DNS services are essential for web browsing. However, it is one of the most vulnerable to attacks. This guide will detail the most dangerous DNS attacks and some actions that will protect the network infrastructure.
One of the reasons why DNS services have some susceptibility to attack is the UDP transport layer protocol. Remember that this is a connectionless transmission protocol. The latter means that it is not connection-oriented, the UDP protocol does not care if the data reaches its destination completely, it will still continue to transmit everything it has in queue. Let's say that the data packets are on their own, they may arrive successfully or suffer from some inconvenience in the middle. Let's look at the following scheme for more understanding:
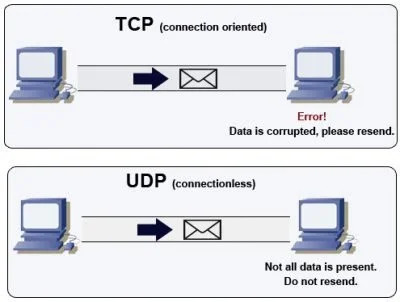
- The first half of the image shows us how another popular protocol which is connection oriented works: TCP. It does not accept corrupt data packets or packets with any integrity problem. Yes or yes they must be sent again to reach their destination 100%.
- The other half refers to UDP. As mentioned, it is not connection-oriented. The destination will receive the data packets regardless of whether they are in trouble or not.
Think about streaming services. These, at certain times, stop and then resume transmission. Either the image is somewhat pixelated or you hear the famous "robotic voice" of the speaker. Even though all this may happen, the transmission does not stop by itself. Of course, there are exceptions such as no Internet connectivity or the person running out of battery or power.
The most powerful DNS attacks
DNS Cache Poisoning
It's one of the most frequent attacks. The main purpose is to capture users through fake and malicious websites. How is it possible that a DNS server returns suspicious sites to us in order to appropriate our personal data? Below, we show you a diagram of how it works and explain it step by step.
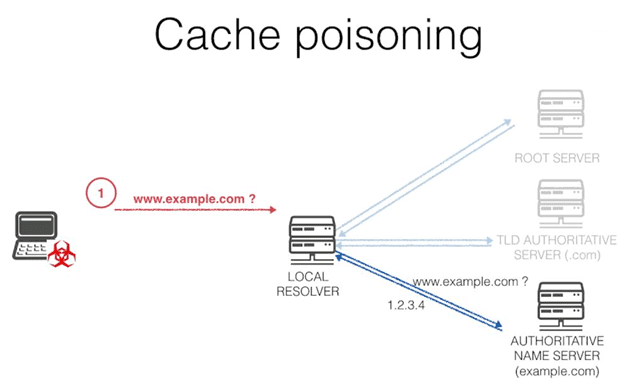
Imagine that you want to access mail.google.com (Gmail), almost without realizing it, a poisoned DNS redirects us to a site quite similar to Gmail where it asks us for our username and password. As we can see, DNS Cache Poisoning is one of the most effective bridges to other well known attacks such as phishing. This attack shows us how easy it is to break the DNS records of a particular server to redirect users to websites that they don't really want to access.
How to prevent and mitigate this attack
Here are three measures that will help prevent DNS Cache Poisoning:
One of the essential measures is to configure the DNS servers so that they trust other DNS servers as little as possible when relating to each other. In this way, cybercriminals will be less likely to alter the settings and DNS records of the servers they are targeting.
Other configuration actions include: restricting recursive queries, storing data that is only associated with the requested domain, and restricting queries to information that only comes from the requested domain.
The use of the DNSSEC tool which is intended to provide reliable DNS data authentication. One of the advantages of DNSSEC is that it is possible to limit the number of DNS requests. It is also possible to prevent other important attacks such as DDoS.
Botnet-based DNS attacks
Keep in mind that with a small botnet, there are multiple possibilities for attacks. Not to mention if you have more than one, and each one has thousands of zombie computers. Basically, the attack based on these networks of connected and infected computers consists of running DDoS.
