63 results for: protocol
Transitioning from a Home Office to a Virtual Office
Category : Web marketing 08-03-2024 by Janeth Kent
The Importance of Maintaining a Crisis-Ready Social Media Strategy: A Closer Look
Category : Social networks 01-06-2023 by Janeth Kent
The ultimate cybersecurity checklist for programmers
Category : Security 02-06-2023 by Silvia Mazzetta
How to make the website's dark mode persistent with Local Storage, CSS and JS
Category : Css 22-12-2020 by
The BleedingTooth vulnerability and other Bluetooth security risks
Category : Security 10-11-2020 by Iveta Karailievova
Why You Should Hire Node.js Developer for Your Backend Development
Category : Javascript 27-10-2020 by Luigi Nori
What cybersecurity professionals have learned from the lockdown experience
Category : Security 26-08-2020 by Silvia Mazzetta
The best websites of the Tor Deep Web and Dark Web Network
Category : Security 03-11-2022 by Janeth Kent
Cross-Origin Resource Sharing (CORS) and examples of XSS and CSRF
Category : Javascript 30-01-2020 by Luigi Nori
How They Can Hack You While Navigating: Protecting Your Digital Security
Category : Security 23-06-2023 by Silvia Mazzetta
RCS: Everything you need to know about the successor to the SMS
Category : Mobile 18-06-2019 by Janeth Kent
Unlock Hidden SmartPhone Features with these Secret Codes
Category : Security 26-07-2025 by Janeth Kent
Configuring DNS-over-TLS and DNS-over-HTTPS with any DNS Server
Category : Networking 27-12-2018 by Janeth Kent
80 Linux Network Monitor Software & Tools for Managing & Monitoring Unix/Linux Systems
Category : Security 23-10-2018 by Janeth Kent
How to install Letsencrypt Certificates with Certbot in Ubuntu
Category : Servers 09-05-2020 by Janeth Kent
Useful Terminal Commands Every Web Developer Should Know About
Category : Operating systems 22-06-2018 by Janeth Kent
The best Free and Open-Source Video editing, VFX and compositing software
Category : Multimedia 01-03-2021 by Janeth Kent
5 best open source version control systems tools for sysadmins
Category : Software 13-05-2017 by Janeth Kent
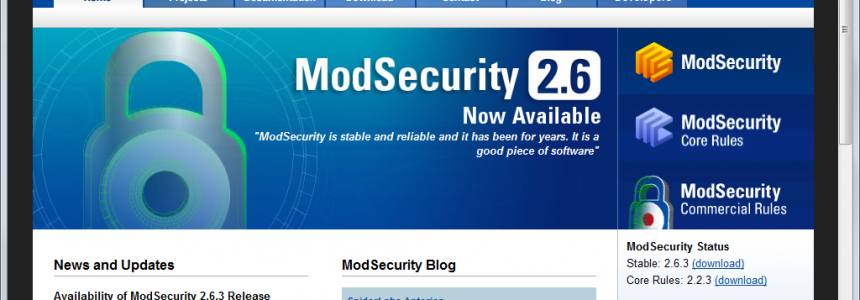
How to Configure the Mod_Security Core Ruleset in Ubuntu
Category : Servers 04-03-2017 by Janeth Kent
How to Connect to a Remote Server via SSH from a Linux Shell
Category : Servers 16-02-2017 by Janeth Kent
Ubuntu servers security: 25 security tools to armor your system
Category : Servers 14-09-2016 by Janeth Kent
The Best Free SSH Tabbed Terminal Clients for Windows
Category : Networking 18-12-2023 by Janeth Kent
How to Parse URLs with JavaScript: the The Easiest Way
Category : Javascript 20-08-2013 by Janeth Kent
The Future of Web Browsing: Liberating Content from the Confines of Space
Category : News and events 28-06-2023 by Janeth Kent
Ubuntu UFW Firewall - Uncomplicated Firewall for Ubuntu
Category : Networking 27-05-2013 by Janeth Kent
Setup VNC server for remote desktop management in Ubuntu 12.04
Category : Networking 24-04-2013 by Janeth Kent