Finally a new generation protocol with a lot of new features

In the second quarter of 2019, Wi-Fi Alliance decided to release the new version of Wi-Fi protocol, innovative already from the name. In fact, if the previous standards had incomprehensible names like IEEE 802.11a, IEEE802.11n and so on, the new protocol is called Wi-Fi 6.
This standard introduces some new features. Let's find out more.
Speed
With every new version of the protocol, the theorical maximum speed increases and this is true also for Wi-Fi 6. The maximum speed is about 9,6Gbps (about three times higher than IEEE 802.11ac).
Practically, we will never see this high speed, since the geographic distance from the devices, interferences that become unavoidable significantly reduce performance.
Checking on the download speed, no difference will be noticed comparing to the previous version. In fact, speed is not the best feature of Wi-Fi 6.
Number of managable devices
A great weakness of the previous versions was the management of a high number of devices. Symptom of this fact is that, at the time when you were going to connect multiple devices to the network, the performance decreased significantly. Until the devices were few, this has never been a problem.
With the increase of devices connected to the Internet, having a protocol that allows to manage a higher number of devices is essential. Let's think about a home, where 4 people leave. Everyone could have a smartphone and maybe a laptop. There could be two smart-tv and a couple of TV-box. If we imagine that a video surveillance system and other devices like tablets, the number of devices increases out of proportion.
Wi-Fi 6 can manage a lot of devices thanks to two technologies:
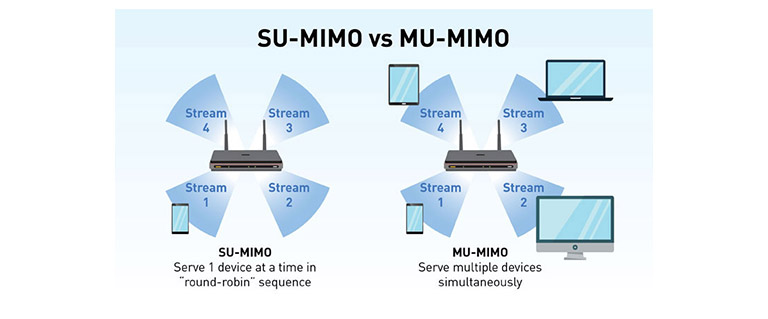
- MU-MIMO: acronym of Multi User Multiple In Multiple Out stands for the maximum number of devices the router can communicate with. Theorically, Wi-Fi 6 can manage 8 devices at a time without compromising performance. Despite of the high number of advantages, it has his own negative sides. In fact it takes some time to adapt every device to the new technology. Furthermore a detail comes up: MU-MIMO signals are spreaded on a directional base, so client-router or router-client. If two devices that are connected both to the same router are really close to each other, they would shre the same channel, losing the advantages of a MU-MIMO connection.
The images explain quite clearly the difference between MU-MIMO and its opposite SU-MIMO acronym of Single User Multiple In Multiple Out.
- OFDMA: acronym of Orthogonal Frequency Division Multiple Access stands for the capacity of dividing every channel into several sub-channels, optimizing the bandwidth with more devices at a time. The idea is to allow the access point to communicate simultaneously with more than one device, dividing the channel in sub-channels and giving each interlocutor a specific sub-channel, so the overhead decreases significantly.
So, Wi-Fi 6 won't let us download faster a film from our NAS, but it will allows us to watch more than one film at a time.
Wi-Fi 6's security
Last but not least, security sector.
Noteworthy is the introduction of WPA3. It is very interesting because it simplifies the authentication procedure that was very complex until the previous version and above all it uses the individual encryption for each communication. The protection from the brute force attacks has been increased.
Despite all of these improvements, the protocol can still be improved even if it is decidedly better than the previous one.
A little defect is that the presence of WPA3 isn't compulsory, since some devices could not prop up it.
Wi-Fi 6's other features
- A very interesting thing is that, belonging to the evaluation, Wi-Fi 6 can reduce energetic costs due to the data transfer. That's because the protocol is better optimizet than the previous one.
- Another noteworthy feature is the TWT function, acronym of Target Wake Time, thanks to which the access point can establish a timed communication with every client.
There is a double advantage: gadgets can be "woken up" according to certains intervals avoiding a continuos connection saving battery. On the other hand the bandwidth is optimized since we can avoid two devices to communicate at the same time. - Nowadays, the only Wi-Fi 6 compatible smartphone is Samsung Galaxy S10, while Lenovo announced that some devices will manmage the new standard. Dealing with routers, Asus, Netgear and TP-link produced compatible devices. Cisco is also equipped.
Definetly, how can I use Wi-Fi 6?
We will have to buy new devices, since the new versions of new protocol are realeased only with the new hardware. Must be precised that, even if we buy a smartphone with Wi-Fi 6 compatibility but the router has no compatibility with the standard, we will carry on using IEEE802.11ac.
Some final considerations
If one one hand Wi-Fi 6 promises remarkable improvements, on the other hand it isn't necessary to hurry to go and buy new devices that support the new standard, mostly because in the common use of the Internet, we won't notice any difference. If the perspective is that of home automation or massive file-sharing buying new devices could help, in terms of bandwidth optimization and security.
Dealing with the economic side,buying new devices could be good if we are renovating our home and then we have to buy the new equipment or if we need to trash our old router.If we have got a relatively new router and needs of "average user", change devices could not be convenient.
If Wi-Fi 6 is a top or a flop, we'll see it over time and maybe, as with a lot of things, we'll understand with the release of the next version. Nowadays it seems to be a valid replacement to IEEE 802.11ac ![]() .
.

