431 results for: import
How to include a JavaScript file in another JavaScript file
Category : Javascript 25-09-2024 by Janeth Kent
Transitioning from a Home Office to a Virtual Office
Category : Web marketing 08-03-2024 by Janeth Kent
The best and most amazing Alexa Hacks you should know about
Category : Operating systems 30-06-2023 by Janeth Kent
Google Play Games on PC: Transforming Your Gaming Experience
Category : Videogames 06-06-2023 by Janeth Kent
How to Track Flight Status in real-time using the Flight Tracker API
Category : Php 12-06-2023 by Janeth Kent
The Payment Request API: Revolutionizing Online Payments (Part 1)
Category : Javascript 12-06-2023 by Silvia Mazzetta
Android Hidden Codes: unveiling custom dialer codes and their functionality
Category : Mobile 02-06-2023 by Janeth Kent
Let's create a Color Picker from scratch with HTML5 Canvas, Javascript and CSS3
Category : Web design 01-06-2023 by Janeth Kent
The Importance of Maintaining a Crisis-Ready Social Media Strategy: A Closer Look
Category : Social networks 01-06-2023 by Janeth Kent
Mastering array sorting in JavaScript: a guide to the sort() function
Category : Javascript 29-05-2023 by Janeth Kent
Is AI sexist? A gender perspective in Robotics and Artificial Intelligence
Category : News and events 22-05-2023 by Silvia Mazzetta
How to download an email in PDF format in Gmail for Android
Category : Technology 16-05-2023 by Janeth Kent
What are javascript symbols and how can they help you?
Category : Javascript 20-12-2022 by Janeth Kent
Benefits of Corporate Social Responsibility to Business
Category : Web marketing 06-12-2022 by Janeth Kent
The history of video games: from entertainment to virtual reality
Category : Videogames 28-11-2022 by Janeth Kent
The first videogame tournaments: the origin of eSports
Category : Videogames 19-10-2022 by Janeth Kent
The AI Revolution: How Are Small Businesses Beginning To Implement AI?
Category : Technology 26-07-2025 by Janeth Kent
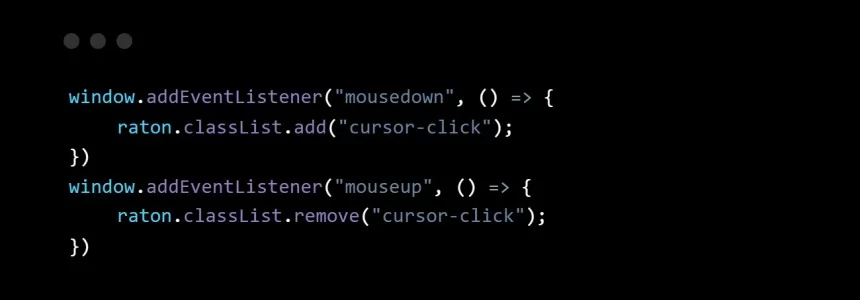
How to make your own custom cursor for your website
Category : Web design 08-06-2022 by Nadal Vicens
8 benefits of having a website for your business
Category : Web marketing 03-06-2022 by Nadal Vicens
How synchronize the scroll of two divs with JavaScript
Category : Javascript 26-05-2023 by Silvia Mazzetta
Strings in JavaScript: What they are and how to use them
Category : Javascript 22-06-2021 by Janeth Kent
Why E-Commerce Businesses Should be Using Cloud Computing
Category : Web marketing 01-06-2021 by Silvia Mazzetta
Advanced Android tutorial: discover all your phone's secrets
Category : Mobile 06-05-2021 by Janeth Kent
How to set up your Android phone: learn how to get your new phone up and running
Category : Mobile 28-04-2021 by Janeth Kent
How to improve customer experience through speech recognition
Category : Technology 27-04-2021 by Janeth Kent
Parental controls on Android: how to make mobiles and tablets child-friendly
Category : Security 26-04-2021 by Janeth Kent
How To Use Varnish As A Highly Available Load Balancer On Ubuntu 20.04 With SSL
Category : Servers 25-04-2021 by Janeth Kent
What is the First Input Delay and why is it important?
