118 results for: password
Google Play Games on PC: Transforming Your Gaming Experience
Category : Videogames 06-06-2023 by Janeth Kent
Infinite scrolling with native JavaScript using the Fetch API
Category : Javascript 05-11-2024 by Janeth Kent
The ultimate cybersecurity checklist for programmers
Category : Security 02-06-2023 by Silvia Mazzetta
Advanced Android tutorial: discover all your phone's secrets
Category : Mobile 06-05-2021 by Janeth Kent
How to set up your Android phone: learn how to get your new phone up and running
Category : Mobile 28-04-2021 by Janeth Kent
Cybersecurity and Data Privacy: Why It Is So Important
Category : Security 26-02-2021 by Janeth Kent
The best tricks and features to master your Android Smart TV
Category : Networking 05-11-2020 by Luigi Nori
How to block any website with a password from your browser
Category : News and events 30-09-2020 by Silvia Mazzetta
How to securely access the Dark Web in 15 steps. Second part
Category : Security 08-03-2024 by Janeth Kent
How to securely access the Dark Web in 15 steps. First part
Category : Security 08-03-2024 by Silvia Mazzetta
What cybersecurity professionals have learned from the lockdown experience
Category : Security 26-08-2020 by Silvia Mazzetta
Browse safely and privately from your mobile phone using a VPN
Category : Security 25-08-2020 by Janeth Kent
First steps into JavaScript – a practical guide 3
Category : Javascript 07-05-2020 by Iveta Karailievova
What is Google My Business and how does it help my local business?
Category : Web marketing 02-05-2020 by Luigi Nori
How to find everything you need on the Deep Web and the Dark Web
Category : Security 10-05-2021 by Silvia Mazzetta
Cross-Origin Resource Sharing (CORS) and examples of XSS and CSRF
Category : Javascript 30-01-2020 by Luigi Nori
How They Can Hack You While Navigating: Protecting Your Digital Security
Category : Security 23-06-2023 by Silvia Mazzetta
The Steps to Take if You're the Victim of a Cyber Hack
Category : News and events 27-03-2019 by Janeth Kent
How to Set up a Fully Functional Mail Server on Ubuntu 16.04 with iRedMail
Category : Networking 30-03-2023 by Janeth Kent
A Guide to Integrate Social Media into Your E-Commerce Store
Category : News and events 09-07-2018 by Janeth Kent
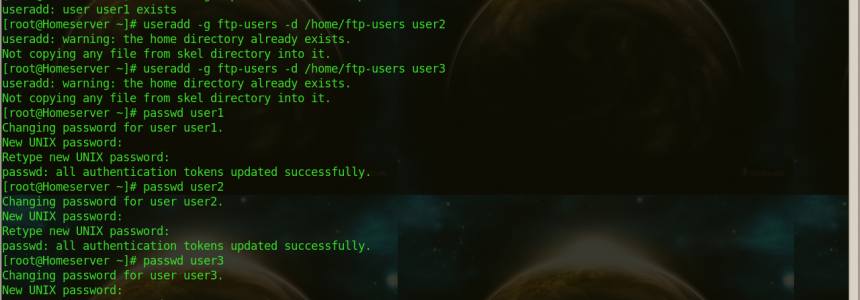
MYSQL: How to create a new user and give it full access only to 1 database
Category : Databases 07-02-2018 by Janeth Kent
ArangoDB, install and configure the popular Database in ubuntu 16.04
Category : Databases 14-11-2017 by Janeth Kent
How to Connect to a Remote Server via SSH from a Linux Shell
Category : Servers 16-02-2017 by Janeth Kent
Ubuntu servers security: 25 security tools to armor your system
Category : Servers 14-09-2016 by Janeth Kent
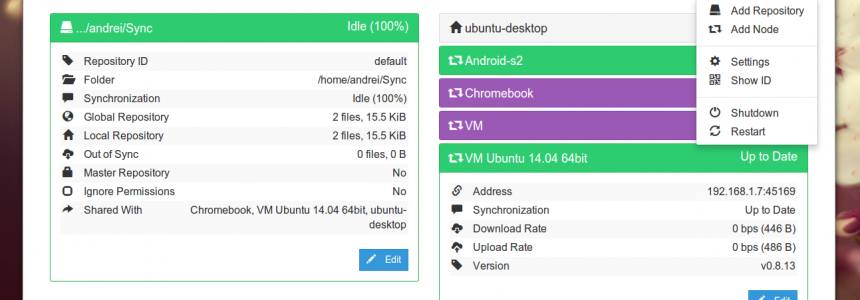
Install Syncthing on Ubuntu 16.04 using Debian Repository
Category : Servers 19-08-2016 by Janeth Kent
PHP7: Guide and References to all the changes between version 5.x and 7 of PHP
Category : Php 27-12-2015 by Janeth Kent
The Best Free SSH Tabbed Terminal Clients for Windows
Category : Networking 18-12-2023 by Janeth Kent
How to Create a Password Strength Indicator With jQuery
Category : Programming 18-12-2013 by Janeth Kent
PHP: Getting started with Object Oriented Programming in PHP5
Category : Php 12-08-2013 by Janeth Kent
WordPress tips and tricks: how to custumize your theme
Category : Web design 10-07-2013 by Janeth Kent
Which apps have access to your online profiles? Check it with MyPermissions app
Category : Software 26-06-2013 by Janeth Kent
Syncronize Files Between Two Ubuntu Servers Using Unison and Incron
Category : Networking 21-06-2013 by Janeth Kent
20 Open Source Scripts Applications for Web Developers
Category : Programming 11-08-2016 by Janeth Kent
Million of visitors per day with a super cheap php mysql server using nginx and varnish
Category : Networking 28-05-2013 by Janeth Kent
Ubuntu UFW Firewall - Uncomplicated Firewall for Ubuntu
Category : Networking 27-05-2013 by Janeth Kent
Php: Automatic Site/Directory Backup via FTP with PHP
Category : Programming 29-04-2013 by Janeth Kent