59 results for: logging
Sick of Video Games? Here are Some Other Pastimes to Try
Category : Technology 29-11-2022 by Janeth Kent
The ultimate cybersecurity checklist for programmers
Category : Security 02-06-2023 by Silvia Mazzetta
How to hide the you are typing text in a WhatsApp group
Category : Social networks 25-03-2021 by Janeth Kent
htaccess Rules to Help Protect from SQL Injections and XSS
Category : Security 01-03-2021 by Janeth Kent
How to make the website's dark mode persistent with Local Storage, CSS and JS
Category : Css 22-12-2020 by
Website Traffic Getting Low? 4 Immediate Action to Take
Category : Web marketing 04-12-2020 by Luigi Nori
What Are The Best Methods to Make Money Online
Category : Web marketing 12-06-2020 by Silvia Mazzetta
How to Gain an Edge and Improve Your Engagement Rate on Instagram
Category : Social networks 20-11-2019 by Silvia Mazzetta
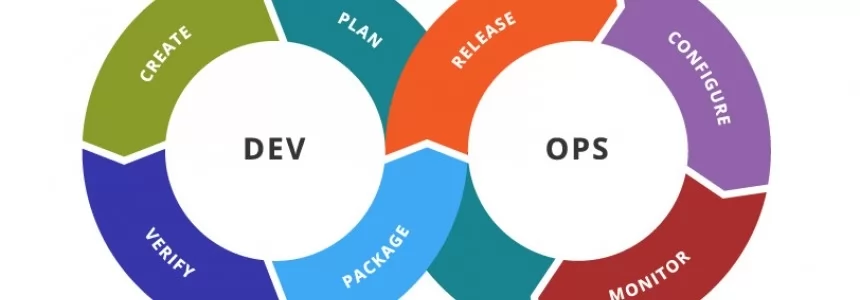
DevOps, Agile Operations, and Continuous Delivery
Category : Programming 26-09-2019 by Silvia Mazzetta
5 Ways to Effectively Market Your Online Business
Category : Web marketing 22-04-2020 by Janeth Kent
Unlock Hidden SmartPhone Features with these Secret Codes
Category : Security 26-07-2025 by Janeth Kent
80 Linux Network Monitor Software & Tools for Managing & Monitoring Unix/Linux Systems
Category : Security 23-10-2018 by Janeth Kent
Useful Terminal Commands Every Web Developer Should Know About
Category : Operating systems 22-06-2018 by Janeth Kent
The Importance of Other People to the Success of Your Website
Category : Web marketing 27-02-2018 by Janeth Kent
How Our Relationship with the Internet has Changed in the Last 20 Years
Category : News and events 29-04-2021 by Janeth Kent
Ubuntu servers security: 25 security tools to armor your system
Category : Servers 14-09-2016 by Janeth Kent
Free PHP, HTML, CSS, JavaScript editor (IDE) - Codelobster PHP Edition
Category : Software 16-01-2014 by Janeth Kent
20 Open Source Scripts Applications for Web Developers
Category : Programming 11-08-2016 by Janeth Kent
Million of visitors per day with a super cheap php mysql server using nginx and varnish
Category : Networking 28-05-2013 by Janeth Kent
Ubuntu UFW Firewall - Uncomplicated Firewall for Ubuntu
Category : Networking 27-05-2013 by Janeth Kent
Thousands of Tumblr blogs migrate to Wordpress after Yahoo deal
Category : News and events 20-05-2013 by Janeth Kent
50 Top Tools for Social Media Monitoring, Analytics, and Management
Category : Social networks 15-05-2013 by Janeth Kent
Google+ Resources to Help You Create a Strategy for Success
Category : Social networks 03-05-2013 by Janeth Kent
The Best Experimental Chrome Features You Should Check Out
Category : Software 24-04-2013 by Janeth Kent
13 Ways to Drive More Website Traffic from Your Facebook Page
Category : Web marketing 24-04-2013 by Janeth Kent
Reset Linux root password without knowing the password
Category : Operating systems 30-04-2021 by Janeth Kent