A single botnet would be large enough to render a regular DNS server unusable. Simply put, each zombie must be "programmed" to send multiple access requests to a web resource recognized by that DNS server. Then, that server will be saturated by so many requests, cannot answer them and therefore, stops operating.
Botnet-based attacks can be prevented by applying a few actions that, in the long term, will prevent one or more eventualities:
Checking your networked devices for vulnerabilities.
Do you have IoT devices in your network? Check the security settings as soon as possible.
Are there threats of DNS attacks? It is essential to have IDS/IPS security solutions to identify them and act accordingly.
DNS Flood Attacks
The main goal is to overload the DNS server so that it cannot continue to handle DNS requests because all the DNS zones in question influence the purpose of the resource records.
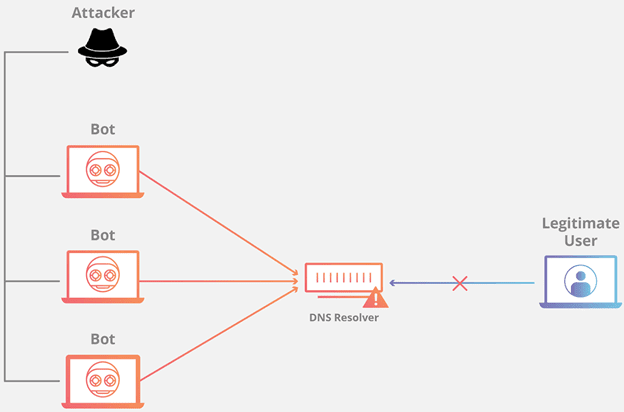
As can be seen in the diagram above, an attacker creates a botnet with many computers acting as zombies, infected of course, with the clear purpose of attacking the DNS server with thousands of requests. This is probably the most recurrent case of a DoS attack.
This type of attack is usually controlled in a simple way because usually the origin comes from a single IP address. However, the situation becomes much more complicated if it becomes a distributed DoS, i.e. a DDoS.
Poisoning Cache
This attack is one of the most effective ways for users to become victims of phishing attacks. Because users, being certain that they are entering a legitimate website, are actually accessing one that has the task of collecting all your data. Especially access credentials and bank details.
Let's suppose you want to enter your bank's website and, without paying too much attention, you see that you have actually accessed the official page. Apparently, everything looks the same and there is nothing to worry about. However, you enter your access data and at a certain point, you realize that something is wrong.
But what is DNS caching? It is a process in which a DNS server is involved to resolve. Its function is to store the answers to DNS requests for a certain time. This serves to respond to all DNS requests much more quickly, without going through the whole process of resolving domain names.
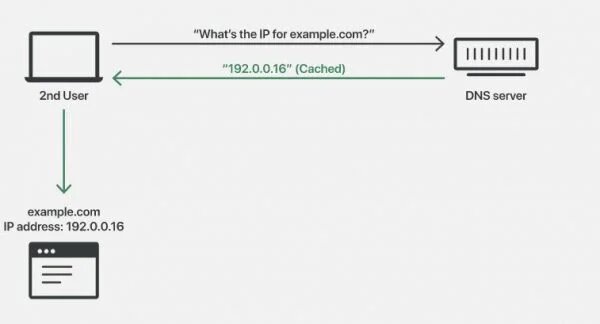
Unfortunately, a cybercriminal can gain control of the DNS by resolving and altering the responses to all the DNS requests he has stored. For example, if the site www.ejemplo.com is originally associated with the IP 192.0.0.16, the cybercriminal can alter that response by associating the domain with a malicious IP: 192.0.0.17
And so, without realizing it, the user accesses a malicious site even though he has entered a legitimate domain. As a web services administrator, you should implement the following:
-- Restrict recursive queries.
- Store DNS records associated only with domain names.
- Limit responses to DNS requests to the information actually associated with the domain.
DrDoS (Distributed Reflection Denial of Service Attack)
This is further evidence that DDoS attacks can be on a large scale. The servers that act as reflectors in this variant of DDoS could belong to different networks. The advantage for the attacker is that it becomes very difficult to track the attack scheme afterwards.
