134 results for: Database
How to Track Flight Status in real-time using the Flight Tracker API
The Flight Tracker API provides developers with the ability to access real-time flight status, which is extremely useful for integrating historical tracking or live queries of air traffic into your website. With this API, you can easily track the status of a flight and access airport schedules. There are several Flight Tracker…
Category : Php 12-06-2023 by Janeth Kent
Infinite scrolling with native JavaScript using the Fetch API
I have long wanted to talk about how infinite scroll functionality can be implemented in a list of items that might be on any Web page. Infinite scroll is a technique that allows the user to interact with the mouse by scrolling down to load new dynamic content. In this way, the…
Category : Javascript 15-05-2023 by Janeth Kent
Sorting elements with SortableJS and storing them in localStorage
SortableJS is a JavaScript extension that you will be able to use in your developments to offer your users the possibility to drag and drop elements in order to change their position. To learn what SortableJS is and how to get started, you can read the following tutorial. In this article you…
Category : Javascript 15-05-2023 by Janeth Kent
How to fix excessive MySQL CPU usage
What happens if we realise that a series of databases that we thought were optimised through the use of indexes, have begun to consume CPU usage time of a server to unsuspected limits? Even users have stopped being able to access the server when it had a certain number of visits…
Category : Development 21-12-2022 by Janeth Kent
The first videogame tournaments: the origin of eSports
The first video videogame tournaments: the origin of "eSports". Electronic sports or "eSports" are video game competitions that have been increasing in popularity over the years, being a lucrative sector that currently moves hundreds of millions of euros. Its origins date back to the first video game tournaments in history, which were…
Category : Videogames 19-10-2022 by Janeth Kent
PHP - The Singleton Pattern
The Singleton Pattern is one of the GoF (Gang of Four) Patterns. This particular pattern provides a method for limiting the number of instances of an object to just one. It's an easy pattern to grasp once you get past the strange syntax used. Consider the following class: PHP Code: class Database { public…
Category : Php 04-02-2022 by Janeth Kent
How to connect to MySQL with Node.js
Let's see how you can connect to a MySQL database using Node.js, the popular JavaScript runtime environment. Before we start, it is important to note that you must have Node.js installed on your system. Likewise, you must create a MySQL database. Create a MySQL database If you haven't already done so, you can…
Category : Javascript 04-11-2021 by Silvia Mazzetta
How to set up your own free web server with XAMPP
Nowadays anyone can create their own website easily and free of charge. Whether through a CMS (such as WordPress) or by hand with HTML, CSS and JavaScript, in a few minutes we can have a more or less functional website up and running. However, in order to test that everything…
Category : Servers 25-10-2021 by Silvia Mazzetta
What is a Full Stack Developer?
The demand for the Full Stack Developer is growing exponentially in recent years. Disruptive technology companies and startups are increasingly requesting this type of multipurpose profile that knows multiple programming languages and can assume all kinds of functions within the company. Throughout this article we will tell you what a full stack…
Category : News and events 06-08-2021 by Janeth Kent
Why E-Commerce Businesses Should be Using Cloud Computing
Cloud computing is the on-demand delivery of computer system resources via the internet. The resources offered in a cloud computing solution include data storage applications, servers, databases, software, and networking tools. Cloud computing seems like it’s been created specifically for businesses like e-commerce stores, as it offers increased flexibility and…
Category : Web marketing 01-06-2021 by Silvia Mazzetta
The ultimate cybersecurity checklist for programmers
In today's digital age, cybersecurity has become an essential concern for programmers. With cyber threats on the rise, it is crucial for programmers to adopt robust security practices to protect their code, data, and systems from malicious attacks. To assist programmers in this endeavor, we have compiled the ultimate cybersecurity…
Category : Security 02-06-2023 by Silvia Mazzetta
Top JavaScript libraries and frameworks part 1
JavaScript libraries and frameworks make it easy to develop websites and applications with a wide variety of features and functionality, all with dynamic, flexible and engaging features. According to a 2020 StackOverflow survey, JavaScript remains the most widely used programming language (for the eighth year), with 67.7% of respondents using it. Its…
Category : Javascript 06-05-2021 by Janeth Kent
Network attacks and how to avoid them
Nowadays it is impossible to list all the different types of attacks that can be carried out on a network, as in the world of security this varies continuously. We bring you the most common ones according to the network attack databases, so that we can keep up to date…
Category : Security 03-05-2021 by Silvia Mazzetta
How to make a multilingual website without redirect
Today, we're going to talk about how to implement a simple language selector on the basic static website, without the need of any backend or database calls or redirection to another page. We will be using only JavaScript, no PHP or other programming languages. Serving HTML content in multiple languages is…
Category : Javascript 31-05-2023 by
Graphic design and its impact on Web Development
