Today, many users wonder what tools hackers use to look for different vulnerabilities on devices that are connected to the Internet. Normally, everyone uses specific tools, but there are search engines that are specifically designed for security researchers.
Although many users think that a hacker is a hacker, the reality is quite the opposite, since most of them are dedicated to investigating and finding security flaws so that later, the affected companies and even themselves can offer a solution in this respect. Several of the tools they use to see the attacks that occur are the following search engines:
1. Censys
Censys is a payment tool where we can see the attacks suffered by different computer systems and applications in real time. Censys also has a free domain search engine where you can access and see different information about the domains, such as which ports and protocols they use, and which certificate is valid. It also has a certificate search engine where we can see if it is valid and which key is the last valid.
It also has an IPv4 address search engine where we can find different relevant information, as well as the approximate location of the IP address. Finally, one of the most interesting payment options is to be able to see how a detected security breach has been resolved. If you want more information you can enter the official website of Censys.io where you have all the details about this tool.
Let's see what kind of information Censys provides and how we can interact with it. Censys collects data from computers and websites through daily scans with ZMap and ZGran about IPv4 address space. At the end with Censys we have regular snapshots of how the computers and websites are configured. As I mentioned before, you can interact through:
- Search engine on the website.
- API for plugin integrations.
- Downloading in "Raw data" mode the databases
The latter are quite large JSON files and, for example, in the case of my talk I downloaded a file of more than 4.3 GB, representing all IPv4 machines with port 21 open and with banner grabbing done on the machine.
We can find much more information about the architecture on which Censys is mounted and its functionalities in the paper that its authors published. From the web frontend and the API you can access different elements, Google Datastore, Elastic Search and Google BigQuery. Another option, mentioned above, is the download of raw information through compressed files that host a JSON.
Like Shodan, it has various tools that add intelligence to the data collected, such as the possibility of discovering public exploits for certain hosts under certain conditions. Censys presents several tools to analyze the information that has been previously collected.
Censys is an interesting source of information that, as we have seen, provides different mechanisms to "play" with the information and build interesting things, like applying intelligence on the data and crossing it with public exploits to "conquer the world". Of course, if you are responsible for security in a company, it is a useful source to see what any potential attacker might be collecting from your infrastructure.
2. Shodan
Shodan is a free web service that allows us to see what devices have access to the Internet, and if they have any security flaws. This service is ideal, for example, to see if there are webcams, Smart TV, air conditioning, alarms and other devices in the digital home connected to the Internet and vulnerable to different types of attacks.
Shodan is one of the most popular and used search engines, as it provides us with a large amount of information, and allows us to see in detail if there is any type of security flaw in our device, or what information it has about our public IP address.
3. Greynose
Greynose has a search engine where you can enter an IP address and also search for words. Depending on what we have entered, it will show us information about attacks, malicious websites or faults it finds. It also has a section in the lower right side of the search bar, called "explore trends" where we can see different statistics updated in real time, such as anomalies detected in different ports, malicious attacks, etc.. To access this functionality you can do it from the following link.
All this is free, but if we want more accurate information such as IP lookup, more advanced queries, or support, we must buy the payment option for companies that is worth 2,999.
