65 results for: promise
How to include a JavaScript file in another JavaScript file
Category : Javascript 25-09-2024 by Janeth Kent
The Payment Request API: Revolutionizing Online Payments (Part 1)
Category : Javascript 12-06-2023 by Silvia Mazzetta
How do you stop JavaScript execution for a while: sleep()
Category : Javascript 31-05-2023 by Janeth Kent
JavaScript Arrow functions: What they are and how to use them
Category : Javascript 30-08-2021 by Janeth Kent
The ultimate cybersecurity checklist for programmers
Category : Security 02-06-2023 by Silvia Mazzetta
A FULFILLED PROMISE - Using the FETCH API to make AJAX calls
Category : Javascript 26-12-2020 by Iveta Karailievova
Making AJAX requests to a REST API using vanilla JavaScript and XHR
Category : Javascript 25-11-2020 by Iveta Karailievova
The BleedingTooth vulnerability and other Bluetooth security risks
Category : Security 10-11-2020 by Iveta Karailievova
What's the Difference between Google TV and Android TV?
Category : Software 27-10-2020 by Silvia Mazzetta
How to securely access the Dark Web in 15 steps. Second part
Category : Security 08-03-2024 by Janeth Kent
How to securely access the Dark Web in 15 steps. First part
Category : Security 08-03-2024 by Silvia Mazzetta
How to configure Tor to browse the deep web safely
Category : Security 12-08-2020 by Silvia Mazzetta
JavaScript: Promises explained with simple real life examples
Category : Javascript 06-05-2020 by Janeth Kent
Web shells as a security thread for web applications
Category : Security 04-05-2020 by Iveta Karailievova
How to find everything you need on the Deep Web and the Dark Web
Category : Security 10-05-2021 by Silvia Mazzetta
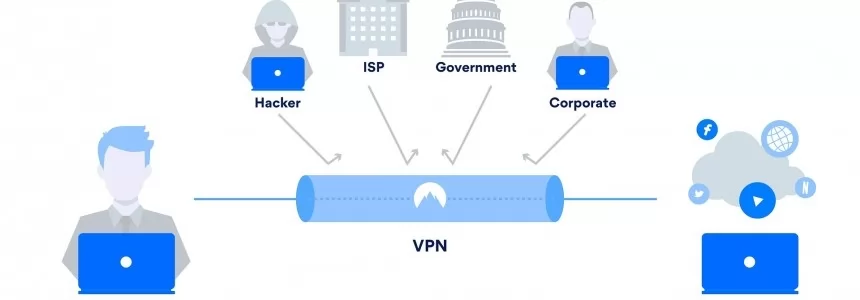
How They Can Hack You While Navigating: Protecting Your Digital Security
Category : Security 23-06-2023 by Silvia Mazzetta
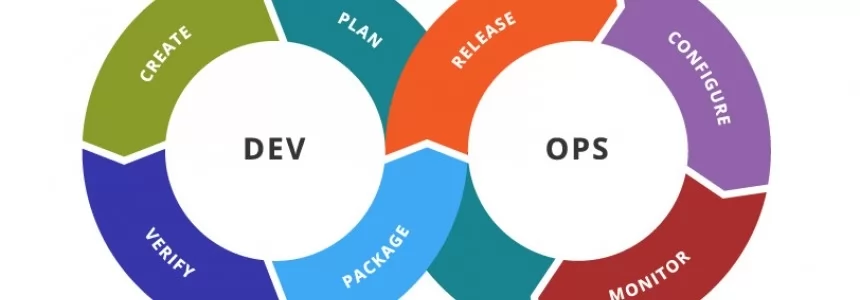
DevOps, Agile Operations, and Continuous Delivery
Category : Programming 26-09-2019 by Silvia Mazzetta
Understanding the JavaScript language (guidelines for beginners)
Category : Javascript 18-06-2019 by Janeth Kent
RCS: Everything you need to know about the successor to the SMS
Category : Mobile 18-06-2019 by Janeth Kent
The Steps to Take if You're the Victim of a Cyber Hack
Category : News and events 27-03-2019 by Janeth Kent
Is JavaScript imperative for Cross-Platform Development?
Category : Programming 09-03-2019 by Janeth Kent
Vuejs and GDPR : how to be compliant with new EU regulations
Category : Javascript 21-09-2018 by Janeth Kent
Fetch API, an amazing replacement of XMLHttpRequest AJAX
Category : Programming 19-02-2017 by Janeth Kent
Ubuntu servers security: 25 security tools to armor your system
Category : Servers 14-09-2016 by Janeth Kent
Guide: Install Free SSL Certificate On Your Website with Let's Encrypt
Category : Networking 09-05-2020 by Janeth Kent
The Future of Web Browsing: Liberating Content from the Confines of Space
Category : News and events 28-06-2023 by Janeth Kent
Top Alternatives to Google Adsense (ideal for small publishers)
Category : Web marketing 15-06-2020 by Silvia Mazzetta
Mastering JavaScript: Top Resources to Propel Your Learning Journey
Category : Javascript 23-06-2023 by Janeth Kent
Streamline your business with the top Invoicing Software Solutions
Category : Web marketing 14-06-2023 by Janeth Kent
Super Stealthy Backdoor Spreads To Hit Hundreds Of Thousands Of Web Users
Category : Security 09-05-2013 by Janeth Kent
WARNING: New Malware Threat in Twitter's Topics
Category : News and events 23-04-2013 by Janeth Kent
20 Best Wireframing Tools for Web Designers and Developers
Category : Web design 11-04-2013 by Janeth Kent