In today's article we will explain the concept of graphic design, its fundamentals and what it brings into web development. Graphic design is applied to everything visual, believe or not, it can aid in selling a product or idea, it's applied company identity as logos, colors, typography of the company…
Category : Web design 05-04-2021 by
7 Astonishing New Uses of Machine Learning
Recently a strange video published on YouTube caused a controversy – it was a funny take on Queen Elizabeth’s traditional Christmas message created by Channel 4, a British public-service television broadcaster. They used AI to produce a fake video of the Queen making it look very realistic and if the message itself…
Category : Technology 31-12-2020 by Iveta Karailievova
What is Django and what is it used for
When we talk about Django, we refer to that framework that is used for any totally free and open source web application which is written in Python. Basically, it's a group of elements that will help you create web pages much more easily and quickly. At the moment you are going…
Category : Programming 26-12-2020 by Janeth Kent
Django vs. Laravel: Market Share Comparison
There are two leading frameworks in the web development segment: Django and Laravel. In this article, we prepared a Django and Laravel comparison focusing on their market share so that you can figure out which framework is better for your project. Selecting the appropriate framework is crucial for coping with…
Category : Programming 23-12-2020 by Janeth Kent
Brief History of Biometric Authentication
These days, biometric authentication seems to be part of every little gadget or device we use. You’ve no doubt used it when logging onto your laptop, your tablet, or your cell phone, alongside more ‘old school’ methods like a password or PIN. Governments often use biometric authentication for security access and…
Category : Security 30-11-2020 by Janeth Kent
A beginner’s guide to software vulnerabilities
What are software vulnerabilities The number of devices connected to the Internet is growing every day. And among those devices we find not only computers and smartphones, but also an ever-rising number of cameras, smoke detectors, motion sensors, smart door locks, and let’s not forget that even plant pots. Many households…
Category : Security 17-11-2020 by Iveta Karailievova
Why You Should Hire Node.js Developer for Your Backend Development
When developers are building a new website, they mainly focus on both frontend and backend development. The frontend code helps create the interfaces through which the app interacts with the users while the back-end code interacts with the server to deliver data or content that is displayed to the website…
Category : Javascript 27-10-2020 by Luigi Nori
3 awesome ways technology is helping us combat the COVID pandemic
Times are hard now, that humanity once more stumbled into a terrible pandemic. But in comparison to the poor folks back in 1918 when the Spanish flu was on wreaking havoc, nowadays we have the advantage of cutting edge technology on our side. Here’s a quick list of top three ways…
Category : Technology 28-10-2020 by Iveta Karailievova
MAME Multiple Arcade Machine Emulator: How to download and configure this arcade emulator for Windows
Despite the fact that new state-of-the-art computer games are coming out every so often, the whole retro theme is very appealing to users who are looking to relive the long hours spent in front of a console, such as the NES or SNES, and even in arcades playing arcade machines.…
Category : Software 14-10-2020 by Luigi Nori
Google Dorks: How to find interesting data and search like hacker
Go the words Google and Hacking together? Well if you thought that we will learn how to use hack Google, you might be wrong. But we can Use Google search engine to find interesting data accidentally exposed to the Internet. Such a simple search bar has the potential to help you also…
Category : Security 03-12-2021 by
How to securely access the Dark Web in 15 steps. Second part
Let's continue with the 2nd part of our article in which we try to give you some advice on how to safely and securely explore the dark web. Let's restart from number 6. 6. Changes the security level in the Tor browser It is also possible to increase the security level of the…
Category : Security 08-03-2024 by Janeth Kent
The concept of Model-View-Controller (MVC) explained
In software engineering, we use design patterns as reusable solutions to a commonly occurring problem, a pattern is like a template for how to solve a problem. Model-View-Controller (MVC) is a software design pattern that divides the related program or web application into three interconnected elements or components. Each of these…
Category : Programming 22-10-2020 by
The package managers npm and yarn: main differences
Npm and yarn are package managers that help to manage a project’s dependencies. A dependency is, as it sounds, something that a project depends on, a piece of code that is required to make the project work properly. In the past we had only npm but it had so many issues…
Category : Javascript 19-08-2020 by Luigi Nori
A collection of interesting networks and technology aiming at re-decentralizing the Internet
The decentralised web, or DWeb, could be a chance to take control of our data back from the big tech firms. So how does it work? Take a look at this collection of projects aimed to build a decentralized internet. Cloud BitDust - is decentralized, secure and anonymous on-line storage, where only…
Category : Networking 27-08-2020 by Janeth Kent
MySQL 8.0 is now fully supported in PHP 7.4
MySQL and PHP is a love story that started long time ago. However the love story with MySQL 8.0 was a bit slower to start… but don’t worry it rules now ! The support of MySQL 8.0’s new default authentication method in PHP took some time and was added in PHP…
Category : Databases 27-10-2020 by Janeth Kent
Is JavaScript good for machine learning?
