When you install an application on your smartphone, you decide what permissions you give it, but it's not always clear. We tell you how to know if those permissions are too much...
Smartphones have become the target of choice for hackers and criminals who want to make money or extort money from you by obtaining data or information about you or by using your smartphone for their own profit. In some cases, they are simply doing it to pass the time.
But it's not something we should worry about any more than when we access the computer. With some precautions and security measures, our smartphone and the content we store will be safe from unexpected access.
One of the things that cause most distrust and fear is the unauthorized access to items on your smartphone such as the location, microphone and camera. In the first case, because they can know where we are and where we are going during the day. No one likes to be spied on while talking to someone.
However, the functions mentioned are very useful. What would become of the current maps without the possibility of locating us on the map? Video calls would not be possible without access to the microphone and camera. In addition, without the microphone, it would not be possible to make calls.
As a precaution, for years both Apple's iOS and Google's Android have asked you what permissions you're going to give to a certain application before installing it on your smartphone. It also lets you know when it's going to be updated, if it adds or changes those permissions, and allows you to change the permissions at any time.
Location, microphone and camera on Android
Let's start with Android, the most popular platform and the one that suffers the most attacks in the form of malicious applications or malware available for Android. Although the latest versions of Android have a tool that analyzes applications to make sure they're safe, Google Play Protect, it doesn't hurt to check the permissions we give to apps ourselves from time to time.
On Android, permissions can be checked from several sites. Location, for example, is available in Settings > Location, where you can disable access to your map location for all apps and Android and review application permissions from Application Permission. In that list, you'll see which apps can always access your location, which can only do so when you're using them, and which have no access to your location or are denied.
Another way to access location permissions, in addition to microphone and camera related permissions, is to go to Settings > Privacy > Permissions Manager. Among other options you will see the ones that interest us, Camera or Microphone. As well as Location, you'll see which apps always have access, those that are only accessed while in use, and those that can't be accessed. At any time you can select an application and change its permissions.
Location, microphone and camera in iOS
In the operating systems of your iPhone and iPad, iOS and iPadOS respectively, the process for accessing the permissions you have granted to your applications is similar to Android, so it is not lost.
From Settings > Privacy you'll see all the possible permissions. When you access each one, you'll see which applications have permission and which don't, along with other options, as appropriate. Furthermore, you can revoke your authorisation at any time or grant authorisation if you do not have it.
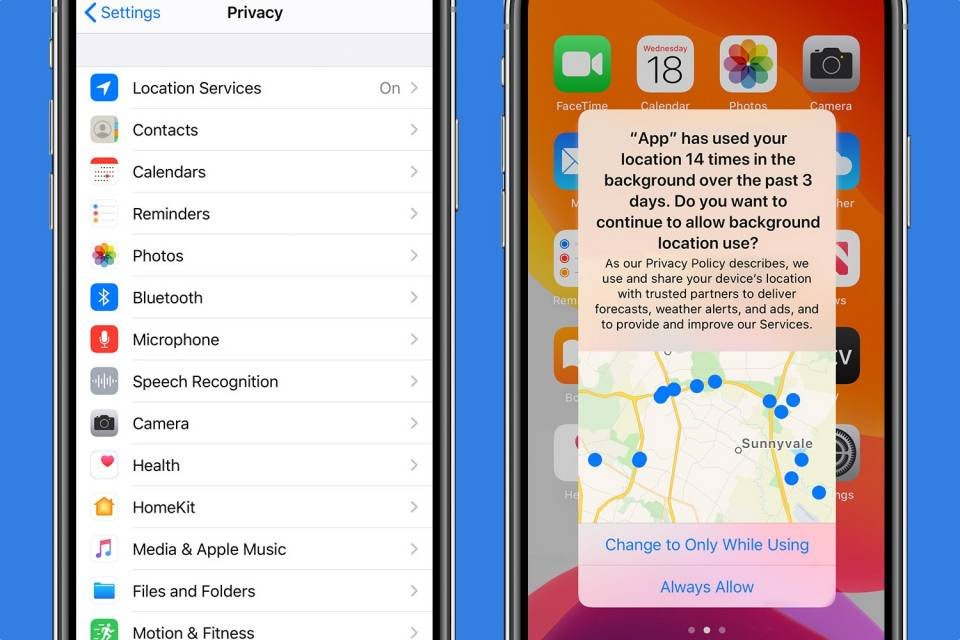
In Location, you'll see which applications can ask your iPhone or iPad where you are from the built-in GPS or using mobile or Wi-Fi connections. Otherwise, Microphone and Camera do the obvious.
In all permissions, apps can have constant access - only if you're using them or never. And when you first open an app, it may ask you for a specific permission. You can give it forever, deny it, or give it only once.
Technology vector created by stories - www.freepik.com

