127 results for: operation
Transitioning from a Home Office to a Virtual Office
Category : Web marketing 08-03-2024 by Janeth Kent
Marketing Trends in Technology 2023: Spotlight on Inflation
Category : Web marketing 01-06-2023 by Janeth Kent
Is AI sexist? A gender perspective in Robotics and Artificial Intelligence
Category : News and events 22-05-2023 by Silvia Mazzetta
The AI Revolution: How Are Small Businesses Beginning To Implement AI?
Category : Technology 26-07-2025 by Janeth Kent
Strings in JavaScript: What they are and how to use them
Category : Javascript 22-06-2021 by Janeth Kent
Why E-Commerce Businesses Should be Using Cloud Computing
Category : Web marketing 01-06-2021 by Silvia Mazzetta
Advanced Android tutorial: discover all your phone's secrets
Category : Mobile 06-05-2021 by Janeth Kent
How to improve customer experience through speech recognition
Category : Technology 27-04-2021 by Janeth Kent
Elon Musk To Found Starbase, A City In Texas To House His Companies And Projects
Category : Technology 05-03-2021 by Janeth Kent
Interesting and Helpful Google Search Features You’ll Want to Start Using
Category : Software 31-01-2021 by Iveta Karailievova
A FULFILLED PROMISE - Using the FETCH API to make AJAX calls
Category : Javascript 26-12-2020 by Iveta Karailievova
The best tricks and features to master your Android Smart TV
Category : Networking 05-11-2020 by Luigi Nori
What's the Difference between Google TV and Android TV?
Category : Software 27-10-2020 by Silvia Mazzetta
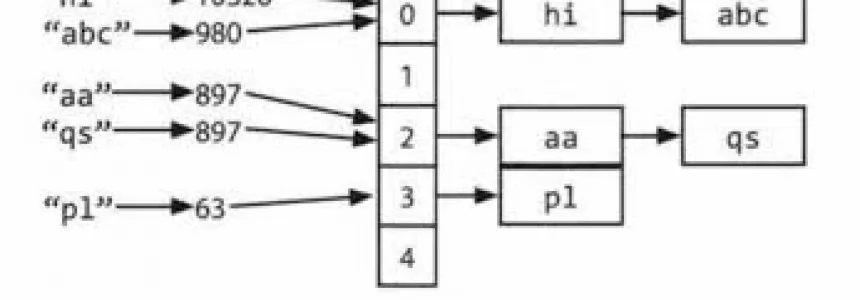
Hashmap: hashing, collisions and first functions
Category : C language 28-06-2020 by Alessio Mungelli
Javascript: what are callbacks and how to use them.
Category : Javascript 23-10-2020 by Silvia Mazzetta
How are businesses using artificial intelligence?
Category : News and events 21-06-2023 by Silvia Mazzetta
How to setup an Android TV with androidtv.com/setup or the Google application
Category : Operating systems 26-10-2020 by Janeth Kent
What cybersecurity professionals have learned from the lockdown experience
Category : Security 26-08-2020 by Silvia Mazzetta
How to Take Your Small Ecommerce Business to the Next Level
Category : Web marketing 25-01-2022 by Janeth Kent
What is Google My Business and how does it help my local business?
Category : Web marketing 02-05-2020 by Luigi Nori
The best websites of the Tor Deep Web and Dark Web Network
Category : Security 03-11-2022 by Janeth Kent
Coronavirus: Citizen Science projects to help research from home
Category : News and events 02-04-2020 by Silvia Mazzetta
How to find everything you need on the Deep Web and the Dark Web
Category : Security 10-05-2021 by Silvia Mazzetta
Best ways to start a video conference without registration
Category : Multimedia 21-04-2020 by Silvia Mazzetta
DevOps, Agile Operations, and Continuous Delivery
Category : Programming 26-09-2019 by Silvia Mazzetta
How to conditionally build an object in JavaScript with ES6
Category : Javascript 09-08-2019 by Janeth Kent
RCS: Everything you need to know about the successor to the SMS
Category : Mobile 18-06-2019 by Janeth Kent
7 Useful tricks for writing more concise and performant JavaScript
Category : Javascript 04-06-2019 by Janeth Kent
Unlock Hidden SmartPhone Features with these Secret Codes
Category : Security 26-07-2025 by Janeth Kent
How to Successfully Promote Your Healthcare Business
Category : Web marketing 20-03-2019 by Janeth Kent
6 JavaScript Utility Libraries you Should Know in 2019
Category : Javascript 18-01-2019 by Janeth Kent
A Guide to Moving IT Services During an Office Relocation
Category : News and events 21-08-2018 by Janeth Kent
5 best open source version control systems tools for sysadmins
Category : Software 13-05-2017 by Janeth Kent
Facebook Prepack, The Next Big Thing In The JavaScript World
Category : Javascript 11-05-2017 by Janeth Kent
How to Connect to a Remote Server via SSH from a Linux Shell
Category : Servers 16-02-2017 by Janeth Kent
Ubuntu servers security: 25 security tools to armor your system
Category : Servers 14-09-2016 by Janeth Kent
PHP7: Guide and References to all the changes between version 5.x and 7 of PHP
Category : Php 27-12-2015 by Janeth Kent