One of the things you always hear when you are talking to someone related to the M.L. world is that, one must learn Python because the vast majority of the major libraries are in that technology. You're probably right, but I chose JavaScript as the metal of my sword and…
Category : Javascript 16-06-2020 by Silvia Mazzetta
Web shells as a security thread for web applications
Over the past two decades, web applications as an alternative to traditional desktop application have been on to rise. As their name suggests, they are installed on web servers and accessed via a web browser. This gives web apps a rather long list of advantages: multi-platform cross-compatibility, no installation required for…
Category : Security 04-05-2020 by Iveta Karailievova
JavaScript Development Services and How It Works
JavaScript is a programming language. This scripting language, however, is used to create features on web pages. As a result, it helps to make web pages alive. All that stuff that you see or do on the internet or websites or web applications is because of JavaScript. It is used to…
Category : Javascript 17-04-2020 by Luigi Nori
The best websites of the Tor Deep Web and Dark Web Network
We already talked about Deep Web more than a year ago, explaining that to open Deep Web (or rather Dark Web) sites you need total and undetectable user anonymity and access to the "onion" network. The Dark Web is much smaller than the Deep Web and is composed mainly of sites…
Category : Security 03-11-2022 by Janeth Kent
Coronavirus: Citizen Science projects to help research from home
The term "citizen science" is used to define the involvement and active and conscious participation of people of different ages, education and social backgrounds in scientific research activities: students, simple enthusiasts, retired people and amateur scientists, not included in academic structures. In other words, everyone is invited to contribute. No specific…
Category : News and events 02-04-2020 by Silvia Mazzetta
How to find everything you need on the Deep Web and the Dark Web
How to find everything you need on the Deep Web and the Dark Web Best links, sites, markets what you can find on the Deep Web The Deep Web is also known as the Deep Internet is a sort of layer of content that is not indexed by the search engines…
Category : Security 10-05-2021 by Silvia Mazzetta
10 Steps To become Work with a Low-Code Platform
Low code has become a popular option for businesses that need to develop their software’s in a simple way and at an accelerated pace to get their needed software up and running as soon as possible. Using the low-code platform allows businesses to focus more on innovation and enables them to…
Category : Software 25-03-2020 by Luigi Nori
Cross-Origin Resource Sharing (CORS) and examples of XSS and CSRF
Cross-Origin Resource Sharing (CORS) enables web clients to make HTTP requests to servers hosted on different origins. CORS is a unique web technology in that it has both a server-side and a client-side component. The server-side component configures which types of cross-origin requests are allowed, while the client-side component controls…
Category : Javascript 30-01-2020 by Luigi Nori
Java Sorting Algorithm: Bubble Sort
Programming, the need to order the collections of data or objects that must then be manipulated often arises. Ordering a list can be useful in cases where you have to do very quick searches. We will see later on how to maintain an ordered list is useful to carry out dichotomous…
Category : Java 15-12-2019 by Alessio Mungelli
The best Internet search engines used by hackers
Today, many users wonder what tools hackers use to look for different vulnerabilities on devices that are connected to the Internet. Normally, everyone uses specific tools, but there are search engines that are specifically designed for security researchers. Although many users think that a hacker is a hacker, the reality is…
Category : Security 07-01-2021 by Silvia Mazzetta
10 Open source tools for security operations (SOC)
As we know, there are many moving parts to building a Security Operations Centre (SOC). From a technological point of view, it is very important to count on open source to identify threats and reduce costs. From a DiD (Defense in Depth) point of view, there are many devices and…
Category : Security 29-11-2019 by Janeth Kent
10 Javascript tips and tricks you should know
Javascript is the most widely used language in fullstack development thanks to the boom in recent years in libraries and frameworks such as NodeJs (backend) and React/Angular/Vue (frontend). However, regardless of which one you use to develop, there are a number of tricks and tips common to all of them…
Category : Javascript 08-08-2019 by Janeth Kent
The strategic advantages of Open Source
Being a good web designer also means getting the right tools (and skills) to accomplish the task. Fortunately, there are an incredible number of resources available to those of us who work in this area. Here's the thing: most of them are free. A smart and cheap start There are some costs involved…
Category : Programming 11-07-2019 by Janeth Kent
10 Collaborative Coding Tools for Remote Pair Programming
The days of lonesome coding are long gone since the development of pair programming. It is a technique where two software developers share a keyboard and collaboratively work together. The two developers take turns and continually switch roles in writing code: one being the Driver, whose job is to write…
Category : Development 02-03-2020 by Janeth Kent
The Bible of the Best Node.Js Frameworks
Node.js is the platform built on chrome’s javascript runtime for easily building fast, scalable network applications. It uses an event-driven non-blocking IO modal that makes it lightweight and efficient. node.js is perfect for data-intensive real-time applications that run across distributed devices. Node.js frameworks can help to streamline the development of web…
Category : Javascript 09-05-2019 by Janeth Kent
Top free JavaScript User Authentication Libraries
We are keen on security: authentication is an important issue when creating a dynamic web application Authentication is for identifying users and provide different access rights and content depending on their id. Since new tutorials appear on the web and more people try to understand the cost-benefit equation for implementing their…
Category : Javascript 29-01-2020 by Janeth Kent
Which Javascript frameworks will rule in 2019?
