Most of the actions you take online are not as private as you might imagine.
Nowadays, countless people and groups try to follow our online behaviour as closely as possible. Our ISPs, our network administrators, our browsers, search engines, the applications we have installed, social networks, governments, hackers and even the websites we visit know, to some extent, what we are doing when we are online. If you don't want your partner to discover that special gift you just ordered for his birthday, it will be enough to use the incognito mode. However, if you don't want anyone to know what you are doing online, a simple incognito mode will not work.
Do you want to surf, stream or download anonymously? There are a few ways to protect your privacy online. In this article we will introduce you to a couple of methods and tips you can use to remain anonymous when you are online. We'll tell you all about the effectiveness of VPNs, proxy servers and Tor, all of which are tools to help you stay off the radar.
Tip 1: Secure and anonymous surfing with a VPN
The use of a VPN (virtual private network) is an appropriate way to surf the Internet anonymously. When you are connected to a VPN server, your connection is secure. The software ensures that all your online traffic is encrypted using special protocols, so that others cannot read this data.
In addition, your IP address remains hidden, as it automatically takes the IP of the VPN server you are using. An IP address is the identification number of your Internet connection, and can reveal your location and ultimately your identity. A VPN hides this IP address behind its own IP. This way, the websites you visit will not be able to see your real IP address and will not be able to identify you.
Many VPN providers do not record your activity while you use their services. This is the product they promise you: anonymous surfing. These providers offer their users guaranteed anonymity with their secure VPN connections.
Combining a masked IP with a secure connection ensures VPN users that no one can follow what you're doing. However, not all VPN providers are as strict when it comes to delivering on this promise. If you wish to anonymise your Internet connection, it is important to find a good and reliable VPN provider with a zero-registration policy. A zero-registration policy ensures that the VPN provider does not record any of your online activities. So even the government cannot make a provider turn over this information, because there is simply nothing to turn over. Most of the time, it is a very good idea to go for a premium VPN, as your private data is not always secure in the hands of a free VPN provider.ç
ExpressVPN: A trusted giant
An example of a trusted VPN provider is ExpressVPN. ExpressVPN has a large number of servers worldwide and offers strong security options. If you subscribe to their services, you will get access to software that protects all your devices and works on Windows, Mac, Android and iOS. You can connect to the Internet with up to five devices simultaneously with a single subscription. ExpressVPN is well suited for those who want to be able to surf, stream and download with complete anonymity.
ExpressVPN is very easy to use. After purchasing a subscription, you can install the application and connect to a secure VPN server with just a few clicks. The application will run in the background and you will be able to browse and stream as you always have, but securely and anonymously. If you want to know more about this provider, please read our full review of ExpressVPN.
CyberGhost: An easy to use VPN
Another VPN with good performance is CyberGhost. CyberGhost is an easy-to-use VPN provider that helps you browse anonymously. They have a large number of servers around the world, which makes it extremely easy to find a server that suits your needs. Their servers will make sure that you can surf the Internet without restrictions. With CyberGhost you can even view Netflix and download torrents freely. The CyberGhost application is very easy to use and if you have problems using it, CyberGhost also has an excellent customer support team to help you.
If there is an HTTPS alternative to an HTTP website you are trying to visit, CyberGhost will make sure that you are automatically redirected to the secure version of the website. So you can surf anonymously and securely at all times. Read our detailed review of CyberGhost for more information on this VPN.
Tip 2: Use the right browser
It's wise to get back to the basics and make sure they help protect your anonymity. But which browser is best to use in this case? The most popular browsers have very different ways of dealing with user privacy. They also have different levels of security. In this section we will discuss several well-known browser alternatives.
