72 results for: encrypt
Is AI sexist? A gender perspective in Robotics and Artificial Intelligence
Category : News and events 22-05-2023 by Silvia Mazzetta
The ultimate cybersecurity checklist for programmers
Category : Security 02-06-2023 by Silvia Mazzetta
How To Use Varnish As A Highly Available Load Balancer On Ubuntu 20.04 With SSL
Category : Servers 25-04-2021 by Janeth Kent
Cybersecurity and Data Privacy: Why It Is So Important
Category : Security 26-02-2021 by Janeth Kent
How to prevent your neighbor from hacking your Chromecast
Category : Networking 26-10-2020 by Luigi Nori
How to securely access the Dark Web in 15 steps. Second part
Category : Security 08-03-2024 by Janeth Kent
How to securely access the Dark Web in 15 steps. First part
Category : Security 08-03-2024 by Silvia Mazzetta
How to install a Linux partition on a Windows 10 PC
Category : Operating systems 06-09-2020 by Luigi Nori
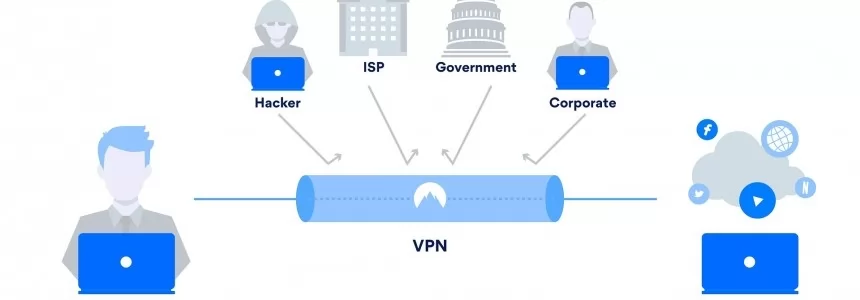
Browse safely and privately from your mobile phone using a VPN
Category : Security 25-08-2020 by Janeth Kent
How to get into the Deep Web: a guide to access TOR, ZeroNet, Freenet and I2P
Category : Security 07-05-2020 by Janeth Kent
The best websites of the Tor Deep Web and Dark Web Network
Category : Security 03-11-2022 by Janeth Kent
How to setup Free Let’s Encrypt SSL certificates with ISPConfig 3
Category : Servers 03-12-2019 by Luigi Nori
RCS: Everything you need to know about the successor to the SMS
Category : Mobile 18-06-2019 by Janeth Kent
10 Collaborative Coding Tools for Remote Pair Programming
Category : Development 02-03-2020 by Janeth Kent
Configuring DNS-over-TLS and DNS-over-HTTPS with any DNS Server
Category : Networking 27-12-2018 by Janeth Kent
How to install Letsencrypt Certificates with Certbot in Ubuntu
Category : Servers 09-05-2020 by Janeth Kent
How to Set up a Fully Functional Mail Server on Ubuntu 16.04 with iRedMail
Category : Networking 30-03-2023 by Janeth Kent
How to Connect to a Remote Server via SSH from a Linux Shell
Category : Servers 16-02-2017 by Janeth Kent
Ubuntu servers security: 25 security tools to armor your system
Category : Servers 14-09-2016 by Janeth Kent
Install Syncthing on Ubuntu 16.04 using Debian Repository
Category : Servers 19-08-2016 by Janeth Kent
Guide: Install Free SSL Certificate On Your Website with Let's Encrypt
Category : Networking 09-05-2020 by Janeth Kent
How to Configure Cloudflare Flexible SSL with WordPress website
Category : Servers 03-12-2015 by Janeth Kent
The Best Free SSH Tabbed Terminal Clients for Windows
Category : Networking 18-12-2023 by Janeth Kent
How to Create a .ONION Website and Domain With Tor Network
Category : Networking 02-11-2014 by Janeth Kent
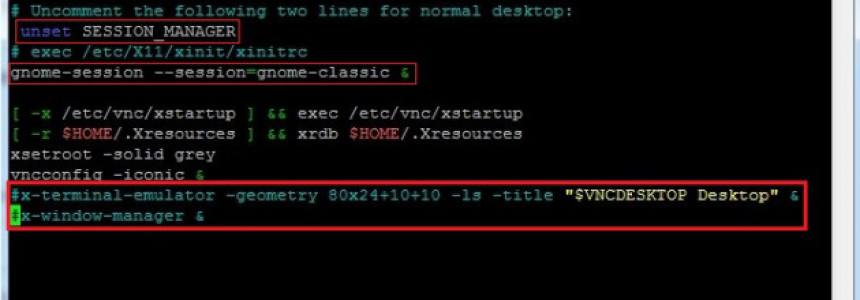
Setup VNC server for remote desktop management in Ubuntu 12.04
Category : Networking 24-04-2013 by Janeth Kent