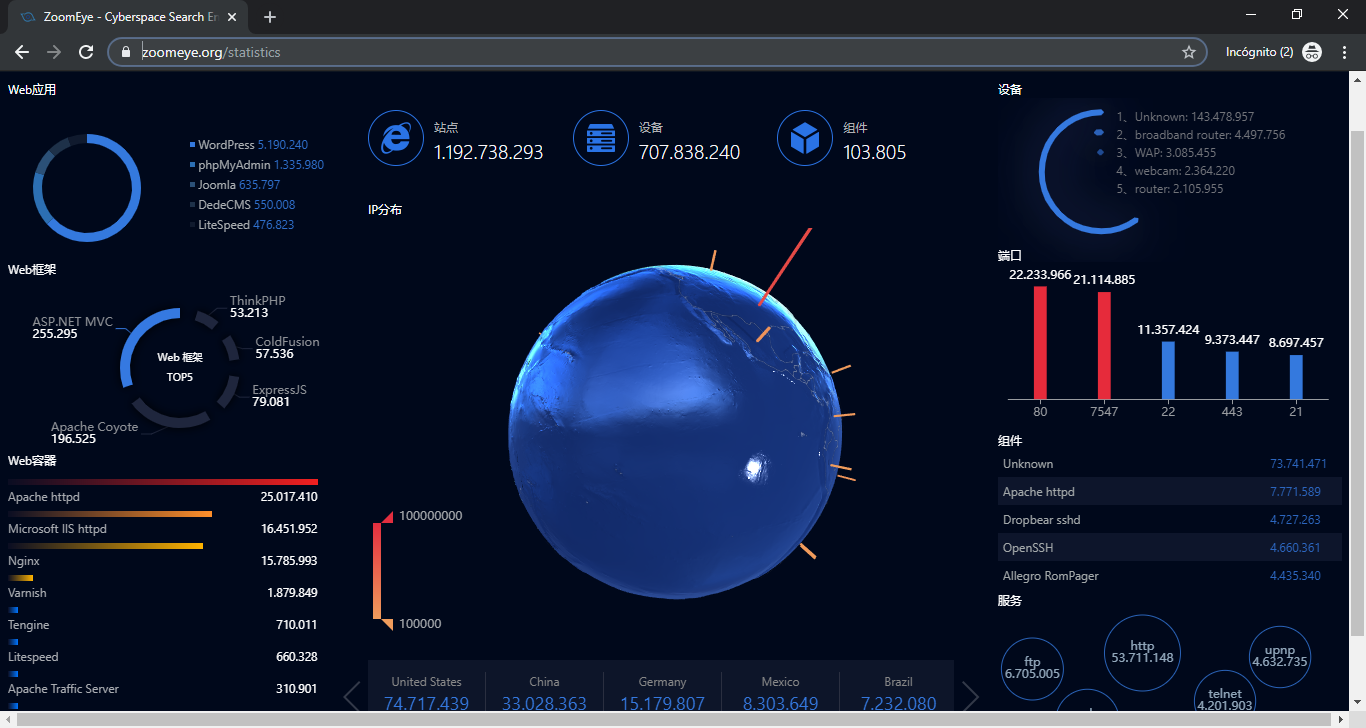
4. Zoomeye
Zoomeye is very similar to Greynose but is developed for the Chinese market. It has a search engine where entering IP addresses, a word, etc. will show us information about it. As it is in Chinese, we recommend that you use it with a translator, because although the information of the results will be shown in English, the menus and some data will not.
Zoomeye also has a very interesting section called statistics, where we can see different statistics of the entire planet of all kinds, from countries, browsers, servers, protocols, etc.. If you want to access this function you can do it from the following link.
5. Wigle
Wigle is a search engine for wireless networks by coordinates. In other words, when we enter Wigle we find a map, and to the right we can enter latitude and longitude coordinates to go some point on the planet Earth. If we zoom in we will be able to see the different hotspot networks that are available in the place. There are also Wi-Fi devices, Bluetooth, and telecommunications antennas. Of course it can be very useful to see what surrounds us and if we have any network available nearby. You can access to Wigle in the following link.
6. Publicwwww
Publicwww is a web that through a search engine allows us to search for HTML, JS and CSS code in any web page. Actually its use is very simple, but it can be very useful. The operation of Publicwww is very simple. Once we enter your website, we must enter in the search box, the code we want to find out if it is on any website. Once introduced we must click to the right in the bar where we have introduced the code, the button "Search", and it will show us the results found.
If we want to know what syntax we can enter in the search box, we must click below, where it says in blue "query syntax: RegEx, ccTLDs, etc." and we will open a new page, with the different ways in which we can search the code. We enclose some screenshots where you can see examples.
