157 results for: email
Transitioning from a Home Office to a Virtual Office
Category : Web marketing 08-03-2024 by Janeth Kent
How to Use ChatGPT to automatically create Spotify playlists
Category : Technology 23-06-2023 by Janeth Kent
The Payment Request API: Revolutionizing Online Payments (Part 2)
Category : Javascript 08-06-2023 by Silvia Mazzetta
Marketing Trends in Technology 2023: Spotlight on Inflation
Category : Web marketing 01-06-2023 by Janeth Kent
How to download an email in PDF format in Gmail for Android
Category : Technology 16-05-2023 by Janeth Kent
Does Google's artificial intelligence have feelings?
Category : Technology 04-08-2022 by Janeth Kent
Why E-Commerce Businesses Should be Using Cloud Computing
Category : Web marketing 01-06-2021 by Silvia Mazzetta
How to set up your Android phone: learn how to get your new phone up and running
Category : Mobile 28-04-2021 by Janeth Kent
htaccess Rules to Help Protect from SQL Injections and XSS
Category : Security 01-03-2021 by Janeth Kent
Deepfakes Detection – An Emerging Technological Challenge
Category : Technology 27-01-2021 by Iveta Karailievova
Read comics online: best websites and apps to download and read digital comics
Category : News and events 26-05-2023 by Silvia Mazzetta
Some Neat Ways to Improve Your Internet Browsing Experience?
Category : News and events 21-12-2020 by Janeth Kent
The BleedingTooth vulnerability and other Bluetooth security risks
Category : Security 10-11-2020 by Iveta Karailievova
How to securely access the Dark Web in 15 steps. Second part
Category : Security 08-03-2024 by Janeth Kent
Suggestions to Improve the Efficiency of a Small Business
Category : Web marketing 26-07-2025 by Janeth Kent
Free Netflix: everything you can see without subscribing
Category : News and events 09-09-2020 by Luigi Nori
Browse safely and privately from your mobile phone using a VPN
Category : Security 25-08-2020 by Janeth Kent
7 Killer Strategies to Increase Your Sales Funnel Conversion Rates
Category : Web marketing 23-07-2020 by Janeth Kent
How to get into the Deep Web: a guide to access TOR, ZeroNet, Freenet and I2P
Category : Security 07-05-2020 by Janeth Kent
What is Google My Business and how does it help my local business?
Category : Web marketing 02-05-2020 by Luigi Nori
Online Marketing Strategies for your Ecommerce
Category : Web marketing 20-04-2023 by Silvia Mazzetta
The best websites of the Tor Deep Web and Dark Web Network
Category : Security 03-11-2022 by Janeth Kent
How to find everything you need on the Deep Web and the Dark Web
Category : Security 10-05-2021 by Silvia Mazzetta
Best Free Image Optimization Tools for Image Compression
Category : Software 27-03-2020 by Janeth Kent
Best ways to start a video conference without registration
Category : Multimedia 21-04-2020 by Silvia Mazzetta
Cross-Origin Resource Sharing (CORS) and examples of XSS and CSRF
Category : Javascript 30-01-2020 by Luigi Nori
How to Build Your eCommerce's Email List Using Instagram
Category : Web marketing 06-12-2019 by Luigi Nori
How They Can Hack You While Navigating: Protecting Your Digital Security
Category : Security 23-06-2023 by Silvia Mazzetta
What to Expect from Email Marketing Tools in 2019
Category : Web marketing 18-11-2019 by Janeth Kent
Unlock Hidden SmartPhone Features with these Secret Codes
Category : Security 26-07-2025 by Janeth Kent
Features you will get in EaseUS data recovery software
Category : Software 25-06-2019 by Janeth Kent
The Steps to Take if You're the Victim of a Cyber Hack
Category : News and events 27-03-2019 by Janeth Kent
What You Need to Know When Sending a Press Release to Newswire
Category : News and events 25-02-2019 by Janeth Kent
The Most Useful 50 Web Sites you wish you knew earlier
Category : Web marketing 13-06-2020 by Janeth Kent
Six Ways to Make Your Design Brand Stand Out with a Portfolio
Category : Ui/ux design 21-11-2018 by Janeth Kent
80 Linux Network Monitor Software & Tools for Managing & Monitoring Unix/Linux Systems
Category : Security 23-10-2018 by Janeth Kent
A Guide to Moving IT Services During an Office Relocation
Category : News and events 21-08-2018 by Janeth Kent
Four of the Biggest Reasons Your Emails are Sent to Spam
Category : Web marketing 14-08-2018 by Janeth Kent
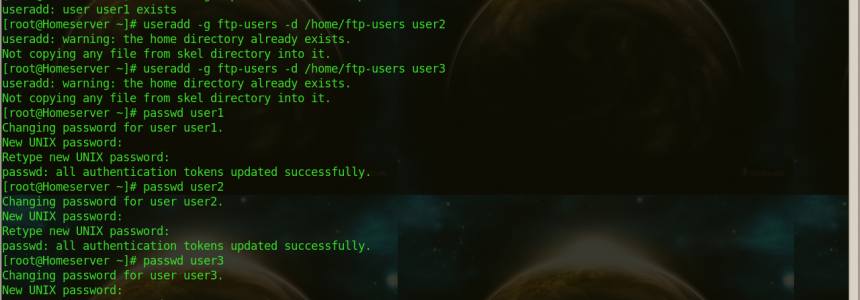
How to Set up a Fully Functional Mail Server on Ubuntu 16.04 with iRedMail
Category : Networking 30-03-2023 by Janeth Kent
A Guide to Integrate Social Media into Your E-Commerce Store
Category : News and events 09-07-2018 by Janeth Kent
Send Push Notification to Users Using Firebase Messaging Service in PHP
Category : Php 14-05-2018 by Janeth Kent
How Our Relationship with the Internet has Changed in the Last 20 Years
Category : News and events 29-04-2021 by Janeth Kent
Top 8 Free Online Social Media Marketing Tools For Startups
Category : Web marketing 08-11-2022 by Janeth Kent
5 best open source version control systems tools for sysadmins
Category : Software 13-05-2017 by Janeth Kent
An Introduction to Email Segmentation: Boosting Engagement and Personalization
Category : Web marketing 23-06-2023 by Janeth Kent
The Best Lightweight Linux Distributions For Older PC's
Category : Operating systems 12-03-2017 by Janeth Kent
Fetch API, an amazing replacement of XMLHttpRequest AJAX
Category : Programming 19-02-2017 by Janeth Kent
8 Social Tools to interact with Customers and improve CX
Category : Social networks 22-07-2016 by Janeth Kent
Guide: Install Free SSL Certificate On Your Website with Let's Encrypt
Category : Networking 09-05-2020 by Janeth Kent