55 results for: emails
How to download an email in PDF format in Gmail for Android
Category : Technology 16-05-2023 by Janeth Kent
How to set up your Android phone: learn how to get your new phone up and running
Category : Mobile 28-04-2021 by Janeth Kent
Some Neat Ways to Improve Your Internet Browsing Experience?
Category : News and events 21-12-2020 by Janeth Kent
The BleedingTooth vulnerability and other Bluetooth security risks
Category : Security 10-11-2020 by Iveta Karailievova
How to securely access the Dark Web in 15 steps. Second part
Category : Security 08-03-2024 by Janeth Kent
Suggestions to Improve the Efficiency of a Small Business
Category : Web marketing 26-07-2025 by Janeth Kent
7 Killer Strategies to Increase Your Sales Funnel Conversion Rates
Category : Web marketing 23-07-2020 by Janeth Kent
How to get into the Deep Web: a guide to access TOR, ZeroNet, Freenet and I2P
Category : Security 07-05-2020 by Janeth Kent
The best websites of the Tor Deep Web and Dark Web Network
Category : Security 03-11-2022 by Janeth Kent
How to find everything you need on the Deep Web and the Dark Web
Category : Security 10-05-2021 by Silvia Mazzetta
How to Build Your eCommerce's Email List Using Instagram
Category : Web marketing 06-12-2019 by Luigi Nori
How They Can Hack You While Navigating: Protecting Your Digital Security
Category : Security 23-06-2023 by Silvia Mazzetta
What to Expect from Email Marketing Tools in 2019
Category : Web marketing 18-11-2019 by Janeth Kent
The Steps to Take if You're the Victim of a Cyber Hack
Category : News and events 27-03-2019 by Janeth Kent
The Most Useful 50 Web Sites you wish you knew earlier
Category : Web marketing 13-06-2020 by Janeth Kent
80 Linux Network Monitor Software & Tools for Managing & Monitoring Unix/Linux Systems
Category : Security 23-10-2018 by Janeth Kent
Four of the Biggest Reasons Your Emails are Sent to Spam
Category : Web marketing 14-08-2018 by Janeth Kent
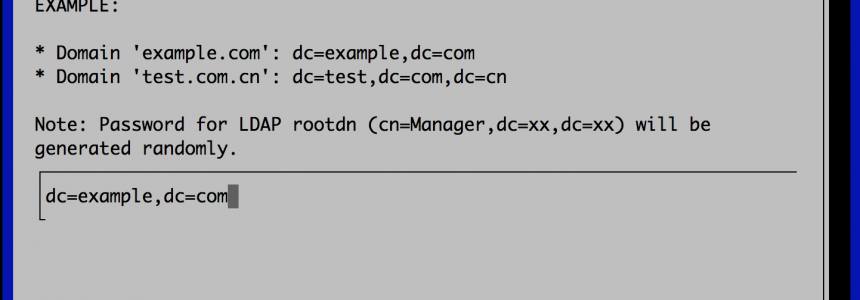
How to Set up a Fully Functional Mail Server on Ubuntu 16.04 with iRedMail
Category : Networking 30-03-2023 by Janeth Kent
A Guide to Integrate Social Media into Your E-Commerce Store
Category : News and events 09-07-2018 by Janeth Kent
How Our Relationship with the Internet has Changed in the Last 20 Years
Category : News and events 29-04-2021 by Janeth Kent
5 best open source version control systems tools for sysadmins
Category : Software 13-05-2017 by Janeth Kent
An Introduction to Email Segmentation: Boosting Engagement and Personalization
Category : Web marketing 23-06-2023 by Janeth Kent
The Best Lightweight Linux Distributions For Older PC's
Category : Operating systems 12-03-2017 by Janeth Kent
WebDev:32 New Tools and Services for Web Developers
Category : Programming 28-11-2013 by Janeth Kent
How Companies can Drive Engagement with Blogs: 50 tips
Category : Web marketing 21-08-2013 by Janeth Kent
A Guide To Understanding Structured Data and Schema Markup
Category : Programming 21-06-2023 by Janeth Kent
Android tips: How to change archive and delete actions in the new Gmail
Category : Operating systems 11-06-2013 by Janeth Kent
Streamline your business with the top Invoicing Software Solutions
Category : Web marketing 14-06-2023 by Janeth Kent
8 Things That Anonymous, The Hacker 'Terrorist' Group, Has Done For Good
Category : Security 29-04-2013 by Janeth Kent