In this article, we will review and analyze the 2018 State of JavaScript report to later focus attention on frameworks that will be at the center of attention in 2019. Let's take some time to look at the amazing journey of JavaScript, reflected in the use of more than 20,000 developers…
Category : Javascript 19-02-2019 by Janeth Kent
A roadmap to becoming a web developer in 2019
There are plenty of tutorials online, which won't cost you a cent. If you are sufficiently self-driven and interested, you have no difficulty training yourself. The point to learn coding I think is to read a lot of code of other developers, then typing code and testing to see what…
Category : Programming 30-05-2019 by Janeth Kent
Best Javascript front-end hacking cheatsheets
JavaScript has a extremely high potential to build cutting-edge web applications. But it's really hard to memorize it by heart. The JavaScript cheat sheets therefore act perfectly as a reminder and a comprehensive reference for developers. All popular and special purpose cheat sheets have been discussed above. You now have…
Category : Javascript 06-05-2020 by Janeth Kent
Working with JSON in JavaScript
JSON is short for JavaScript Object Notation and an easy - to - access way to store information. In short, it gives us a collection of human - readable data that we can access in a very logical way. In addition to RSS feeds, any sites now share data using JSON,…
Category : Javascript 08-04-2020 by Janeth Kent
Best Node Js Resources, Courses and Tutorials.
NodeJS is a platform that enables developers to write high-performance and networked applications server side. And using good old Javascript as well. Why should you study NodeJS? To begin with, it never hurts to learn something new. But most importantly, it's great to learn NodeJS. With a focus on modern JavaScript and real-world application,…
Category : Javascript 10-05-2020 by Janeth Kent
Most Popular Node.js Frameworks in 2019
Before Node.js, web developers always faced the issue of having to use different languages for client-side and server-side scripts. JavaScript was traditionally the language for client-side scripting with the HTML code running in the browser. The invention of Node.js in 2009 introduced server-side scripting with JavaScript code running on the…
Category : Javascript 14-02-2019 by Janeth Kent
80 Linux Network Monitor Software & Tools for Managing & Monitoring Unix/Linux Systems
It’s hard work monitoring and debugging Linux performance problems, but it’s easier with the right tools at the right time. Finding a Linux Network Monitor tool or Software package for your Critical servers and services that are running on those systems in one of the most (if not the most)…
Category : Security 23-10-2018 by Janeth Kent
8 Free PHP Books to Read in Summer 2018
In this article, we've listed 8 free PHP books that can help you to learn new approaches to solving problems and keep your skill up to date. Practical PHP Testing This book is aimed at advanced php developers and is comprised of articles from the author's Practical PHP Testing blog series. It…
Category : Php 20-06-2018 by Janeth Kent
Best Websites to Learn Coding Online
You know and we know that it’s totally possible to learn to code for free... If you can teach yourself how to write code, you gain a competitive edge over your peers, you can think more algorithmically and thus can tackle problems more efficiently. But what are the best resources to achieve…
Category : Programming 19-06-2018 by Janeth Kent
Send Push Notification to Users Using Firebase Messaging Service in PHP
Today I will show you how to send unlimited free push notifications to your clients using Firebase Cloud Messaging (FCM) in your PHP web application. Push Notifications are clickable messages that come from a website. They are used to show notifications outside the web page context even if the user is not browsing…
Category : Php 14-05-2018 by Janeth Kent
How to Become a Full Stack Developer in 2018
A full stack developer is someone who can work on the development of all layers of an app or program. That means that they are familiar with both the front end and back end aspects of programming. For example, full stack development would involve the development of the user interface, the…
Category : Programming 22-03-2018 by Janeth Kent
