38 results for: messaging
Transitioning from a Home Office to a Virtual Office
Category : Web marketing 08-03-2024 by Janeth Kent
The Importance of Maintaining a Crisis-Ready Social Media Strategy: A Closer Look
Category : Social networks 01-06-2023 by Janeth Kent
How to have two WhatsApp accounts on your Dual SIM phone
Category : Software 25-01-2021 by Luigi Nori
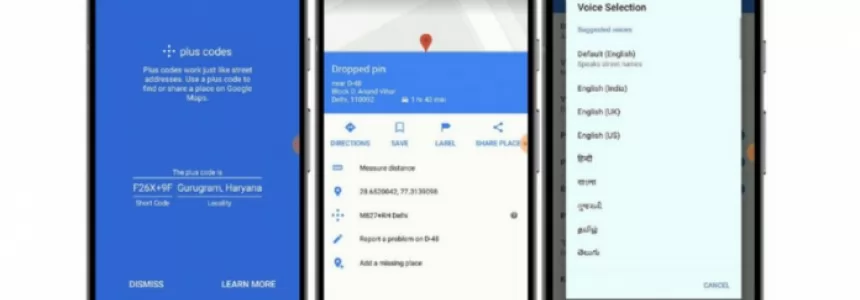
How to share your location using Plus codes on Google Maps for Android
Category : Technology 17-05-2023 by Janeth Kent
How to securely access the Dark Web in 15 steps. Second part
Category : Security 08-03-2024 by Janeth Kent
Browse safely and privately from your mobile phone using a VPN
Category : Security 25-08-2020 by Janeth Kent
How to get notified when one of your WhatsApp contact is online
Category : Software 15-06-2020 by Silvia Mazzetta
The best websites of the Tor Deep Web and Dark Web Network
Category : Security 03-11-2022 by Janeth Kent
Best Free Image Optimization Tools for Image Compression
Category : Software 27-03-2020 by Janeth Kent
RCS: Everything you need to know about the successor to the SMS
Category : Mobile 18-06-2019 by Janeth Kent
Unlock Hidden SmartPhone Features with these Secret Codes
Category : Security 26-07-2025 by Janeth Kent
The Meaning of Colors in web Design. A little bit of psychology
Category : Web design 05-08-2019 by Janeth Kent
Whatsapp is working to a new sales system integrated in the app
Category : Technology 28-11-2018 by Janeth Kent
Send Push Notification to Users Using Firebase Messaging Service in PHP
Category : Php 14-05-2018 by Janeth Kent
The Best Lightweight Linux Distributions For Older PC's
Category : Operating systems 12-03-2017 by Janeth Kent
8 Social Tools to interact with Customers and improve CX
Category : Social networks 22-07-2016 by Janeth Kent
The importance of building a responsive website and targeting the mobile audience
Category : Web design 15-06-2020 by Silvia Mazzetta
What is a growth hacker? The actual difference between growth hacking and marketing
Category : Web marketing 22-05-2013 by Janeth Kent
50 Top Tools for Social Media Monitoring, Analytics, and Management
Category : Social networks 15-05-2013 by Janeth Kent