7. Hunter.io
Hunter.io is a website where we have a search engine where we can enter the name of a company, and show us all email addresses that have filtered on that company. This website can be useful if we need to find an email address. The operation of Hunter.io is very simple. Once we enter your website, we must enter in the search box, the name of the company we want to find out if any email address has been filtered. Once introduced we must click to the right in the bar where we have introduced the direction of email, the button "Find email addresses" or when we introduce the name of the company can appear already in the searcher.
Once clicked if it doesn't find anything, the message will appear below the following search box "This doesn't look like a domain name". On the other hand, if you find any result, we will see the email addresses found and next to a green icon if they are still active or yellow if you do not know. In addition, we will also appear on the right side of each email address found, a downward arrow that tells us which website has found the email of the company we are looking for and tells us whether or not the place where you found it is still active.
8. Haveibeenpwned
Haveibeenpwned allows us to find out if by means of the address of our electronic mail some password of some web page has been filtered. We recommend that you try this website, especially because of the leaks and theft of information in recent years. The operation of Haveibeenpwned is very simple. Once we enter your website, we must enter in the search box, the email address we want to find out if any website has filtered the password. Once introduced we must click to the right in the bar where we have introduced the direction of email, the button "pwned".
If you don't find that your email address is filtered, we'll see below the green and white search bar the following text, "Good news - no pwnage found! On the other hand, if you find that our email address has been filtered, the following text, "Oh no - pwned!" will appear in red and white.
In the event that we happen to this filtering, the first thing we must do, is change the password of the email. Next, in this web if we download below the whole web site, it will indicate us where it has found that it has filtered our email address and password. This website can save us from a good problem of improper access, so from RedesZone we recommend that you test your email addresses to see if they have been filtered.
9. OSINT Framework
OSINT Framework is a web that through the use of different menus, we can find links to different websites about the information of the category we are looking for. When we enter the OSINT Framework website we find on the left side a series of subcategories, which we will see next, where we try to follow the different options, according to what we want, and, at the end, leads to a series of results, which clicking on them will open a new tab with the search engine we have selected. We have to bear in mind that, if we click on the blue ball, another submenu will be opened, on the other hand, if the ball is white, the selected web will be opened to us.
The different submenus that we can choose are the following ones:
Username: Within the section "username" we have other subcategories, such as "username search engines" or "specific sites". Selecting one of these subcategories allows us to further narrow down the available services we have for searching user names.
Email Address: Within the section "email address" we can choose between the different subcategories "email search", "common emails formats", "email verification", "vreach data", "spam reputation lists" and "mail blacklist". Selecting one of these subcategories allows us to further narrow down the services we have available to search for email addresses.
Domain Name: Within the section "domain name" we can choose between the different subcategories "whois records", "subdomains", "Discovery", "certificate search", "passiveDNS", "reputation", "domain blacklists", "typosquatting", "analytics", "url expanders", "change detection", "social anaysis", "DNSSEC", "cloud resources", "vulnerabilities" and "tools". Selecting one of these subcategories allows us to further narrow down the available services we have to search for any data on domain names.
IP Address: Within the section "IP address" we can choose between the different subcategories "geolocation", "host / port discovery", "IPV4", "IPV6", "BGP", "reputation", "blacklists", "neighbor domains", "protect by cloud services", "Wireless network info", "network analysis tools" and "IP loggers". Selecting one of these subcategories allows us to further narrow down the available services we have to search for any IP address data.
Images / Videos / Docs: Within the section "images, videos and docs" we can choose between the different subcategories "images", "videos", "webcams", "documents" and "fonts". Selecting one of these subcategories allows us to further narrow down the available services we have to search for any data on the above mentioned files.
Social Networks: Within the section "social networks" we can choose between the different subcategories "Facebook", "Twitter", "Reddit", "LinkedIn", "other social networks", "search" and "social media monitoring wiki". Selecting one of these subcategories allows us to further narrow down the available services we have to search for any data on the selected social networks.
