360 results for: word
How to include a JavaScript file in another JavaScript file
Category : Javascript 25-09-2024 by Janeth Kent
The best and most amazing Alexa Hacks you should know about
Category : Operating systems 30-06-2023 by Janeth Kent
Google Play Games on PC: Transforming Your Gaming Experience
Category : Videogames 06-06-2023 by Janeth Kent
The Payment Request API: Revolutionizing Online Payments (Part 2)
Category : Javascript 08-06-2023 by Silvia Mazzetta
Marketing Trends in Technology 2023: Spotlight on Inflation
Category : Web marketing 01-06-2023 by Janeth Kent
How do you stop JavaScript execution for a while: sleep()
Category : Javascript 31-05-2023 by Janeth Kent
Mastering array sorting in JavaScript: a guide to the sort() function
Category : Javascript 29-05-2023 by Janeth Kent
Is AI sexist? A gender perspective in Robotics and Artificial Intelligence
Category : News and events 22-05-2023 by Silvia Mazzetta
Infinite scrolling with native JavaScript using the Fetch API
Category : Javascript 05-11-2024 by Janeth Kent
A Step-by-Step Process to Using Artificial Intelligence as a Startup
Category : Technology 14-03-2023 by Janeth Kent
Benefits of Corporate Social Responsibility to Business
Category : Web marketing 06-12-2022 by Janeth Kent
8 benefits of having a website for your business
Category : Web marketing 03-06-2022 by Nadal Vicens
Difference between arrow and normal functions in JavaScript
Category : Javascript 30-08-2021 by Janeth Kent
JavaScript Arrow functions: What they are and how to use them
Category : Javascript 30-08-2021 by Janeth Kent
What is the difference between primitives types and objects in JavaScript?
Category : Javascript 26-05-2023 by Silvia Mazzetta
The ultimate cybersecurity checklist for programmers
Category : Security 02-06-2023 by Silvia Mazzetta
Advanced Android tutorial: discover all your phone's secrets
Category : Mobile 06-05-2021 by Janeth Kent
How to set up your Android phone: learn how to get your new phone up and running
Category : Mobile 28-04-2021 by Janeth Kent
5 Terrific iOS-Friendly Canva Alternatives to Upgrade Your Marketing Visuals
Category : Web marketing 05-05-2021 by Janeth Kent
Elon Musk To Found Starbase, A City In Texas To House His Companies And Projects
Category : Technology 05-03-2021 by Janeth Kent
Cybersecurity and Data Privacy: Why It Is So Important
Category : Security 26-02-2021 by Janeth Kent
Interesting and Helpful Google Search Features You’ll Want to Start Using
Category : Software 31-01-2021 by Iveta Karailievova
Deepfakes Detection – An Emerging Technological Challenge
Category : Technology 27-01-2021 by Iveta Karailievova
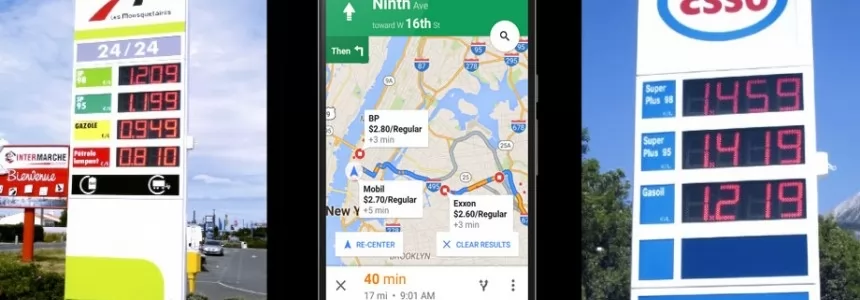
Google Maps updates and now shows gas prices at gas stations
Category : Software 21-01-2021 by Luigi Nori
Some Neat Ways to Improve Your Internet Browsing Experience?
Category : News and events 21-12-2020 by Janeth Kent
Website Traffic Getting Low? 4 Immediate Action to Take
Category : Web marketing 04-12-2020 by Luigi Nori
The best tricks and features to master your Android Smart TV
Category : Networking 05-11-2020 by Luigi Nori
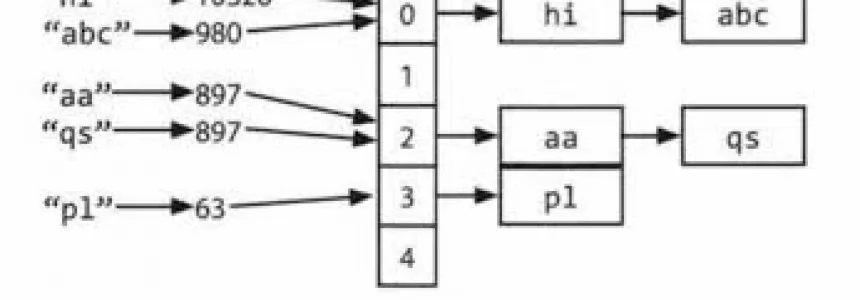
Hashmap: hashing, collisions and first functions
Category : C language 28-06-2020 by Alessio Mungelli
The new features coming to the Google search engine in autumn 2020
Category : Seo & sem 18-10-2020 by Luigi Nori
How to block any website with a password from your browser
Category : News and events 30-09-2020 by Silvia Mazzetta
Jennifer in Paradise: story of the first photo ever edited in Photoshop
Category : News and events 25-09-2020 by Silvia Mazzetta
How to securely access the Dark Web in 15 steps. Second part
Category : Security 08-03-2024 by Janeth Kent
How to securely access the Dark Web in 15 steps. First part
Category : Security 08-03-2024 by Silvia Mazzetta
How to comply with Google's quality guidelines in 2020
Category : Seo & sem 09-09-2020 by Silvia Mazzetta
How are businesses using artificial intelligence?
Category : News and events 21-06-2023 by Silvia Mazzetta
What cybersecurity professionals have learned from the lockdown experience
Category : Security 26-08-2020 by Silvia Mazzetta
5 Remote Careers You Can Start Online in 2020
Category : News and events 25-08-2020 by Silvia Mazzetta
Browse safely and privately from your mobile phone using a VPN
Category : Security 25-08-2020 by Janeth Kent
Get ready for the future: What Does The Future Of SEO Look Like?
Category : Seo 19-08-2020 by Silvia Mazzetta
Why is Website Performance Important for Online Businesses?
Category : Web marketing 24-07-2020 by Janeth Kent
How Learning Accents Connects Us To The World At Large
Category : Web marketing 16-07-2020 by Janeth Kent
Neumorphism (aka neomorphism) : new trend in UI design
Category : Ui/ux design 17-06-2020 by Silvia Mazzetta
How to Take Your Small Ecommerce Business to the Next Level
Category : Web marketing 25-01-2022 by Janeth Kent
Onion Search Engine: How to browse the Deep Web without Tor
Category : Security 25-05-2020 by Janeth Kent
Step by Step Guide to Successful Social Media Marketing
Category : Web marketing 16-05-2023 by Silvia Mazzetta