295 results for: event
How to include a JavaScript file in another JavaScript file
Category : Javascript 25-09-2024 by Janeth Kent
Transitioning from a Home Office to a Virtual Office
Category : Web marketing 08-03-2024 by Janeth Kent
The best and most amazing Alexa Hacks you should know about
Category : Operating systems 30-06-2023 by Janeth Kent
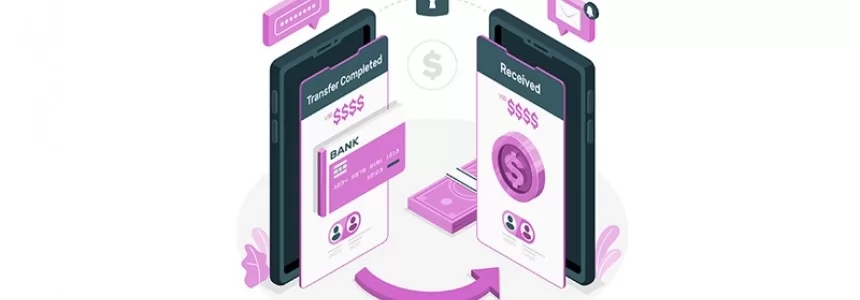
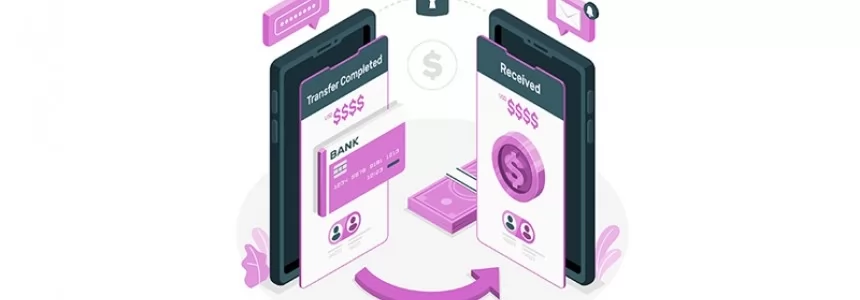
The Payment Request API: Revolutionizing Online Payments (Part 2)
Category : Javascript 08-06-2023 by Silvia Mazzetta
The Payment Request API: Revolutionizing Online Payments (Part 1)
Category : Javascript 12-06-2023 by Silvia Mazzetta
Let's create a Color Picker from scratch with HTML5 Canvas, Javascript and CSS3
Category : Web design 01-06-2023 by Janeth Kent
The Importance of Maintaining a Crisis-Ready Social Media Strategy: A Closer Look
Category : Social networks 01-06-2023 by Janeth Kent
Should Your Social Media Strategy Always Be Ready for a Crisis?
Category : Social networks 01-06-2023 by Janeth Kent
Infinite scrolling with native JavaScript using the Fetch API
Category : Javascript 05-11-2024 by Janeth Kent
A Step-by-Step Process to Using Artificial Intelligence as a Startup
Category : Technology 14-03-2023 by Janeth Kent
The history of video games: from entertainment to virtual reality
Category : Videogames 28-11-2022 by Janeth Kent
Sick of Video Games? Here are Some Other Pastimes to Try
Category : Technology 29-11-2022 by Janeth Kent
The first videogame tournaments: the origin of eSports
Category : Videogames 19-10-2022 by Janeth Kent
How to make your own custom cursor for your website
Category : Web design 08-06-2022 by Nadal Vicens
JavaScript Arrow functions: What they are and how to use them
Category : Javascript 30-08-2021 by Janeth Kent
The ultimate cybersecurity checklist for programmers
Category : Security 02-06-2023 by Silvia Mazzetta
How to access webcam and grab an image using HTML5 and Javascript
Category : Javascript 20-05-2021 by Janeth Kent
Advanced Android tutorial: discover all your phone's secrets
Category : Mobile 06-05-2021 by Janeth Kent
Parental controls on Android: how to make mobiles and tablets child-friendly
Category : Security 26-04-2021 by Janeth Kent
htaccess Rules to Help Protect from SQL Injections and XSS
Category : Security 01-03-2021 by Janeth Kent
Cybersecurity and Data Privacy: Why It Is So Important
Category : Security 26-02-2021 by Janeth Kent
Deepfakes Detection – An Emerging Technological Challenge
Category : Technology 27-01-2021 by Iveta Karailievova
Understanding LCP, CLS, FID. All about Core Web Vitals in Google Search Console
Category : Seo & sem 14-01-2021 by
A FULFILLED PROMISE - Using the FETCH API to make AJAX calls
Category : Javascript 26-12-2020 by Iveta Karailievova
How to make the website's dark mode persistent with Local Storage, CSS and JS
Category : Css 22-12-2020 by
Some Neat Ways to Improve Your Internet Browsing Experience?
Category : News and events 21-12-2020 by Janeth Kent
Making AJAX requests to a REST API using vanilla JavaScript and XHR
Category : Javascript 25-11-2020 by Iveta Karailievova
The best tricks and features to master your Android Smart TV
Category : Networking 05-11-2020 by Luigi Nori
Why You Should Hire Node.js Developer for Your Backend Development
Category : Javascript 27-10-2020 by Luigi Nori
How to prevent your neighbor from hacking your Chromecast
Category : Networking 26-10-2020 by Luigi Nori
3 awesome ways technology is helping us combat the COVID pandemic
Category : Technology 28-10-2020 by Iveta Karailievova
Javascript: what are callbacks and how to use them.
Category : Javascript 23-10-2020 by Silvia Mazzetta
How to change the arrow icon on Google Maps to a 3D car
Category : News and events 17-05-2023 by Silvia Mazzetta
A Dev compile and install Windows XP and Server 2003 from filtered source code
Category : Operating systems 08-10-2020 by Luigi Nori
How to securely access the Dark Web in 15 steps. First part
Category : Security 08-03-2024 by Silvia Mazzetta
How to ‘leave’ a WhatsApp group without actually leaving
Category : Social networks 10-09-2020 by Silvia Mazzetta
What cybersecurity professionals have learned from the lockdown experience
Category : Security 26-08-2020 by Silvia Mazzetta
Small and medium enterprises can now earn money by holding online events on Facebook
Category : Web marketing 19-08-2020 by Luigi Nori
The 6 Essentials for Creating a Visually Appealing Web Design
Category : Web design 25-08-2020 by Silvia Mazzetta
How to configure Tor to browse the deep web safely
Category : Security 12-08-2020 by Silvia Mazzetta
How to Pick the Best Macbook for Graphic Design Work
Category : News and events 05-08-2020 by Janeth Kent
How to integrate native images lazy loading in your web projects
Category : Programming 03-04-2023 by Luigi Nori
Why is Website Performance Important for Online Businesses?
Category : Web marketing 24-07-2020 by Janeth Kent
How Learning Accents Connects Us To The World At Large
Category : Web marketing 16-07-2020 by Janeth Kent
How to get notified when one of your WhatsApp contact is online
Category : Software 15-06-2020 by Silvia Mazzetta
How to move Chrome, Firefox or Edge cache to save space
Category : News and events 04-06-2020 by Janeth Kent