243 results for: internet
Transitioning from a Home Office to a Virtual Office
Category : Web marketing 08-03-2024 by Janeth Kent
The Payment Request API: Revolutionizing Online Payments (Part 1)
Category : Javascript 12-06-2023 by Silvia Mazzetta
Android Hidden Codes: unveiling custom dialer codes and their functionality
Category : Mobile 02-06-2023 by Janeth Kent
How to download an email in PDF format in Gmail for Android
Category : Technology 16-05-2023 by Janeth Kent
The first videogame tournaments: the origin of eSports
Category : Videogames 19-10-2022 by Janeth Kent
8 benefits of having a website for your business
Category : Web marketing 03-06-2022 by Nadal Vicens
JavaScript Arrow functions: What they are and how to use them
Category : Javascript 30-08-2021 by Janeth Kent
Why E-Commerce Businesses Should be Using Cloud Computing
Category : Web marketing 01-06-2021 by Silvia Mazzetta
How to access webcam and grab an image using HTML5 and Javascript
Category : Javascript 20-05-2021 by Janeth Kent
How to set up your Android phone: learn how to get your new phone up and running
Category : Mobile 28-04-2021 by Janeth Kent
5 Terrific iOS-Friendly Canva Alternatives to Upgrade Your Marketing Visuals
Category : Web marketing 05-05-2021 by Janeth Kent
How To Use Varnish As A Highly Available Load Balancer On Ubuntu 20.04 With SSL
Category : Servers 25-04-2021 by Janeth Kent
How to hide the you are typing text in a WhatsApp group
Category : Social networks 25-03-2021 by Janeth Kent
Top Graphic Design e-Books & How to Get them on Your iDevice
Category : Ui/ux design 03-03-2021 by Luigi Nori
htaccess Rules to Help Protect from SQL Injections and XSS
Category : Security 01-03-2021 by Janeth Kent
Cybersecurity and Data Privacy: Why It Is So Important
Category : Security 26-02-2021 by Janeth Kent
Interesting and Helpful Google Search Features You’ll Want to Start Using
Category : Software 31-01-2021 by Iveta Karailievova
Deepfakes Detection – An Emerging Technological Challenge
Category : Technology 27-01-2021 by Iveta Karailievova
How to have two WhatsApp accounts on your Dual SIM phone
Category : Software 25-01-2021 by Luigi Nori
A FULFILLED PROMISE - Using the FETCH API to make AJAX calls
Category : Javascript 26-12-2020 by Iveta Karailievova
Dark Web: the creepy side of the Internet is not as dark as believed
Category : Security 17-05-2023 by Silvia Mazzetta
Some Neat Ways to Improve Your Internet Browsing Experience?
Category : News and events 21-12-2020 by Janeth Kent
Website Traffic Getting Low? 4 Immediate Action to Take
Category : Web marketing 04-12-2020 by Luigi Nori
The BleedingTooth vulnerability and other Bluetooth security risks
Category : Security 10-11-2020 by Iveta Karailievova
The best tricks and features to master your Android Smart TV
Category : Networking 05-11-2020 by Luigi Nori
3 awesome ways technology is helping us combat the COVID pandemic
Category : Technology 28-10-2020 by Iveta Karailievova
How to Unlock Secret Games in Chrome, Edge and Firefox
Category : Videogames 26-07-2025 by Silvia Mazzetta
Jennifer in Paradise: story of the first photo ever edited in Photoshop
Category : News and events 25-09-2020 by Silvia Mazzetta
Data Scraping and Data Crawling, what are they for?
Category : Web marketing 25-09-2020 by Silvia Mazzetta
How to securely access the Dark Web in 15 steps. Second part
Category : Security 08-03-2024 by Janeth Kent
How to securely access the Dark Web in 15 steps. First part
Category : Security 08-03-2024 by Silvia Mazzetta
How to install a Linux partition on a Windows 10 PC
Category : Operating systems 06-09-2020 by Luigi Nori
What cybersecurity professionals have learned from the lockdown experience
Category : Security 26-08-2020 by Silvia Mazzetta
5 Remote Careers You Can Start Online in 2020
Category : News and events 25-08-2020 by Silvia Mazzetta
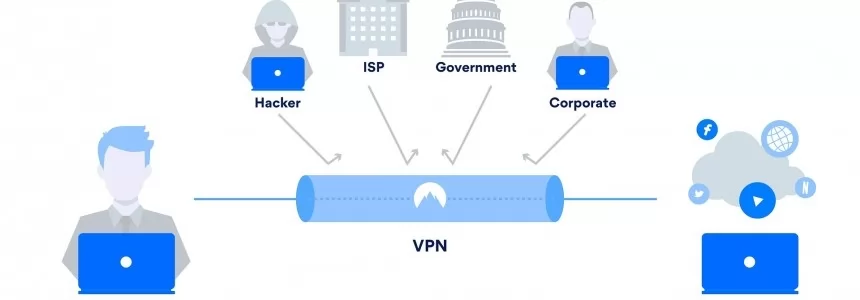
Browse safely and privately from your mobile phone using a VPN
Category : Security 25-08-2020 by Janeth Kent
Get ready for the future: What Does The Future Of SEO Look Like?
Category : Seo 19-08-2020 by Silvia Mazzetta
The 6 Essentials for Creating a Visually Appealing Web Design
Category : Web design 25-08-2020 by Silvia Mazzetta
How to configure Tor to browse the deep web safely
Category : Security 12-08-2020 by Silvia Mazzetta
How to integrate native images lazy loading in your web projects
Category : Programming 03-04-2023 by Luigi Nori
Why is Website Performance Important for Online Businesses?
Category : Web marketing 24-07-2020 by Janeth Kent
Parenting, pandemic and UX: Learning from design of experiences
Category : Ui/ux design 17-06-2020 by Silvia Mazzetta
How to get notified when one of your WhatsApp contact is online
Category : Software 15-06-2020 by Silvia Mazzetta
Why do you vote the way you do in the age of misinformation and fake news?
Category : News and events 11-06-2020 by Silvia Mazzetta
How to move Chrome, Firefox or Edge cache to save space
Category : News and events 04-06-2020 by Janeth Kent
Onion Search Engine: How to browse the Deep Web without Tor
Category : Security 25-05-2020 by Janeth Kent
How to turn your smartphone into a webcam for your pc
Category : Multimedia 17-05-2020 by Luigi Nori
Seo: How Search Behavior Has Changed During COVID-19 Pandemic
Category : Seo & sem 08-05-2020 by Silvia Mazzetta
How to get into the Deep Web: a guide to access TOR, ZeroNet, Freenet and I2P
Category : Security 07-05-2020 by Janeth Kent
Web shells as a security thread for web applications
Category : Security 04-05-2020 by Iveta Karailievova
How To Effectively Learn Coding For Website Development
Category : Programming 21-04-2020 by Luigi Nori
Facebook: how to remove hidden data and personal information
Category : Social networks 20-04-2020 by Silvia Mazzetta
The best websites of the Tor Deep Web and Dark Web Network
Category : Security 03-11-2022 by Janeth Kent
How to find everything you need on the Deep Web and the Dark Web
Category : Security 10-05-2021 by Silvia Mazzetta
Best Free Image Optimization Tools for Image Compression
Category : Software 27-03-2020 by Janeth Kent