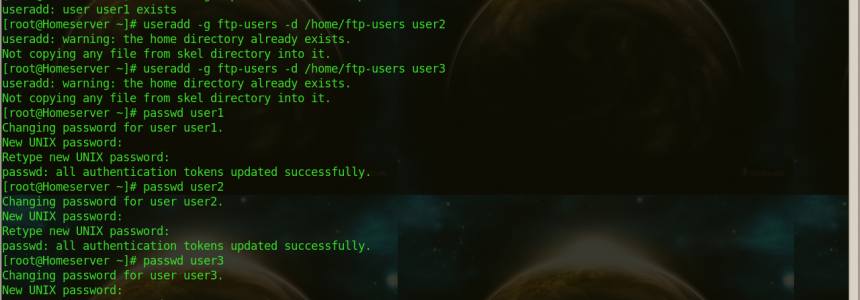
MYSQL: How to create a new user and give it full access only to 1 database
To create a new user in MySQL and give it full access only to 1 database, say dbTest, these are the MySQL commands to do that To create the user: CREATE USER 'user'@'hostname'; To give it access to the database dbTest: GRANT ALL PRIVILEGES ON dbTest.* To 'user'@'hostname' IDENTIFIED BY 'password'; If you are running…
Category : Databases 07-02-2018 by Janeth Kent
ArangoDB, install and configure the popular Database in ubuntu 16.04
Introduction to ArangoDb, open source, NoSQL, multi-model database BigData seems to be getting stronger every day and more and more NoSQL databases are coming out to the market, all trying to position themselves in the lead to be the reference. This week I tried ArangoDB! Another NoSQL database? Today I'm going to…
Category : Databases 14-11-2017 by Janeth Kent
How JSON data types work in mysql
First introduced in MySQL 5.7.8, the JSON data type is a specialized binary column type, similar to a blob , but with added machinery to optimize the storage and retrieval of values from a column typed as json . Javascript Object Notation or more commonly known as JSON, is a modern…
Category : Databases 30-09-2019 by
PHP: Basic Introduction to Namespaces
History of PHP Namespaces In PHP prior to 5.3 (2009), any class you define lived at the same global level as other classes. Class User, class Contact, class Db they're all together in the global namespace. This may seem simple, but it makes organization tough, which is why PHP developers started using underscores…
Category : Php 19-05-2017 by Janeth Kent
How to Configure the Mod_Security Core Ruleset in Ubuntu
ModSecurity is a Web Application Firewall, a program that can be used to inspect information as it passes through your web server, intercepting malicious requests before they are processed by your web application. This tutorial will show you how to install ModSecurity on Apache, and configure it with some sensible rules provided…
Category : Servers 04-03-2017 by Janeth Kent
Install Apache, MariaDB and PHP7 on Ubuntu 16.04
Ubuntu 16.04 LTS Xenial Xerus comes with PHP7 by default so you don’t have to rely on third-party PPA to get PHP7 installed. In this tutorial, we are going to look at how to install Apache, MariaDB and PHP7 (LAMP stack) on Ubuntu 16.04 LTS Xenial Xerus. Update: This tutorial is…
Category : Servers 18-11-2016 by Janeth Kent
How to send an e-mail in 1984 - Vintage overdose
How to send an e mail 1980's style. Electronic message writing down the phone line. First shown on Thames TV's computer programme 'Database' in 1984 07/06/1984 Database is an old British TV show, broadcasted in 1984, which explains how the networks work before the modern Internet, but also the futuristic concept…
Category : Technology 01-10-2016 by Janeth Kent
Ubuntu servers security: 25 security tools to armor your system
The Ubuntu repositories contain several useful tools for maintaining a secure network and network administration.This security tools include network scanning,attack detection,Virus Detection etc. 1) Wireshark -- network traffic analyzer Wireshark is a network traffic analyzer, or "sniffer", for Unix and Unix-like operating systems. It is used for network troubleshooting, analysis, software and…
Category : Servers 14-09-2016 by Janeth Kent
MySql: How to build a performant search engine
In content-heavy websites, it becomes increasingly important to provide capable search possibilities to help your users find exactly what they’re looking for. The most obvious solution is searching your MySQL database directly, but implementing a generic MySQL search is not at all trivial. Here’s how to avoid those pitfalls and…
Category : Databases 10-09-2016 by Janeth Kent
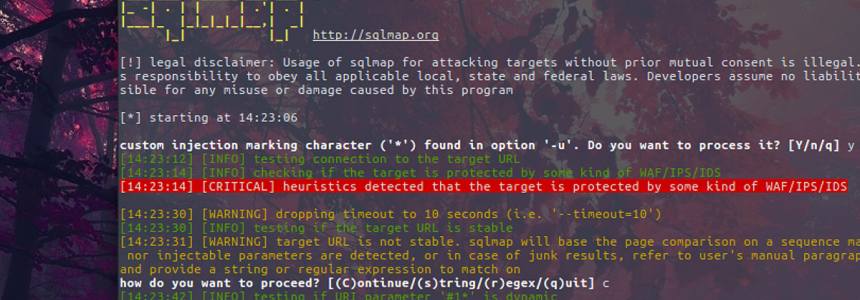
SQLMAP installation and usage in Ubuntu and Kali linux
Let's talk about the penetration testing using one of the KALI linux tool called SQLMAP. What is SQLMAP? sqlmap is an open source penetration testing tool that automates the process of detecting and exploiting SQL injection flaws and taking over of database servers. It is a open source tool to use sql injection…
Category : Security 13-08-2016 by Janeth Kent
PHP Libraries For Summer 2016
