10 risultati per: hacking
Come sbloccare le funzioni nascoste del telefono con codici segreti
Category : Sicurezza 08-04-2020 by Silvia Mazzetta
Come prevenire l'hacking di file in Whatsapp e Telegram
Category : Sicurezza 23-07-2019 by Janeth Kent
Le pagine su Facebook con foto di bimbi malati sono una truffa
Category : Notizie 24-02-2017 by Janeth Kent
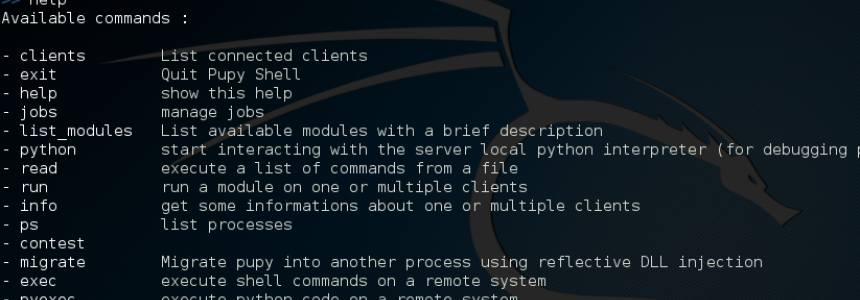
Pupy: Un tool di Amministrazione Remota (RAT) Multipiattaforma
Category : Sicurezza 19-02-2017 by Janeth Kent
The Black Book of Internet, un libro per iniziare con l'hacking etico
Category : Sicurezza 14-04-2020 by Janeth Kent