33 results for: detection
Deepfakes Detection – An Emerging Technological Challenge
Category : Technology 27-01-2021 by Iveta Karailievova
How to securely access the Dark Web in 15 steps. First part
Category : Security 08-03-2024 by Silvia Mazzetta
Awesome JavaScript Games and Js Software to create Games
Category : Javascript 30-06-2020 by Janeth Kent
Web shells as a security thread for web applications
Category : Security 04-05-2020 by Iveta Karailievova
Easy Face and hand tracking browser detection with TensorFlow.js AI and MediaPipe
Category : Programming 09-04-2020 by Luigi Nori
80 Linux Network Monitor Software & Tools for Managing & Monitoring Unix/Linux Systems
Category : Security 23-10-2018 by Janeth Kent
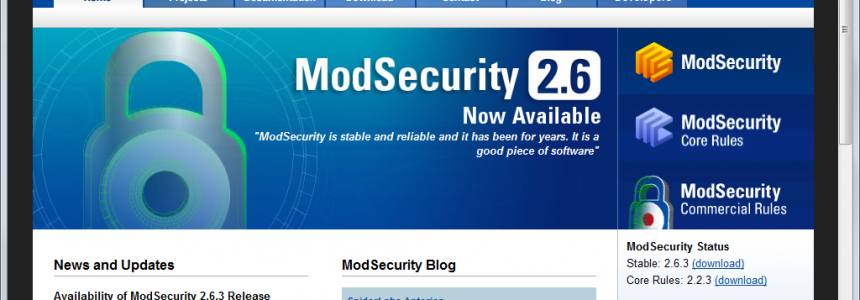
How to Configure the Mod_Security Core Ruleset in Ubuntu
Category : Servers 04-03-2017 by Janeth Kent
Ubuntu servers security: 25 security tools to armor your system
Category : Servers 14-09-2016 by Janeth Kent
16 fantastic examples and uses of the parallax effect
Category : Javascript 09-04-2020 by Janeth Kent
25 Useful HTML5 Tools For Web Designers & Developers
Category : Web design 29-05-2013 by Janeth Kent
Matt Cutts Talks SEO for Google: 9 Things You Should Expect This Summer
Category : Web marketing 14-05-2013 by Janeth Kent
Super Stealthy Backdoor Spreads To Hit Hundreds Of Thousands Of Web Users
Category : Security 09-05-2013 by Janeth Kent