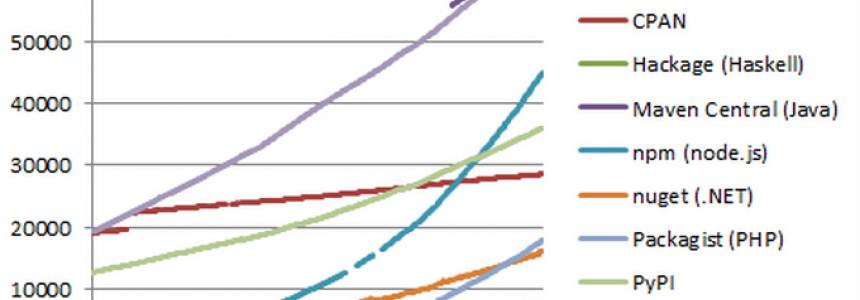
122 results for: networks
Top best AI Image Generators: unlocking creativity with Artificial Intelligence
Category : Technology 26-07-2025 by Janeth Kent
The Payment Request API: Revolutionizing Online Payments (Part 1)
Category : Javascript 12-06-2023 by Silvia Mazzetta
Infinite scrolling with native JavaScript using the Fetch API
Category : Javascript 05-11-2024 by Janeth Kent
The ultimate cybersecurity checklist for programmers
Category : Security 02-06-2023 by Silvia Mazzetta
Advanced Android tutorial: discover all your phone's secrets
Category : Mobile 06-05-2021 by Janeth Kent
How to hide the you are typing text in a WhatsApp group
Category : Social networks 25-03-2021 by Janeth Kent
Deepfakes Detection – An Emerging Technological Challenge
Category : Technology 27-01-2021 by Iveta Karailievova
Cumulative Layout Shift, what is and How to optimize CLS
Category : Seo & sem 14-01-2021 by Luigi Nori
Understanding LCP, CLS, FID. All about Core Web Vitals in Google Search Console
Category : Seo & sem 14-01-2021 by
Dark Web: the creepy side of the Internet is not as dark as believed
Category : Security 17-05-2023 by Silvia Mazzetta
Some Neat Ways to Improve Your Internet Browsing Experience?
Category : News and events 21-12-2020 by Janeth Kent
How to prevent your neighbor from hacking your Chromecast
Category : Networking 26-10-2020 by Luigi Nori
Jennifer in Paradise: story of the first photo ever edited in Photoshop
Category : News and events 25-09-2020 by Silvia Mazzetta
Data Scraping and Data Crawling, what are they for?
Category : Web marketing 25-09-2020 by Silvia Mazzetta
How to securely access the Dark Web in 15 steps. Second part
Category : Security 08-03-2024 by Janeth Kent
How are businesses using artificial intelligence?
Category : News and events 21-06-2023 by Silvia Mazzetta
What cybersecurity professionals have learned from the lockdown experience
Category : Security 26-08-2020 by Silvia Mazzetta
Browse safely and privately from your mobile phone using a VPN
Category : Security 25-08-2020 by Janeth Kent
Get ready for the future: What Does The Future Of SEO Look Like?
Category : Seo 19-08-2020 by Silvia Mazzetta
How to configure Tor to browse the deep web safely
Category : Security 12-08-2020 by Silvia Mazzetta
How to integrate native images lazy loading in your web projects
Category : Programming 03-04-2023 by Luigi Nori
Facebook, three questions to recognize fake news (and not share it)
Category : Social networks 02-07-2020 by Janeth Kent
Why do you vote the way you do in the age of misinformation and fake news?
Category : News and events 11-06-2020 by Silvia Mazzetta
How to Take Your Small Ecommerce Business to the Next Level
Category : Web marketing 25-01-2022 by Janeth Kent
How to get into the Deep Web: a guide to access TOR, ZeroNet, Freenet and I2P
Category : Security 07-05-2020 by Janeth Kent
Online Marketing Strategies for your Ecommerce
Category : Web marketing 20-04-2023 by Silvia Mazzetta
Facebook: how to remove hidden data and personal information
Category : Social networks 20-04-2020 by Silvia Mazzetta
The best websites of the Tor Deep Web and Dark Web Network
Category : Security 03-11-2022 by Janeth Kent
How to find everything you need on the Deep Web and the Dark Web
Category : Security 10-05-2021 by Silvia Mazzetta
How to Generate Static Sites with JavaScript Static Sites Generators
Category : Javascript 13-12-2019 by Luigi Nori
How They Can Hack You While Navigating: Protecting Your Digital Security
Category : Security 23-06-2023 by Silvia Mazzetta
What to Expect from Email Marketing Tools in 2019
Category : Web marketing 18-11-2019 by Janeth Kent
RCS: Everything you need to know about the successor to the SMS
Category : Mobile 18-06-2019 by Janeth Kent
The best collections of Royalty free videos for social networks
Category : Multimedia 02-03-2020 by Janeth Kent
Unlock Hidden SmartPhone Features with these Secret Codes
Category : Security 26-07-2025 by Janeth Kent
80 Linux Network Monitor Software & Tools for Managing & Monitoring Unix/Linux Systems
Category : Security 23-10-2018 by Janeth Kent
The best Free and Open-Source Video editing, VFX and compositing software
Category : Multimedia 01-03-2021 by Janeth Kent
How to Become a Leader in The Field of Digital Technology
Category : Startups 16-06-2020 by Janeth Kent
ArangoDB, install and configure the popular Database in ubuntu 16.04
Category : Databases 14-11-2017 by Janeth Kent
Top 8 Free Online Social Media Marketing Tools For Startups
Category : Web marketing 08-11-2022 by Janeth Kent
Facebook Prepack, The Next Big Thing In The JavaScript World
Category : Javascript 11-05-2017 by Janeth Kent
Ubuntu servers security: 25 security tools to armor your system
Category : Servers 14-09-2016 by Janeth Kent
8 Social Tools to interact with Customers and improve CX
Category : Social networks 22-07-2016 by Janeth Kent
The Future of Web Browsing: Liberating Content from the Confines of Space
Category : News and events 28-06-2023 by Janeth Kent
The importance of building a responsive website and targeting the mobile audience
Category : Web design 15-06-2020 by Silvia Mazzetta
Top Alternatives to Google Adsense (ideal for small publishers)
Category : Web marketing 15-06-2020 by Silvia Mazzetta








































































![Best Days to Post on Facebook [Infographic]](https://media.ma-no.org/img/860-300/admin-facebook-post-data1.png)