68 results for: attacks
The ultimate cybersecurity checklist for programmers
Category : Security 02-06-2023 by Silvia Mazzetta
htaccess Rules to Help Protect from SQL Injections and XSS
Category : Security 01-03-2021 by Janeth Kent
Cybersecurity and Data Privacy: Why It Is So Important
Category : Security 26-02-2021 by Janeth Kent
Some Neat Ways to Improve Your Internet Browsing Experience?
Category : News and events 21-12-2020 by Janeth Kent
The BleedingTooth vulnerability and other Bluetooth security risks
Category : Security 10-11-2020 by Iveta Karailievova
How to prevent your neighbor from hacking your Chromecast
Category : Networking 26-10-2020 by Luigi Nori
What cybersecurity professionals have learned from the lockdown experience
Category : Security 26-08-2020 by Silvia Mazzetta
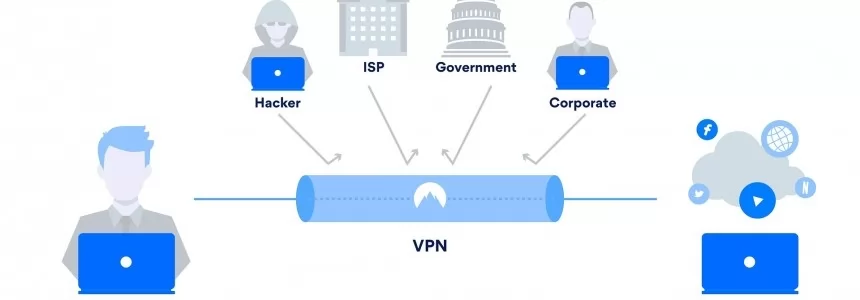
Browse safely and privately from your mobile phone using a VPN
Category : Security 25-08-2020 by Janeth Kent
The 6 Essentials for Creating a Visually Appealing Web Design
Category : Web design 25-08-2020 by Silvia Mazzetta
How to configure Tor to browse the deep web safely
Category : Security 12-08-2020 by Silvia Mazzetta
Why do you vote the way you do in the age of misinformation and fake news?
Category : News and events 11-06-2020 by Silvia Mazzetta
Web shells as a security thread for web applications
Category : Security 04-05-2020 by Iveta Karailievova
Cross-Origin Resource Sharing (CORS) and examples of XSS and CSRF
Category : Javascript 30-01-2020 by Luigi Nori
How They Can Hack You While Navigating: Protecting Your Digital Security
Category : Security 23-06-2023 by Silvia Mazzetta
Features you will get in EaseUS data recovery software
Category : Software 25-06-2019 by Janeth Kent
Configuring DNS-over-TLS and DNS-over-HTTPS with any DNS Server
Category : Networking 27-12-2018 by Janeth Kent
How to Configure the Mod_Security Core Ruleset in Ubuntu
Category : Servers 04-03-2017 by Janeth Kent
Ubuntu servers security: 25 security tools to armor your system
Category : Servers 14-09-2016 by Janeth Kent
How to Configure Cloudflare Flexible SSL with WordPress website
Category : Servers 03-12-2015 by Janeth Kent
Speed up your site and protect it against DDOS attacks with CloudFlare
Category : Networking 23-07-2014 by Luigi Nori
Install and Configure Varnish with Apache multiple Virtual Hosts on Ubuntu 12.10
Category : Networking 21-06-2013 by Janeth Kent
Million of visitors per day with a super cheap php mysql server using nginx and varnish
Category : Networking 28-05-2013 by Janeth Kent
Mobile Malware Targets Android Phones: new Kaspersky Lab report
Category : Security 23-05-2013 by Janeth Kent
8 Things That Anonymous, The Hacker 'Terrorist' Group, Has Done For Good
Category : Security 29-04-2013 by Janeth Kent
Penguin 2.0 Forewarning: The Google Perspective on Links
Category : Web marketing 11-04-2013 by Janeth Kent
A list of Great PHP libraries and classes you should know
Category : Programming 26-03-2021 by Janeth Kent