Here are our picks for the 12 most useful and interesting open-source PHP libraries that you should check out this summer! Monolog With Monolog you can create advanced logging systems by sending your PHP logs to files, sockets, databases, inboxes or other web services. The library has over 50 handlers for various…
Category : Php 11-08-2016 by Janeth Kent
Install HHVM + Nginx on Ubuntu 14.04
The LEMHH software stack is a group of software that can be used to serve dynamic web pages and web applications. This is an acronym that describes a Linux operating system, with an Nginx web server. The backend data is stored in MySQL and the dynamic processing is handled by…
Category : Networking 12-05-2017 by Janeth Kent
Optimize MySql On Low Memory Servers
Cloud computing makes it very affordable to get your own private virtual server on the Internet. Digital Ocean offers an entry level droplet for USD$5 per month, and Amazon.com has a micro instance tier on the EC2 platform that is free for the first year. These instances are rather useful…
Category : Databases 25-08-2020 by Luigi Nori
PHP Filters: the best way to sanitize and validate datas
What are PHP filters? One of the most amazing strengths of PHP is its convenience. Shockingly this same profit has worked against PHP as numerous new coders have forgotten any security to establish safety or fails to offer the adroitness to make a class to validate their variables from end users. One…
Category : Php 02-03-2020 by Janeth Kent
Speed up your site and protect it against DDOS attacks with CloudFlare
If you have checked your site or blog, then you may noticed the page speed, YSlow, Timeline etc. An important factor to give fast content delivery to your blog’s reader and page speed, CND (Content Delivery Network) is must. The CDN makes your wordpress blog even faster to load, that…
Category : Networking 23-07-2014 by Luigi Nori
PHP: list of best awesome PHP libraries
It is an exciting time to be a PHP developer. There are lots of useful libraries released every day, and with the help of Composer and Github, they are easy to discover and use. Here is a complete list of the coolest that We’ve come across. Package Management Libraries for package and…
Category : Php 27-04-2014 by Janeth Kent
10 Server and network monitoring tools
When you have a website or a network, it’s helpful to be aware of any issues as soon as they occur. There are open source and freeware server/network monitoring tools that will supervise your infrastructure for any issues that may arise. These tools are meant to aid you in avoiding…
Category : Networking 04-02-2014 by Janeth Kent
20 Awesome Free Tools For Web Developers 2014
If you’re a web designer or a front-end developer, you probably spend a lot of time writing mark-up. Fortunatly, there are some great tools and projects on the web that can improve your next project easily and quickly. Today we have tracked down 20 brilliant free online tools for developers. We’ve…
Category : Web design 16-01-2014 by Janeth Kent
Free PHP, HTML, CSS, JavaScript editor (IDE) - Codelobster PHP Edition
For valuable work on creation of sites you need a good comfortable editor necessarily. There are many requiring paid products for this purpose, but we would like to select free of charge very functional and at the same time of simple in the use editor - Codelobster PHP Edition .…
Category : Software 16-01-2014 by Janeth Kent
Install Bit Torrent Sync on Ubuntu
There are some great tools for syncing files over the internet available to us, but one stands out from the rest in regards of technology used and possible use cases. A public beta version was released in June this year and now it’s available for Windows, Mac, Linux, FreeBSD, Android and…
Category : Networking 15-01-2014 by Janeth Kent
86 Must Have WordPress Plugins Of 2013
Today we are going to share Best 85 WordPress Plugins for 2013 which will help WordPress Webmasters all over the world. 1. ALL AROUND WORDPRESS CONTENT SLIDER CAROUSEL All Around wordpress content slider is a multi-purpose all-in-one slider solution for your website. It supports both images and video. It can be an…
Category : Software 09-12-2013 by Janeth Kent
PHP: Storing arrays in database
When working with databases, sometimes it is necessary to store an array in a MySQL field. Unfortunately, there is no way to directly pass in an array as a parameter. Storing these data structures is a bit more complex, but by no means hard or impossible. To convert any array (or…
