36 results for: networking
Why E-Commerce Businesses Should be Using Cloud Computing
Category : Web marketing 01-06-2021 by Silvia Mazzetta
Browse safely and privately from your mobile phone using a VPN
Category : Security 25-08-2020 by Janeth Kent
How to configure Tor to browse the deep web safely
Category : Security 12-08-2020 by Silvia Mazzetta
How to get into the Deep Web: a guide to access TOR, ZeroNet, Freenet and I2P
Category : Security 07-05-2020 by Janeth Kent
Online Marketing Strategies for your Ecommerce
Category : Web marketing 20-04-2023 by Silvia Mazzetta
The best websites of the Tor Deep Web and Dark Web Network
Category : Security 03-11-2022 by Janeth Kent
How to find everything you need on the Deep Web and the Dark Web
Category : Security 10-05-2021 by Silvia Mazzetta
Why Becoming A Certified Scrum Master Can Launch Your Career
Category : Startups 20-06-2019 by Janeth Kent
Fetch API, an amazing replacement of XMLHttpRequest AJAX
Category : Programming 19-02-2017 by Janeth Kent
The Best Free SSH Tabbed Terminal Clients for Windows
Category : Networking 18-12-2023 by Janeth Kent
Visualize Your Data: 25 Javascript Visualization Libraries
Category : Javascript 03-05-2021 by Silvia Mazzetta
50 tools to reinvigorate your content marketing efforts
Category : Web marketing 03-07-2013 by Janeth Kent
Mastering JavaScript: Top Resources to Propel Your Learning Journey
Category : Javascript 23-06-2023 by Janeth Kent
Ubuntu UFW Firewall - Uncomplicated Firewall for Ubuntu
Category : Networking 27-05-2013 by Janeth Kent
Super Stealthy Backdoor Spreads To Hit Hundreds Of Thousands Of Web Users
Category : Security 09-05-2013 by Janeth Kent
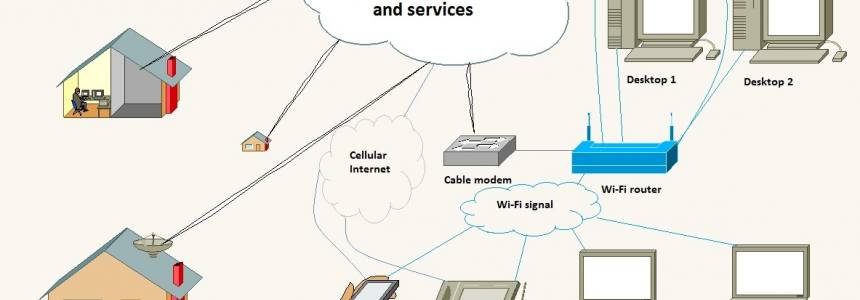
Home networking explained: How to set up a home network
Category : Software 26-04-2013 by Janeth Kent
WARNING: New Malware Threat in Twitter's Topics
Category : News and events 23-04-2013 by Janeth Kent