82 results for: hidden
The best and most amazing Alexa Hacks you should know about
Category : Operating systems 30-06-2023 by Janeth Kent
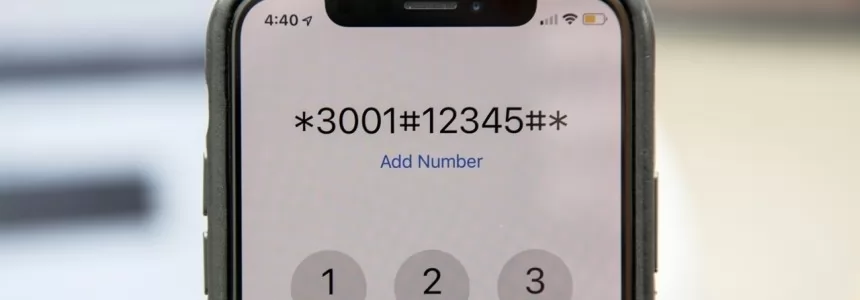
Android Hidden Codes: unveiling custom dialer codes and their functionality
Category : Mobile 02-06-2023 by Janeth Kent
What are javascript symbols and how can they help you?
Category : Javascript 20-12-2022 by Janeth Kent
How synchronize the scroll of two divs with JavaScript
Category : Javascript 26-05-2023 by Silvia Mazzetta
Interesting and Helpful Google Search Features You’ll Want to Start Using
Category : Software 31-01-2021 by Iveta Karailievova
Cumulative Layout Shift, what is and How to optimize CLS
Category : Seo & sem 14-01-2021 by Luigi Nori
How to use your browser as a file browser, in Chrome or Microsoft Edge
Category : Technology 26-12-2020 by Janeth Kent
Cross cultural challenges in web design, an overview
Category : Web design 21-12-2020 by Maria Antonietta Marino
The best tricks and features to master your Android Smart TV
Category : Networking 05-11-2020 by Luigi Nori
How to securely access the Dark Web in 15 steps. First part
Category : Security 08-03-2024 by Silvia Mazzetta
How to comply with Google's quality guidelines in 2020
Category : Seo & sem 09-09-2020 by Silvia Mazzetta
How to configure Tor to browse the deep web safely
Category : Security 12-08-2020 by Silvia Mazzetta
How to integrate native images lazy loading in your web projects
Category : Programming 03-04-2023 by Luigi Nori
Why is Website Performance Important for Online Businesses?
Category : Web marketing 24-07-2020 by Janeth Kent
How to get notified when one of your WhatsApp contact is online
Category : Software 15-06-2020 by Silvia Mazzetta
Step by Step Guide to Successful Social Media Marketing
Category : Web marketing 16-05-2023 by Silvia Mazzetta
How to get into the Deep Web: a guide to access TOR, ZeroNet, Freenet and I2P
Category : Security 07-05-2020 by Janeth Kent
Web shells as a security thread for web applications
Category : Security 04-05-2020 by Iveta Karailievova
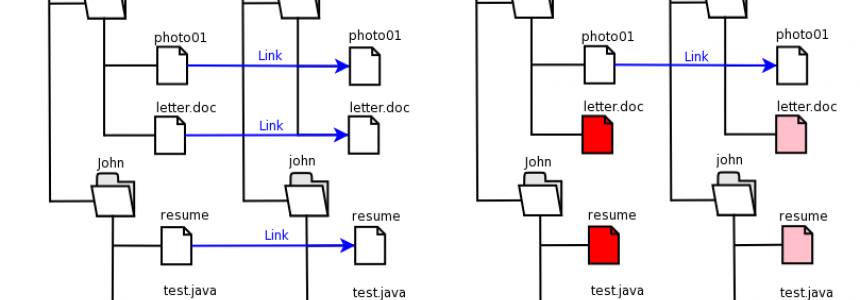
Facebook: how to remove hidden data and personal information
Category : Social networks 20-04-2020 by Silvia Mazzetta
The best websites of the Tor Deep Web and Dark Web Network
Category : Security 03-11-2022 by Janeth Kent
Easy Face and hand tracking browser detection with TensorFlow.js AI and MediaPipe
Category : Programming 09-04-2020 by Luigi Nori
How to find everything you need on the Deep Web and the Dark Web
Category : Security 10-05-2021 by Silvia Mazzetta
How They Can Hack You While Navigating: Protecting Your Digital Security
Category : Security 23-06-2023 by Silvia Mazzetta
Unlock Hidden SmartPhone Features with these Secret Codes
Category : Security 26-07-2025 by Janeth Kent
Fullscreen Background Video HTML5 And CSS cross-browser
Category : Web design 10-05-2020 by Silvia Mazzetta
Ubuntu servers security: 25 security tools to armor your system
Category : Servers 14-09-2016 by Janeth Kent
PHP7: Guide and References to all the changes between version 5.x and 7 of PHP
Category : Php 27-12-2015 by Janeth Kent
How to Create a .ONION Website and Domain With Tor Network
Category : Networking 02-11-2014 by Janeth Kent
How to Retrieve Twitter Timeline and Hashtags in PHP
Category : Programming 12-07-2013 by Janeth Kent
WARNING: New Malware Threat in Twitter's Topics
Category : News and events 23-04-2013 by Janeth Kent
The Best tools that may come in handy in your online life
Category : Software 01-05-2020 by Janeth Kent
How to install and configure vsftpd FTP server in Ubuntu 12.10
Category : Networking 11-04-2013 by Janeth Kent