Category : Databases 18-11-2013 by Janeth Kent
Tutorial: Introduction to PHP:PDO
Many PHP programmers learned how to access databases by using either the MySQL or MySQLi extensions. As of PHP 5.1, there’s a better way. PHP Data Objects (PDO) provide methods for prepared statements and working with objects that will make you far more productive! PDO Introduction “PDO – PHP Data Objects…
Category : Databases 15-10-2013 by Janeth Kent
Ubuntu: How To Start Program As Service
According to Ubuntu’s Upstart website, “Upstart is an event-based replacement for the /sbin/init daemon which handles starting of tasks and services during boot, stopping them during shutdown and supervising them while the system is running.”Basically, Upstart is an init daemon that replaces the /etc/init.d scripts.It comes with Ubuntu 6.10 and…
Category : Networking 10-10-2013 by Janeth Kent
Hash Passwords With PHP 5.5
Every PHP developer would have to build an application that relies on a user login. It means that the user of the website having a Username and Password which is stored in the database so they can login into your website. Therefore it's important that passwords stored in the database should be hashed…
Category : Php 28-08-2013 by Janeth Kent
How to import and export a large database using SSH
The following code snippets will allow you to import and export a database Command Line. To get SSH access to your hosts server you will need to contact your web hosting company, our suggestion is that you find a reliable, high-performing, secure hosting company that can help you. In case you are on a…
Category : Databases 25-06-2019 by Janeth Kent
10 Javascript Tutorials You Must See
Fortunately, we live in an era of global connectivity and access to many resources. Thanks to the Internet and people who enjoy sharing content, you can find almost everything you need to learn, and for free. Free tutorials, books and courses are easily found without spending too much. So if you…
Category : Javascript 10-09-2020 by Silvia Mazzetta
10 Best PHP Scripts for Polling System
In this post we will show you a collection of 10 best PHP Poll Scripts. These PHP scripts for polling system can be added in any self-hosted website. Check out these awesome and easy to install scripts. 1. JAXpoll JAXpoll is a polling widget that you can add into any of your websites.…
Category : Php 23-08-2013 by Janeth Kent
Weekly Fresh Resources for Designers and Developers: JavaScript, HTML & CSS – Week of August 12, 2013
This is our weekly design news column where we share our favorite design related articles, resources and cool freebies from the past week. Enjoy :) Tutorials Raymond Camden shares a very cool proof of concept for drawing a shape on a map and getting back map data from Google Maps. Using Drawing Tools…
Category : Web design 21-08-2013 by Janeth Kent
Top 12 free JavaScript resources for advanced users
If you have a strong knowledge in programming and want to improve your JavaScript skills or you want a good reference book then this list is for you. We've put together a list of 12 of our favorite JavaScript free book to help save you time and energy along the way.…
Category : Javascript 26-06-2023 by Janeth Kent
Submit Your Site to The Best CSS Galleries
Have you spent your time creating a great website design and now you need some traffic, links, and exposure? Getting your site listed on CSS Galleries can do just that for you! Submit your site to the best CSS Galleries and watch the traffic flow in if you get approved. But, how can…
Category : Css 05-08-2013 by Janeth Kent
13 jQuery Plugins and Tutorials for e-commerce website
E-Commerce websites are making shopping easy for customers. The number of ecommerce websites are growing with every day. Shopping Cart is the most important aspect of an E-Commerce website. We all know that jQuery plugins helps us to add difficult things to our websites very easily. Below you’ll find 13 jQuery shopping cart plugin and…
Category : Javascript 02-08-2013 by Janeth Kent
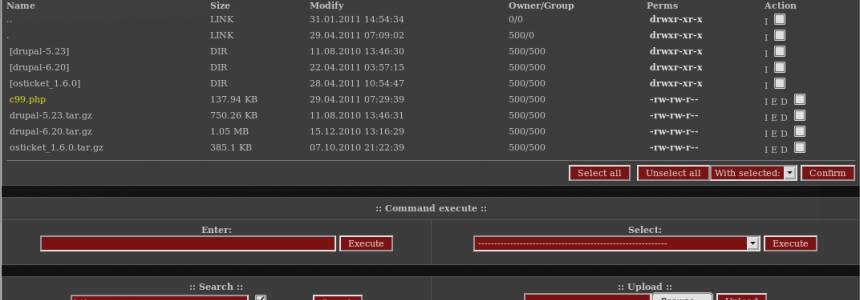
How to detect r57 and c99 Shells in your server