Consequently, multiple networks can be involved in a DrDoS attack. If I have three reflector servers belonging to three different networks, the cybercriminal could take control of these three networks so that all connected devices participate in the attack.
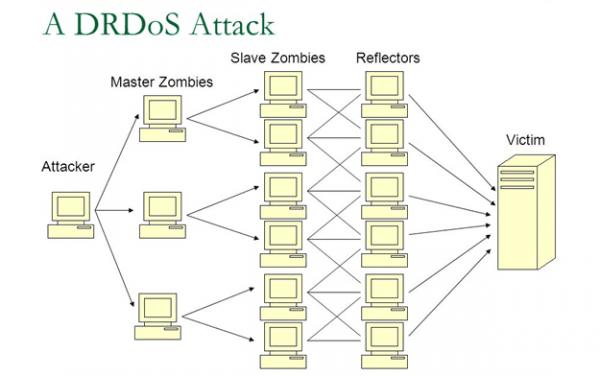
Let's pass this on to the DNS context. If there are multiple devices connected from several networks, and all of these networks have reflector servers, the reflector servers will not be affected by the large number of DNS requests passing through them. It is precisely this feature of reflectors that makes them directly redirect the large number of requests to the victim DNS server.
The affected server will receive as many illegitimate requests, along with the legitimate ones. As its capacity has reached its limit, it will start discarding packets including those corresponding to legitimate requests. Therefore, it stops responding.
How to prevent and mitigate this attack
Although it is very difficult to mitigate a DRDoS, there are prevention measures that, in the long term, will protect you from this type of situation. Especially at the organizational level:
Make sure that your servers (including DNS) are located in different data centers, as well as being part of different networks/subnets in the organization.
Data centers should also have several alternative access routes in addition to the main one.
Most importantly, both the data centers and the related networks/subnets must not have security holes of any kind of impact level.
What can be done to prevent such a large-scale attack?
All the prevention measures suggested so far, apply. However, if the network infrastructure you are managing is large, it is not out of the question to consider the following:
- Multiple servers must be located in more than one data center.
- Data centers must belong to different network segments.
- Ensure that data centers have multiple paths.
- Have little or no security holes.
Phantom Domain Attack
DNS resolvers are attacked and resource use is abused to try and resolve just such phantom domains. In reality, no matter how many times you try, they will never be resolved. What cybercriminals seek to achieve is that these resolvers wait for a response for a very long time, which results in performance failures of DNS services or quite a deteriorated performance.
Below is a list of measures you can apply to prevent/mitigate this type of attack:
- Increase the number of recursive clients
- Restrict recursive requests by each server, as well as restrict requests (inquiries) by zone.
Random Subdomain Attack
Although it is not one of the most popular attacks, it is quite difficult to identify. So we recommend that you pay attention. It is quite similar to DoS attacks by its nature and scheme of operation. This attack is carried out by sending many DNS requests to an active domain. However, these malicious requests do not originate from the main domain, but rather from those sub-domains that do not currently exist.
It is an attack on sub-domains, but eventually succeeds in carrying out an embedded DoS attack that causes the DNS server to be down and its DNS lookups down. Since it receives too many requests and gets saturated when trying to resolve the main domain.
Impact of DNS attacks
DNS attacks cause great harm to the various organizations that are victims of them. The sums of money that are the result of the losses easily reach millions of dollars. What is most worrying is that DNS attacks tend to be increasingly sophisticated and specific to the modus operandi.
Insider-type threats are the order of the day. Organizations, although they seem to be less susceptible to DNS attacks, must protect their infrastructure from insiders using the Threat Intelligence tools that are fortunately available. On the other hand, security tools for web service management also have many options.
DNS attacks, although they have been carried out for many years now, do not stop growing in terms of the number of events that occur each year. While your organization will probably never fall victim to any of these attacks, protecting your network infrastructure is not an option
Technology vector created by freepik - www.freepik.com

