203 results for: mac
Transitioning from a Home Office to a Virtual Office
Category : Web marketing 08-03-2024 by Janeth Kent
The best and most amazing Alexa Hacks you should know about
Category : Operating systems 30-06-2023 by Janeth Kent
Top best AI Image Generators: unlocking creativity with Artificial Intelligence
Category : Technology 26-07-2025 by Janeth Kent
Android Hidden Codes: unveiling custom dialer codes and their functionality
Category : Mobile 02-06-2023 by Janeth Kent
Is AI sexist? A gender perspective in Robotics and Artificial Intelligence
Category : News and events 22-05-2023 by Silvia Mazzetta
A Step-by-Step Process to Using Artificial Intelligence as a Startup
Category : Technology 14-03-2023 by Janeth Kent
Benefits of Corporate Social Responsibility to Business
Category : Web marketing 06-12-2022 by Janeth Kent
The history of video games: from entertainment to virtual reality
Category : Videogames 28-11-2022 by Janeth Kent
The first videogame tournaments: the origin of eSports
Category : Videogames 19-10-2022 by Janeth Kent
The AI Revolution: How Are Small Businesses Beginning To Implement AI?
Category : Technology 26-07-2025 by Janeth Kent
Does Google's artificial intelligence have feelings?
Category : Technology 04-08-2022 by Janeth Kent
How to set up your Android phone: learn how to get your new phone up and running
Category : Mobile 28-04-2021 by Janeth Kent
Top Graphic Design e-Books & How to Get them on Your iDevice
Category : Ui/ux design 03-03-2021 by Luigi Nori
Deepfakes Detection – An Emerging Technological Challenge
Category : Technology 27-01-2021 by Iveta Karailievova
Python or Swift: Revealing Benefits and Drawbacks of Each Language and Their Differences
Category : Programming 04-03-2021 by
The BleedingTooth vulnerability and other Bluetooth security risks
Category : Security 10-11-2020 by Iveta Karailievova
Why You Should Hire Node.js Developer for Your Backend Development
Category : Javascript 27-10-2020 by Luigi Nori
What's the Difference between Google TV and Android TV?
Category : Software 27-10-2020 by Silvia Mazzetta
3 awesome ways technology is helping us combat the COVID pandemic
Category : Technology 28-10-2020 by Iveta Karailievova
A Dev compile and install Windows XP and Server 2003 from filtered source code
Category : Operating systems 08-10-2020 by Luigi Nori
Data Scraping and Data Crawling, what are they for?
Category : Web marketing 25-09-2020 by Silvia Mazzetta
How to securely access the Dark Web in 15 steps. Second part
Category : Security 08-03-2024 by Janeth Kent
How to securely access the Dark Web in 15 steps. First part
Category : Security 08-03-2024 by Silvia Mazzetta
How are businesses using artificial intelligence?
Category : News and events 21-06-2023 by Silvia Mazzetta
What cybersecurity professionals have learned from the lockdown experience
Category : Security 26-08-2020 by Silvia Mazzetta
Browse safely and privately from your mobile phone using a VPN
Category : Security 25-08-2020 by Janeth Kent
How to configure Tor to browse the deep web safely
Category : Security 12-08-2020 by Silvia Mazzetta
How to Pick the Best Macbook for Graphic Design Work
Category : News and events 05-08-2020 by Janeth Kent
Awesome JavaScript Games and Js Software to create Games
Category : Javascript 30-06-2020 by Janeth Kent
How to get into the Deep Web: a guide to access TOR, ZeroNet, Freenet and I2P
Category : Security 07-05-2020 by Janeth Kent
What is Google My Business and how does it help my local business?
Category : Web marketing 02-05-2020 by Luigi Nori
The best websites of the Tor Deep Web and Dark Web Network
Category : Security 03-11-2022 by Janeth Kent
Coronavirus: Citizen Science projects to help research from home
Category : News and events 02-04-2020 by Silvia Mazzetta
How to find everything you need on the Deep Web and the Dark Web
Category : Security 10-05-2021 by Silvia Mazzetta
How to see the websites visited during the incognito mode and delete them
Category : Security 21-02-2020 by Silvia Mazzetta
How the Java Swing is Worthy in Designing the Photo Editing App
Category : Java 03-04-2023 by Janeth Kent
Javascript overcomes Java as the most popular programming language of 2019
Category : Javascript 18-09-2019 by Silvia Mazzetta
How Technology has Improved the Way We Do Business
Category : Web marketing 20-06-2019 by Janeth Kent
Why Becoming A Certified Scrum Master Can Launch Your Career
Category : Startups 20-06-2019 by Janeth Kent
How to Create your own custom Linux system, step by step
Category : Operating systems 14-06-2019 by Janeth Kent
Unlock Hidden SmartPhone Features with these Secret Codes
Category : Security 26-07-2025 by Janeth Kent
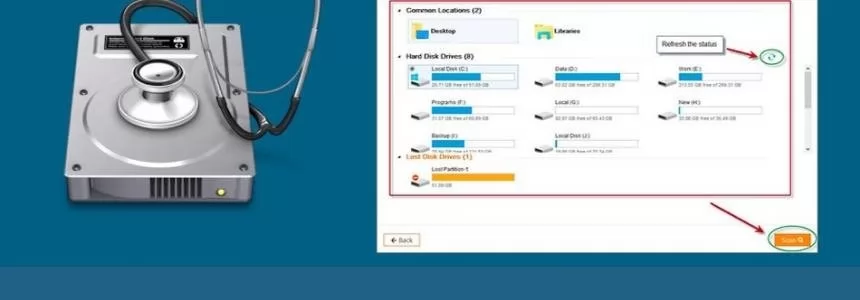
Features you will get in EaseUS data recovery software
Category : Software 25-06-2019 by Janeth Kent
How to Successfully Promote Your Healthcare Business
Category : Web marketing 20-03-2019 by Janeth Kent