Category : Seo & sem 25-03-2021 by Janeth Kent
Elon Musk To Found Starbase, A City In Texas To House His Companies And Projects
Category : Technology 05-03-2021 by Janeth Kent
Cybersecurity and Data Privacy: Why It Is So Important
Category : Security 26-02-2021 by Janeth Kent
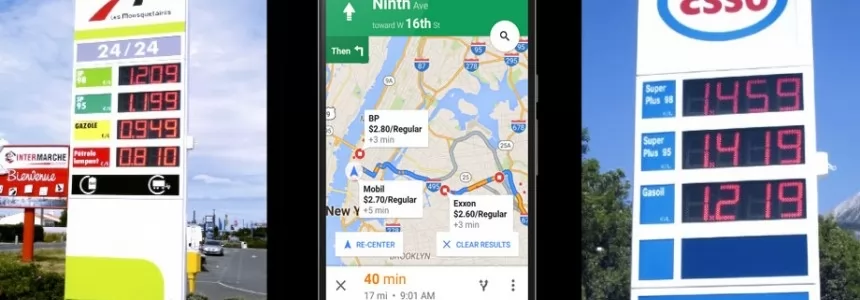
Google Maps updates and now shows gas prices at gas stations
Category : Software 21-01-2021 by Luigi Nori
Cumulative Layout Shift, what is and How to optimize CLS
Category : Seo & sem 14-01-2021 by Luigi Nori
Understanding LCP, CLS, FID. All about Core Web Vitals in Google Search Console
Category : Seo & sem 14-01-2021 by
Read comics online: best websites and apps to download and read digital comics
Category : News and events 26-05-2023 by Silvia Mazzetta
Dark Web: the creepy side of the Internet is not as dark as believed
Category : Security 17-05-2023 by Silvia Mazzetta
Cross cultural challenges in web design, an overview
Category : Web design 21-12-2020 by Maria Antonietta Marino
Some Neat Ways to Improve Your Internet Browsing Experience?
Category : News and events 21-12-2020 by Janeth Kent
Making AJAX requests to a REST API using vanilla JavaScript and XHR
Category : Javascript 25-11-2020 by Iveta Karailievova
Why You Should Hire Node.js Developer for Your Backend Development
Category : Javascript 27-10-2020 by Luigi Nori
What's the Difference between Google TV and Android TV?
Category : Software 27-10-2020 by Silvia Mazzetta
3 awesome ways technology is helping us combat the COVID pandemic
Category : Technology 28-10-2020 by Iveta Karailievova
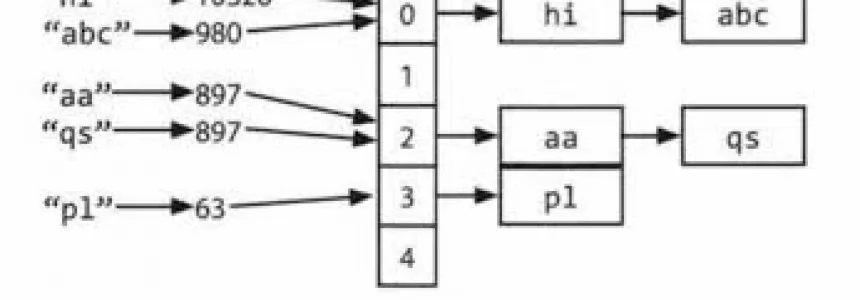
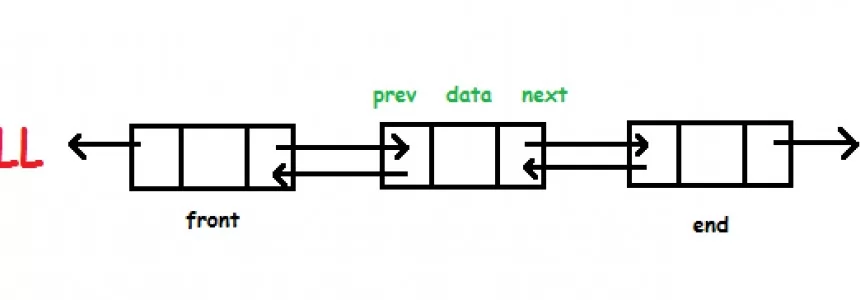
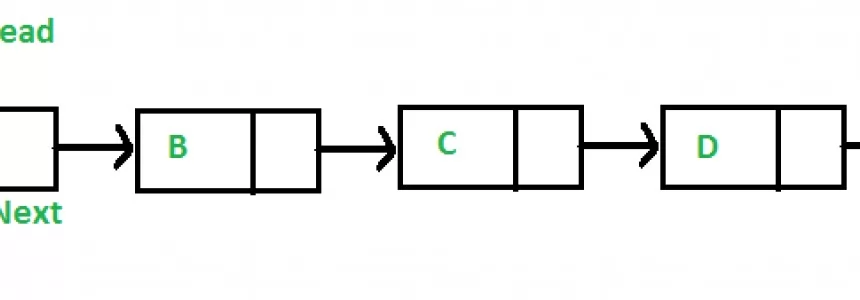
Hashmap: hashing, collisions and first functions
Category : C language 28-06-2020 by Alessio Mungelli
Javascript: what are callbacks and how to use them.
Category : Javascript 23-10-2020 by Silvia Mazzetta
The new features coming to the Google search engine in autumn 2020
Category : Seo & sem 18-10-2020 by Luigi Nori