Stay away from Microsoft Internet Explorer and Edge
In view of the security and privacy of the online environment, we recommend that you do not use Microsoft's browsers (Internet Explorer and Edge). Internet Explorer no longer receives updates, making it very vulnerable and exposing its users to various risks, including many forms of cybercrime. Microsoft Edge is the official successor to Internet Explorer and receives security updates. Even so, the privacy levels of this browser are not very good. It does not have any tracking protection, which other browsers do. For this and other privacy options that Microsoft lacks, we advise you to stay away from Internet Explorer and Edge if you want to focus on protecting your privacy.
Google Chrome - Don't search for privacy on Google
The Chrome browser supports several pop-up blockers and other privacy-oriented extensions. Even so, Chrome is owned by Google, which is not good news for your privacy. Google benefits from having as much data about its users as possible. This data is used to display customised ads and to improve the Google search engine. Many people criticise Google about the way they treat people's privacy. For example, it has been questioned why Chrome users often automatically sign in with their Google or Gmail accounts. This way Google can track all your browsing activity and connect to you as a person. This information is then synchronised across all your devices. Do you use an Android smartphone with applications like Google Maps? Then Google knows even more about you instantly. If you value your privacy, Chrome is not the best choice as a browser.
Apple Safari does its job well
Lately, Apple's Safari browser is doing very well in terms of privacy. New features have been introduced into the browser to stop fingerprinting, making it difficult for third parties to follow you. It also has intelligent tracking prevention. This automatically deletes the original tracking cookies that websites place on the Safari browser after seven days. Because of this system, websites can track visitors for a much shorter period of time. Apart from that, Safari offers some useful extensions that improve online privacy. We will return to this later.
Mozilla Firefox: the best and most popular browser for privacy
If you ask us, Mozilla Firefox is the best "normal" browser for users who value their privacy. To begin with, Firefox has several security features, such as protection against phishing and malware. Aside from that, Firefox users are automatically warned every time a website tries to install add-ons. When it comes to privacy, Firefox is a very safe choice, because it also offers useful extensions that protect users against all kinds of tracking and privacy violations. These add-ons are very often specifically for Firefox.
Unlike most other browsers, Firefox is open source. This means that anyone can view the code that makes up Firefox software. Because of this transparent way of working, Mozilla could not create tracking functions, nor would it want to. Someone would notice and show it, which would be terrible for Mozilla's reputation.
Next level anonymous navigation: the Tor browser
If you really want to browse anonymously, the Tor browser could be an interesting option. Tor (the onion router) is an online network for encrypted and anonymous communications. Tor works in much the same way as other browsers such as Firefox, Safari or Chrome. However, unlike other browsers, Tor allows you to browse completely anonymously. The Tor network consists of thousands of servers around the world. All the data traffic that passes through it is cut into small pieces that are then encrypted and sent through various servers before reaching their destination. This process costs time and so the Tor browser can be relatively slow. But no matter how slow it is, it makes sure that no one can see what you're doing when you're browsing.
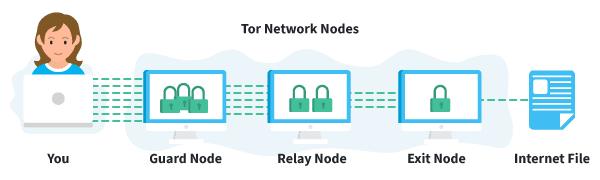
One important thing to keep in mind about using Tor is that it only encrypts part of what you do online. It only protects the Internet traffic that passes through your browser. Services like Skype and WhatsApp access the Internet without using a browser. In this case, Tor cannot offer you protection.
Another thing worth mentioning is that Tor provides users with access to the dark web. Navigating the dark web must be done very carefully. This 'dark side' of the Internet is not regulated, which means that it carries many risks to your safety. For example, it is very easy to find malware. Therefore, for most of us, using a VPN together with the Firefox browser is a better, easier, and safer alternative.
