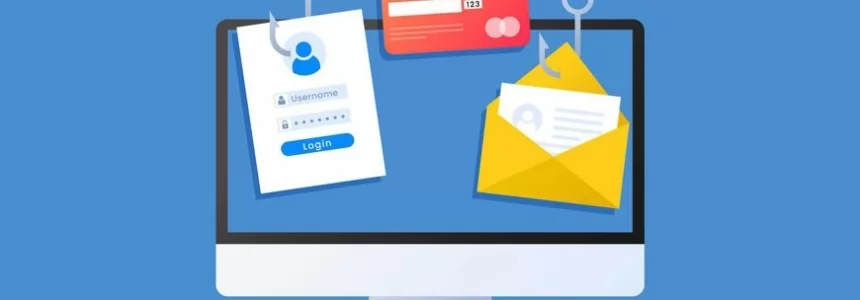
Onion Search Engine: How to browse the Deep Web without Tor
Category : Security 25-05-2020 by Janeth Kent
How to get into the Deep Web: a guide to access TOR, ZeroNet, Freenet and I2P
Category : Security 07-05-2020 by Janeth Kent
Web shells as a security thread for web applications
Category : Security 04-05-2020 by Iveta Karailievova
How to see the websites visited during the incognito mode and delete them
Category : Security 21-02-2020 by Silvia Mazzetta
80 Linux Network Monitor Software & Tools for Managing & Monitoring Unix/Linux Systems
Category : Security 23-10-2018 by Janeth Kent
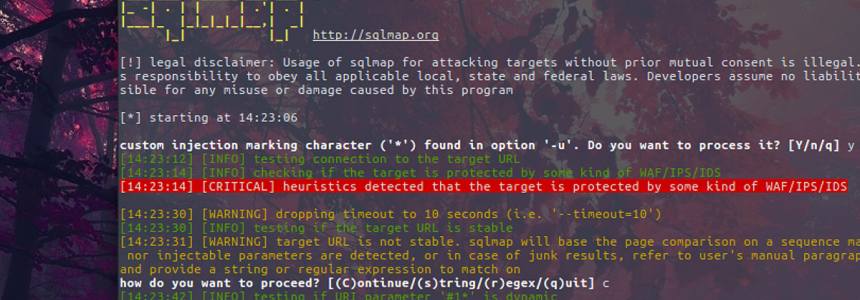
SQLMAP installation and usage in Ubuntu and Kali linux
Category : Security 13-08-2016 by Janeth Kent
Mobile Malware Targets Android Phones: new Kaspersky Lab report
Category : Security 23-05-2013 by Janeth Kent
Super Stealthy Backdoor Spreads To Hit Hundreds Of Thousands Of Web Users
Category : Security 09-05-2013 by Janeth Kent
8 Things That Anonymous, The Hacker 'Terrorist' Group, Has Done For Good
Category : Security 29-04-2013 by Janeth Kent