Not a lot of people know about .onion websites, not many people actually use it. .ONION websites are used by people who want to stay anonymous. In addition, .onion websites are the first layer of the Deep Web. Which is basically described in the picture bellow
As many websites say, the Deep Web is about 96% of the WWW content. It's full of illegal things, for example, drug dealers, private information sellers, and child p0rn websites. Plus, some people say that you can find hit-men and assassins there!
You can search about the deep web if you want to know more, but as an advise, don't access it much. This tutorial is just for educational purposes, and for you to know about this.
First of All let's start with the requirements:
- Tor Installed (Windows) OR Downloaded and extracted (Linux)
- A Server like Apache. (Windows users are advised to use XAMPP and Linux users, you can simply install Apache2 on your machine.)
- Text Editor.
If you have all the above, then you're ready to go!
First of all run Tor to make sure it's working:

If it's working, then that's good you're good to go for the next step.
Stop and close Tor for now,
Then Open the following file:
WINDOWS:
C:\Tor Browser\Data\Tor\torrc
LINUX:
open the extracted folder from tor > Data > Tor > torrc
Then add the following text at the bottom of the file:
WINDOWS:
# Hidden Service
HiddenServiceDir C:\Users\UserName\tor_service
HiddenServicePort 80 127.0.0.1:80
Linux:
# Hidden Service
HiddenServiceDir /root/tor_service
HiddenServicePort 80 127.0.0.1:80
You can change from root to any user you are using.
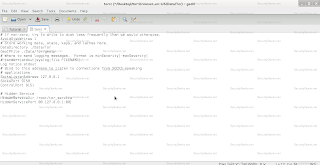
Now make the directory in the path you added in torrc (tor_service)
.png)
Now start you apache server and make sure it's working!

If it's working, start Tor!
Check Log Message to check that there was no error starting it!

No errors! Now check the folder that you created "tor_service" You will find two files!

Open the file "hostname" and you will find you .onion link!!

This link is now working and ONLY ACCESSIBLE for Tor users!
Want to test it? Open tor, and access it!