Tip 3: Anonymous Proxy Browsing
The use of a proxy server also provides some anonymity when connected. When you use a proxy, a request for information is sent to that proxy server, which then sends it to the correct web. The site will only be able to see the proxy server's IP address and not yours. A proxy does not have the same level of encryption as a VPN. Although the websites you visit will not be able to see directly who you are, your IP address and online traffic are much easier to decode than if you used a VPN. Third parties will still be able to see what you do. The only thing that prevents them from knowing your identity is the IP of the proxy. This is why proxies do not protect your connection.
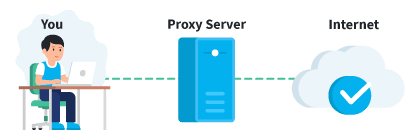
Proxy servers are seen as simpler and free alternatives to a VPN. They may suit your needs, but keep in mind that they do not have the same security standards as a VPN.
Tip 4: Use an anonymous search engine
There is also the option of using an anonymous search engine. DuckDuckGo is probably the best known anonymous search engine. Anonymous search engines, such as DuckDuckGo, are alternatives to Google, Bing, Yahoo and other search engines that like to collect and use your data. When you use DuckDuckGo, the search terms and links you click on are not tracked. In addition, the sites you visit will not be able to see which search terms you used. However, they still know that you have visited their site. This is recorded via your IP address. With DuckDuckGo you can search the Internet more anonymously than with a normal search engine, but it cannot offer you complete anonymity or privacy.
DuckDuckGo does not have the same budget and staff as large companies like Google. This means that the search results it displays will not be as optimised. However, some say that this is actually good for those who focus on privacy. After all, DuckDuckGo shows everyone who enters the same keywords the same search results. Google, by contrast, adjusts its results to your user profile. DuckDuckGo's inaccuracy therefore shows that it really does live up to its promise of anonymity. Our advice is to try DuckDuckGo to see if you like it.
A second anonymous search engine is Startpage. This is a privacy-friendly search system that gets its search results from Google, but does not track them. We also recommend that you try it out.
Tip 5: Minimize tracking with the right browser extensions
There are many browser extensions to help increase your privacy and security online. These extensions are usually easy to install and use. In addition to an ad blocker, a password manager and a VPN browser extension, you can also try specific add-ons and extensions that minimize tracking.
Privacy Badger and Ghostery
Privacy Badger and Ghostery are extensions that detect and block third-party tracking cookies that are stored on your computer while you are browsing. By blocking these cookies you prevent third parties from tracking you online. Did you install Privacy Badger or Ghostery and visit a site that tries to install third party tracking cookies? Then these extensions come into play. Good for you, bad for online retailers, and very good for your privacy.
Tip 6: Watch out for Facebook and Google
Facebook is known to share its users' personal information with advertisers. This is why women tend to have feminine hygiene ads on their Facebook feed while men do not. However, Facebook takes this practice much further: they also keep track of what you do when you are not on their website. If you have been looking for car insurance online, you will most likely see a related ad in your Facebook feed. Facebook allows you to change this slightly in your account's privacy settings. After you have changed this setting, they may no longer show selected ads, but you will still see ads. In addition, they will continue to collect information about you. It is not possible to disable their tracking through their own services, you can only slightly modify what appears in your news feed.
Google also allows you to disable ad personalisation. Again, this doesn't mean that all ads disappear, or that Google stops tracking your data traffic. As a rule, these large companies that rely on advertising revenue will not stop crawling us, unless we make it impossible, for example, via a VPN connection.
Conclusions
There are several steps you can take to better protect your privacy and security online. Do you want to surf the Internet anonymously? Then these are the tips we would like to give you:
- Use Mozilla Firefox or Tor as your browser
- Use a VPN
- Use an anonymous search engine
- Minimize tracking with the right browser extensions
If you combine these tips, your privacy on the Internet will be much more protected. You will be able to surf the Internet completely anonymously. Using a proxy is also an option, but it is quite unnecessary if you are already using a VPN (which is also a better alternative).
Folder vector created by stories - www.freepik.com

