46 results for: authentication
The ultimate cybersecurity checklist for programmers
Category : Security 02-06-2023 by Silvia Mazzetta
Deepfakes Detection – An Emerging Technological Challenge
Category : Technology 27-01-2021 by Iveta Karailievova
The best tricks and features to master your Android Smart TV
Category : Networking 05-11-2020 by Luigi Nori
Web shells as a security thread for web applications
Category : Security 04-05-2020 by Iveta Karailievova
Cross-Origin Resource Sharing (CORS) and examples of XSS and CSRF
Category : Javascript 30-01-2020 by Luigi Nori
Superior React-Native Courses for Mobile Application Developers
Category : Programming 24-11-2019 by Janeth Kent
How to Set up a Fully Functional Mail Server on Ubuntu 16.04 with iRedMail
Category : Networking 30-03-2023 by Janeth Kent
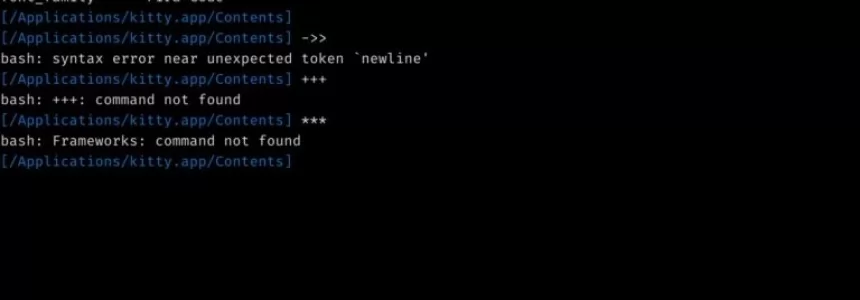
Useful Terminal Commands Every Web Developer Should Know About
Category : Operating systems 22-06-2018 by Janeth Kent
Send Push Notification to Users Using Firebase Messaging Service in PHP
Category : Php 14-05-2018 by Janeth Kent
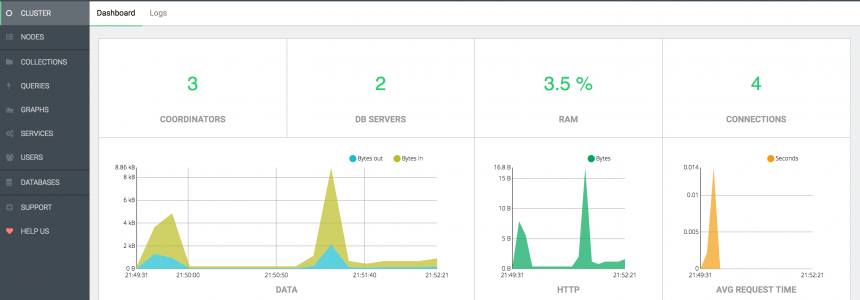
ArangoDB, install and configure the popular Database in ubuntu 16.04
Category : Databases 14-11-2017 by Janeth Kent
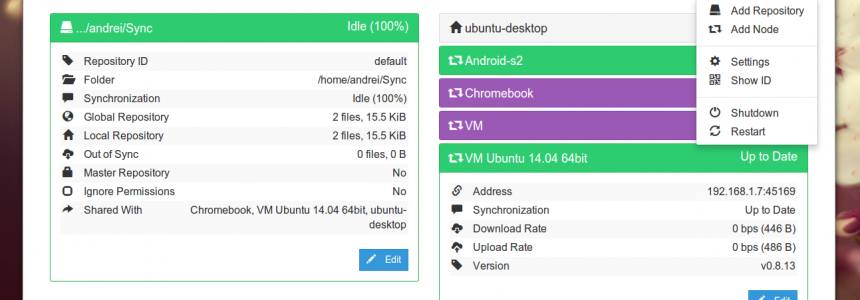
Install Syncthing on Ubuntu 16.04 using Debian Repository
Category : Servers 19-08-2016 by Janeth Kent
The Best Free SSH Tabbed Terminal Clients for Windows
Category : Networking 18-12-2023 by Janeth Kent
How to Retrieve Twitter Timeline and Hashtags in PHP
Category : Programming 12-07-2013 by Janeth Kent
20 Open Source Scripts Applications for Web Developers
Category : Programming 11-08-2016 by Janeth Kent
WARNING: New Malware Threat in Twitter's Topics
Category : News and events 23-04-2013 by Janeth Kent
How to install LAMP (Linux,Apache,Mysql,Php) in Ubuntu 12.10
Category : Networking 11-04-2013 by Janeth Kent