adding an additional service on top of your standard email account like Mailvelope. This service works with providers like Gmail or Hotmail, and many more. Please note that this option is less secure than a temporary email address or an encrypted email address. A lot of information about you can be tracked through your regular email address.
10. Avoid logins, plugins, subscriptions and payments
If you want to browse the dark web safely, anonymity is the best option. If you decide to log in to certain bank or user accounts, your anonymity will be compromised. It is never a good idea to log in to your bank account while you are on the dark web. Once you've logged into a user account, every activity on that site can be attributed to that profile, with or without Tor. Therefore, it is best not to log in to any profile or account while surfing the dark web.
However, some sites require you to have an account to access them. In this case, you can create a random, disposable email address, create an account that you cannot be identified with in any way, and use this account to browse the web. Creating an untraceable user account means not using your name, birth date, hobbies, interests, location, etc. The more random and anonymous it is, the better. For more help on creating a secure password, see this guide.
Most people use at least some plugins in their browsers. Many of these plug-ins can collect personal information about you, your location, and your online behavior. Therefore, it is best not to have them enabled while you are searching the dark web.
What do you think about the second part? Was our advice useful?
If you missed the first part of the article or are bored while waiting for the 3rd and last part, you can go back to reading the first one:: How to securely access the Dark Web in 15 steps. First part