Instant Messaging: Within the section "instant messaging" we can choose between the different subcategories "Skype", "Snapchat", "KiK" and "Yikyak". Selecting one of these subcategories allows us to further narrow down the available services we have to search for any data about the selected instant messaging networks.
People Search Engines: Within the section "people search engines" we can choose between the two different subcategories "general people search" and "registries". Selecting one of these subcategories allows us to further narrow down the available services we have to search for any data on the selected category.
Dating: Within the section "dating" we can choose between the different subcategories "match.com", "ayi.com", "plenty of fish.com", "eharmony", "farmers only", "zoosk", "okcupid", "tinder", "wamba.com", "adultfriendfinder", "Ashley madison", "beautifulpeople.com", "badoo", "spark.com", "meetup", "blackpeoplemeet" and "review of users". Selecting one of these subcategories allows us to delimit or enter the selected website or service.
Telephone Numbers: Within the section "telephone numbers" we can choose between the different subcategories "voicemail", "international", "pipl api", "whocalld", "411", "callerid test", "thatsthem - reverse pone lookup", "twilio lookup", "fonde finder", "true caller", "reverse genie", "spydialer", "pone validator", "free Carrier lookup", "mr. number", "calleridservice.com", "next caller", "data24-7", "hlr lookup portal", "opencnam", "opencnam api", "usphonebook", "numspy" and "numspy-api". Selecting one of these subcategories allows us to further narrow down the available services we have to search for any data about phone numbers.
Public Record: Within the section "public records" we can choose between the different subcategories "property records", "court / criminal records" , "gonvernment records" , "financial / tax resources". birth records" , "death records" , "us country data" , "voter records" , "patent records" , "political records" , "public records" , "enigma" , "the world bank open data catalog" . , "brb public records" , "govdata (german)" and "open.data-portal München". Selecting one of these subcategories allows us to further narrow down the available services we have to search for any public data, it is mostly focused on the USA, although we have some options for other countries such as Germany.
Business Records: Within the section "business records" we can choose between the different subcategories "annual reports", "general info & news", "company profiles", "employee profiles & resumes" and "additional resources". Selecting one of these subcategories allows us to limit information about and for companies.
Transportation: Within the section "transportation" we can choose between the different subcategories "vehicle records", "air traffic records", "marine records", "railway records", "satellite tracking" and "track-trace". Selecting one of these subcategories allows us to delimit information of different categories and methods of transport.
Geolocation Tools / Maps: Within the section "geolocation tools / maps" we can choose between the different subcategories "geolocation tools", "coordinates", "map reporting tools", "mobile coverage", "Google maps", "Bing maps", "HERE maps", "dual maps", "instant Google Street view", "wikimapia", "openstreetmap", "flash earth", "historic aerials", "Google maps update alerts", "Google earth overlays", "yandex....maps", "terraserver", "Google earth", "Baidu maps", "corona", "daum", "naver", "earthexplorer", "openstreetcam", "dronetheworld", "travel by drone", "hivemapper", "landsatlook viewer", "sentinel2look viewer", "nexrad data inventory search", "mapquest", "openrailwaymap", "openstreetmap routing service", "hiking & biking map", "us nav guide zip code data" and "wayback imagery". Selecting one of these subcategories allows us to delimit information from different categories and geolocation services.
Search Engines: Within the section "search engines" we can choose between the different subcategories "general search", "meta search", code search", "FTP search", academic / publication search", "news search", "other search", "search tools", "search engine guides" and "fact checking". Selecting one of these subcategories allows us to narrow down information from different categories and on different search methods.
Forums / Blogs / IRC: Within the section "forums / blogs /IRC" we can choose between the different subcategories "forum search engines", "blog search engines" and "IRC search". Selecting one of these subcategories allows us to delimit and select a service that performs a search on forums, blogs or IRC.
Archives: Within the "archives" section we can choose between the different subcategories "web", "data leaks", "public datasets" and "other media". Selecting one of these subcategories allows us to delimit and select a service that performs a search on files.
Language Translation: Within the section "language translations" we can choose between the different subcategories "text", "pictures" and "analysis". Selecting one of these subcategories allows us to delimit and select a translation service.
