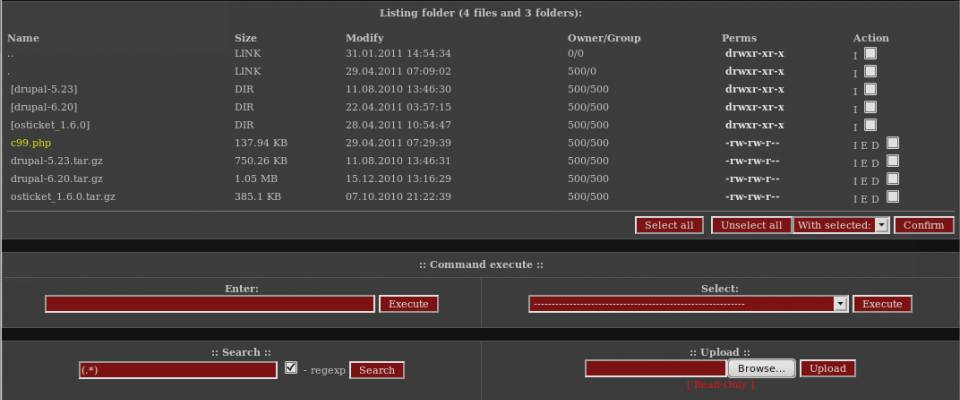
When malicious intruders compromise a web server, there's an excellent chance a famous Russian PHP script, r57shell, will follow. The r57 and C99 shell PHP script gives the intruder a number of capabilities, including, but not limited to: downloading files, uploading files, creating backdoors, setting up a spam relay, forging email, bouncing a connection to decrease the risk of being caught, and even taking control of SQL databases. All these functions become readily available through an easy to use web interface, but now you can fight back.
First, make sure you execute updatedb so find has an up to date image to search:
find /var/www/ -name "*".php -type f -print0 | xargs -0 grep r57 | uniq -c | sort -u | cut -d":" -f1 | awk '{print "rm -rf " $2}' | uniq
You can also search regular text (.txt) files:
find /var/www/ -name "*".txt -type f -print0 | xargs -0 grep r57 | uniq -c | sort -u | cut -d":" -f1 | awk '{print "rm -rf " $2}' | uniq
Or even cleverly disguised GIF image files:
find /var/www/ -name "*".gif -type f -print0 | xargs -0 grep r57 | uniq -c | sort -u | cut -d":" -f1 | awk '{print "rm -rf " $2}' | uniq
The command might appear scary, or even malicious to an inexperienced Linux admin, but here's the break down.
find /var/www/
find is a must know command when dealing with Linux. Find is what's used to perform command line file searches. The path /var/www is the directory find will search, in addition to all directories contained within www, but nothing above. For example, /var/mail is not searched. If your publicly accessible files are not contained in /var/www, then you'll obviously need to replace /var/www with the correct path.
-name "*".php -type f -print0
This portion of the command tells find to search file names (not directories) ending in .php. Anything else is ignored.
| xargs -0 grep r57
The pipe symbol ( | ) tells Linux to take the results of the first command (the PHP files we searched for), and pass them along to the second command, xargs. At this point, all located files are searched for any mention of r57, not just the file names, but the actual content within the files.
| uniq -c | sort -u
uniq will prevent duplicate results from displaying. The command is smart enough to know when multiple instances are found in a single file, resulting in a single mention instead of potentially hundreds, flooding your console with repeated messages. The -c parameter tells uniq to count the number of consecutive lines that were combined. sort will take the unordered results, and display them in some type of orderly fashion.
| cut -d":" -f1
cut will prevent the line of code that contains r57 from showing up in the results. The output is just a simple mention of the filename or names, and how many occurrences. There's no need to display the actual code if your intentions are to remove the malicious files.
| awk '{print "rm -rf " $2}'
awk, a programming language in itself, is a very powerful command with many beneficial uses. In this command, awk is instructed to print rm -rf with the file path and file name appended. Here's an example output:
rm -rf /var/www/users/domain.com/images/uploads/r57shell.php
rm -rf is used to delete files without asking questions. The, "are you sure you want to delete ..." is skipped, so be careful when using the -rf switch, it's very destructive if used without care. Notice the print portion - this means the command is only printed, not carried out.
Another popular tool is the c99shell, which I also recommend searching for. Just change three characters:
find /var/www/ -name "*".php -type f -print0 | xargs -0 grep c99 | uniq -c | sort -u | cut -d":" -f1 | awk '{print "rm -rf " $2}' | uniq
Once you've confirmed all the found files are malicious, you can easily dumb the results into a file, make the file executable, and delete the plague in one shot instead of manually deleting individual files one by one.