28 results for: injection
The ultimate cybersecurity checklist for programmers
Category : Security 02-06-2023 by Silvia Mazzetta
htaccess Rules to Help Protect from SQL Injections and XSS
Category : Security 01-03-2021 by Janeth Kent
Web shells as a security thread for web applications
Category : Security 04-05-2020 by Iveta Karailievova
Cross-Origin Resource Sharing (CORS) and examples of XSS and CSRF
Category : Javascript 30-01-2020 by Luigi Nori
80 Linux Network Monitor Software & Tools for Managing & Monitoring Unix/Linux Systems
Category : Security 23-10-2018 by Janeth Kent
How to Configure the Mod_Security Core Ruleset in Ubuntu
Category : Servers 04-03-2017 by Janeth Kent
Ubuntu servers security: 25 security tools to armor your system
Category : Servers 14-09-2016 by Janeth Kent
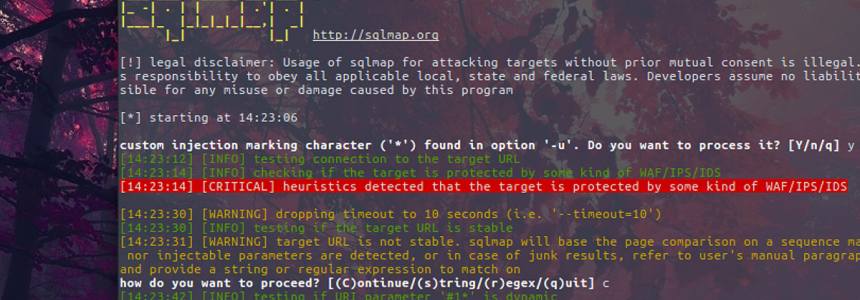
SQLMAP installation and usage in Ubuntu and Kali linux
Category : Security 13-08-2016 by Janeth Kent
PHP7: Guide and References to all the changes between version 5.x and 7 of PHP
Category : Php 27-12-2015 by Janeth Kent