Metadata: Within the "metadata" section we can choose between the different subcategories "exiftool", "metagoofil", "seal" and "codetwo Outlook export". Selecting one of these subcategories allows us to delimit and select a service that performs a search on metadata.
Mobile Emulation: Within the section "mobile emulation" we can choose only the subcategory "Android", where within the category "Android" give us the subcategories of "emulation tools" and "apps". Selecting one of these subcategories allows us to delimit and select an Android emulation service.
Terrorism: Within the section "terrorism" we can only choose the subcategory "Global Terrorism Database". Selecting this category allows us to access a database on terrorism.
Dark Web: Within the section "dark web" we can choose between the different subcategories "general info", "clients", "discovery", "TOR search", "TOR directories", "TOR2web", "web or proxy" and "IACA dark web investigation support". Selecting one of these subcategories allows us to delimit and select a service or information about the dark web.
Digital Currency: Within the section "digital currency" we can choose between the different subcategories "bitcoin", "Ethereum" and "monero". Selecting one of these subcategories allows us to access different services and websites on the selected digital currency.
Classifieds: Within the section "classifieds" we can choose between the different subcategories "craigslist", "kijiji", " quikr", " ebay", " offerup", " goofbid", " flippity", "searchalljunk", " totalcraigsearch", " backpage", " search tempest", " oodley" and "claz.org". Selecting one of these subcategories allows us to access different classification services.
Enconding / Decoding: Within the section "enconding / decoding" we can choose between the different subcategories "base64", "barcodes / QR", "javascript", "PHP", "XOR", "cyberchef" and "functions online". Selecting one of these subcategories allows us to access different services and programming websites.
Tools: Within the section "tools" we can choose between the different subcategories "osint automation", "pentesting recon", "virtual machines", "paterva / maltego", "epic privacy browser" and "overview". Selecting one of these subcategories allows us to access different tools.
Malicious File Analysis: Within the section "malicious file analysis" we can choose between the different subcategories "search", "hosted automated analysis", "office files", "PDFs", "pcaps", "ghidra" and "malware analysis tools". Selecting one of these subcategories allows us to access different analysis tools for malicious files.
Exploits & Advisories: Within the section "exploits & advisories" we can choose between the different subcategories "default passwords", "mitre att&ck", "exploit DB", "packet storm", "securityfocus", "nvd - nist", "osvdb", "cve details", "cve mitre", "owasp", "0day.today", "secunia" and "Canadian centre for cyber security". Selecting one of these subcategories allows us to access different tools and websites for analysis of exploits.
Threat Intelligence: Within the section "threat intelligence" we can choose between the different subcategories "phishing", "ioc tools", "ttps", "ibm x-force exchange", "malware information sharing platform", "malware patrol", "project honey pot", "cymon open threat intelligence", "mlsecproject / combine", "hostintel - keithjones github", "massive-octo-spice - csirgadgets github", "bot scout", "blueliv threat exchange", "aptnotes", "honeydb", "pulsedive" and "mr.looquer ioc feed - 1st dual stack threat feed". Selecting one of these subcategories allows us to access different information websites.
OpSec: Within the "opsec" section we can choose between the different subcategories "persona creation", "anonymous browsing", "privacy /clean up" and "metada /style". Selecting one of these subcategories allows us to access different opsec tools and websites.
Documentation: Within the "documentation" section we can choose between the different subcategories "web browsing", "screen capture", "map locations" and "timeline js3". Selecting one of these subcategories allows us to access different documentation.
Training: Within the section "training" we can choose between the different subcategories "games", "automatingosint.com", "open source Intelligence techniques", "plessas", "sans sec487 osint class", "netbootcamp", and "smart questions". Selecting one of these subcategories allows us to access different training sites on the selected topic.
As you can see OSINT Framework, it would be more Wikipedia style, for the amount of menus and categories it offers, to be able to find almost any category of what we are looking for. Without a doubt we recommend that you try it.