78 results for: privacy
Is AI sexist? A gender perspective in Robotics and Artificial Intelligence
Category : News and events 22-05-2023 by Silvia Mazzetta
How to download an email in PDF format in Gmail for Android
Category : Technology 16-05-2023 by Janeth Kent
How to hide the you are typing text in a WhatsApp group
Category : Social networks 25-03-2021 by Janeth Kent
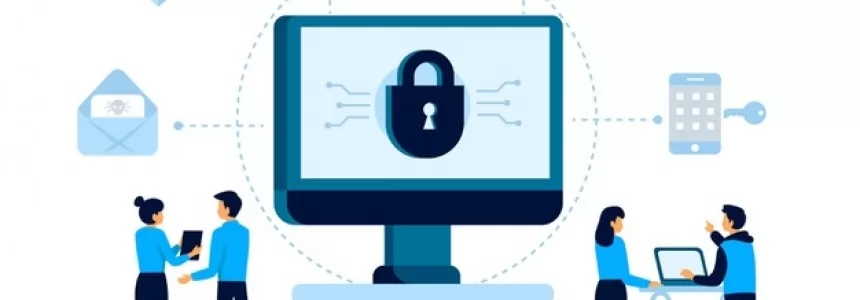
Cybersecurity and Data Privacy: Why It Is So Important
Category : Security 26-02-2021 by Janeth Kent
Dark Web: the creepy side of the Internet is not as dark as believed
Category : Security 17-05-2023 by Silvia Mazzetta
Some Neat Ways to Improve Your Internet Browsing Experience?
Category : News and events 21-12-2020 by Janeth Kent
How to block any website with a password from your browser
Category : News and events 30-09-2020 by Silvia Mazzetta
How to securely access the Dark Web in 15 steps. Second part
Category : Security 08-03-2024 by Janeth Kent
How to securely access the Dark Web in 15 steps. First part
Category : Security 08-03-2024 by Silvia Mazzetta
What cybersecurity professionals have learned from the lockdown experience
Category : Security 26-08-2020 by Silvia Mazzetta
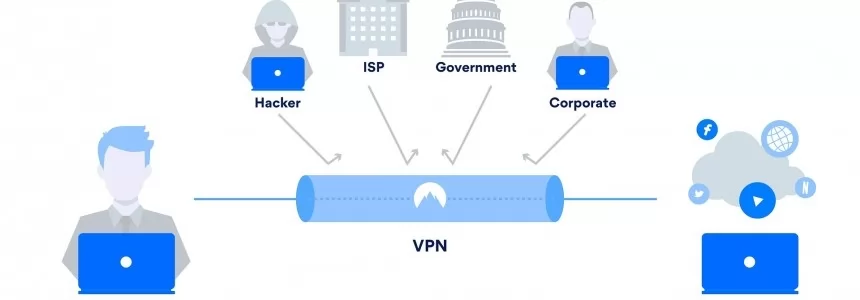
Browse safely and privately from your mobile phone using a VPN
Category : Security 25-08-2020 by Janeth Kent
How to configure Tor to browse the deep web safely
Category : Security 12-08-2020 by Silvia Mazzetta
How to get notified when one of your WhatsApp contact is online
Category : Software 15-06-2020 by Silvia Mazzetta
Onion Search Engine: How to browse the Deep Web without Tor
Category : Security 25-05-2020 by Janeth Kent
How to get into the Deep Web: a guide to access TOR, ZeroNet, Freenet and I2P
Category : Security 07-05-2020 by Janeth Kent
What is Google My Business and how does it help my local business?
Category : Web marketing 02-05-2020 by Luigi Nori
Facebook: how to remove hidden data and personal information
Category : Social networks 20-04-2020 by Silvia Mazzetta
The best websites of the Tor Deep Web and Dark Web Network
Category : Security 03-11-2022 by Janeth Kent
Easy Face and hand tracking browser detection with TensorFlow.js AI and MediaPipe
Category : Programming 09-04-2020 by Luigi Nori
How to find everything you need on the Deep Web and the Dark Web
Category : Security 10-05-2021 by Silvia Mazzetta
How to see the websites visited during the incognito mode and delete them
Category : Security 21-02-2020 by Silvia Mazzetta
How They Can Hack You While Navigating: Protecting Your Digital Security
Category : Security 23-06-2023 by Silvia Mazzetta
10 Collaborative Coding Tools for Remote Pair Programming
Category : Development 02-03-2020 by Janeth Kent
Configuring DNS-over-TLS and DNS-over-HTTPS with any DNS Server
Category : Networking 27-12-2018 by Janeth Kent
Vuejs and GDPR : how to be compliant with new EU regulations
Category : Javascript 21-09-2018 by Janeth Kent
Ubuntu servers security: 25 security tools to armor your system
Category : Servers 14-09-2016 by Janeth Kent
Guide: Install Free SSL Certificate On Your Website with Let's Encrypt
Category : Networking 09-05-2020 by Janeth Kent
The Best Free SSH Tabbed Terminal Clients for Windows
Category : Networking 18-12-2023 by Janeth Kent
The Future of Web Browsing: Liberating Content from the Confines of Space
Category : News and events 28-06-2023 by Janeth Kent
Which apps have access to your online profiles? Check it with MyPermissions app
Category : Software 26-06-2013 by Janeth Kent
A Big Deal for Brands: Instagram Adds an Identity Layer
Category : Web marketing 03-05-2013 by Janeth Kent
Transform A Simple Website in Vibrant Ecommerce Portal
Category : Web design 04-05-2020 by Silvia Mazzetta