692 results for: amp
How to include a JavaScript file in another JavaScript file
Category : Javascript 25-09-2024 by Janeth Kent
The best and most amazing Alexa Hacks you should know about
Category : Operating systems 30-06-2023 by Janeth Kent
How to Use ChatGPT to automatically create Spotify playlists
Category : Technology 23-06-2023 by Janeth Kent
Google Play Games on PC: Transforming Your Gaming Experience
Category : Videogames 06-06-2023 by Janeth Kent
How to Track Flight Status in real-time using the Flight Tracker API
Category : Php 12-06-2023 by Janeth Kent
The Payment Request API: Revolutionizing Online Payments (Part 2)
Category : Javascript 08-06-2023 by Silvia Mazzetta
The Payment Request API: Revolutionizing Online Payments (Part 1)
Category : Javascript 12-06-2023 by Silvia Mazzetta
Android Hidden Codes: unveiling custom dialer codes and their functionality
Category : Mobile 02-06-2023 by Janeth Kent
Marketing Trends in Technology 2023: Spotlight on Inflation
Category : Web marketing 01-06-2023 by Janeth Kent
The Importance of Maintaining a Crisis-Ready Social Media Strategy: A Closer Look
Category : Social networks 01-06-2023 by Janeth Kent
How do you stop JavaScript execution for a while: sleep()
Category : Javascript 31-05-2023 by Janeth Kent
Mastering array sorting in JavaScript: a guide to the sort() function
Category : Javascript 29-05-2023 by Janeth Kent
Is AI sexist? A gender perspective in Robotics and Artificial Intelligence
Category : News and events 22-05-2023 by Silvia Mazzetta
Should Your Social Media Strategy Always Be Ready for a Crisis?
Category : Social networks 01-06-2023 by Janeth Kent
How to download an email in PDF format in Gmail for Android
Category : Technology 16-05-2023 by Janeth Kent
Infinite scrolling with native JavaScript using the Fetch API
Category : Javascript 05-11-2024 by Janeth Kent
Sorting elements with SortableJS and storing them in localStorage
Category : Javascript 15-05-2023 by Janeth Kent
A Step-by-Step Process to Using Artificial Intelligence as a Startup
Category : Technology 14-03-2023 by Janeth Kent
Benefits of Corporate Social Responsibility to Business
Category : Web marketing 06-12-2022 by Janeth Kent
The history of video games: from entertainment to virtual reality
Category : Videogames 28-11-2022 by Janeth Kent
Sick of Video Games? Here are Some Other Pastimes to Try
Category : Technology 29-11-2022 by Janeth Kent
The first videogame tournaments: the origin of eSports
Category : Videogames 19-10-2022 by Janeth Kent
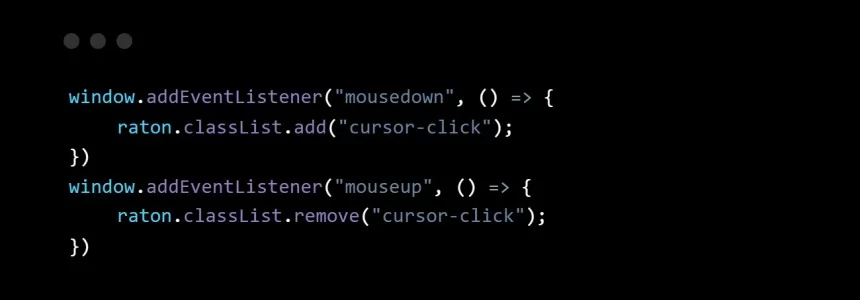
How to make your own custom cursor for your website
Category : Web design 08-06-2022 by Nadal Vicens
8 benefits of having a website for your business
Category : Web marketing 03-06-2022 by Nadal Vicens
Difference between arrow and normal functions in JavaScript
Category : Javascript 30-08-2021 by Janeth Kent
JavaScript Arrow functions: What they are and how to use them
Category : Javascript 30-08-2021 by Janeth Kent
How to insert an element into an array with JavaScript
Category : Javascript 20-08-2021 by Janeth Kent
What is the difference between primitives types and objects in JavaScript?
Category : Javascript 26-05-2023 by Silvia Mazzetta
How synchronize the scroll of two divs with JavaScript
Category : Javascript 26-05-2023 by Silvia Mazzetta
Strings in JavaScript: What they are and how to use them
Category : Javascript 22-06-2021 by Janeth Kent
Advanced Android tutorial: discover all your phone's secrets
Category : Mobile 06-05-2021 by Janeth Kent
How to set up your Android phone: learn how to get your new phone up and running
Category : Mobile 28-04-2021 by Janeth Kent
5 Terrific iOS-Friendly Canva Alternatives to Upgrade Your Marketing Visuals
Category : Web marketing 05-05-2021 by Janeth Kent
How to improve customer experience through speech recognition
Category : Technology 27-04-2021 by Janeth Kent
Parental controls on Android: how to make mobiles and tablets child-friendly
Category : Security 26-04-2021 by Janeth Kent
Top Graphic Design e-Books & How to Get them on Your iDevice
Category : Ui/ux design 03-03-2021 by Luigi Nori
Cybersecurity and Data Privacy: Why It Is So Important
Category : Security 26-02-2021 by Janeth Kent
Interesting and Helpful Google Search Features You’ll Want to Start Using
Category : Software 31-01-2021 by Iveta Karailievova