When malicious intruders compromise a web server, there's an excellent chance a famous Russian PHP script, r57shell, will follow. The r57 and C99 shell PHP script gives the intruder a number of capabilities, including, but not limited to: downloading files, uploading files, creating backdoors, setting up a spam relay, forging…
Category : Security 26-07-2013 by Janeth Kent
The best code editor for web developers
Every web developer requires the right tools to do their job, therefore the choice of a source code editor shouldn’t come lightly. This is where we spend most of our development time and where productivity is gained or lost on a grand scale. But which is the best Code Editor? To determine the best source code editor, we…
Category : Software 25-07-2013 by Janeth Kent
21 PHP Libraries You Should Know About
The aim of the Standard PHP Library-or SPL is to provide a standard library of interfaces which allows developers to take full advantage of object-oriented programming in PHP. Therefore in this article we have collected 21 of the best PHP Libraries which will assist and help developers to simplify their work and serve…
Category : Programming 24-07-2013 by Janeth Kent
The definitive list of analytics and metrics tools
Lately I had a little problem with Google Analytics. Live results wasn't counting perfectly the number of live users online. Obviously, I am a little disappointed about it, and basically, the amount of time to research a solution or alternative would make the original content stale. Now, i want to…
Category : Software 22-07-2013 by Janeth Kent
A Collection of Essential WordPress Plugins
With so many plugins available, finding the best WordPress plugins can be hard and time-consuming! That is my motivation for gathering this comprehensive collection of Essential WordPress plugins. Enjoy! WP DB Backup WP DB Backup is an easy to use plugin which lets you backup your core WordPress database tables just by…
Category : Web design 21-08-2020 by Janeth Kent
Setup and Manage Mysql/MysqlAdmin root password
Managing mysql main root password is one of the most common questions/problems that new linux users have, and one of the essential tasks. By defaultroot user is MySQL admin account. The Linux / UNIXlogin root account for your operating system and MySQL root aredifferent. They are separate and nothing to…
Category : Databases 18-07-2013 by Janeth Kent
Who is immune to cyber-crime?
Every company is a target. No industry is safe, or immune to cyber-crime, and although technology in IT security has come a long way, the number of data hacking is growing. Knowing your potential attacker is essential to being prepared to defend your company from hackers and to protect your data. According to…
Category : Security 15-07-2013 by Janeth Kent
Top 15 Free Hacking Tools for Ethical Hackers
Intrusion tests, known as "Penetration Analysis" or "Ethical Hacking", are now a common practice to know the level of security a website has. These tests assess the type and extent of system and network vulnerabilities in terms of confidentiality and integrity. They check the security of the network and empirically verify…
Category : Security 19-06-2020 by Silvia Mazzetta
50 tools to reinvigorate your content marketing efforts
2012 has been the year of growth for content marketing. Brands have begun to embrace the discipline as a vital part of their overall strategy. What was once a conversation on “why content marketing” has turned into a conversation on “how to.” The current focus on social media advertising is pulling marketing attention…
Category : Web marketing 03-07-2013 by Janeth Kent
PHP 5.5: Introduction To The New Functionalities
PHP 5.5.0 has been released, bringing with it a host of new features and fixes. Here we post a review; Generators are now available Generators provide a simple way to iterate through data without having to write a class implementing the Iterator interface. Just like any other function a generator is defined with…
Category : Programming 02-07-2013 by Janeth Kent
NoSQL Concept and MongoDB
NoSQL has emerged as a different and alternative approach compared to relational database management systems (RDBMS). Actually, there are fundamental differences between the scalable NoSQL systems and relational database management systems. Relational database management systems are transaction-based and have ACID rules. NoSQL systems do not fully support the ACID rules and there is no…
Category : Databases 28-06-2013 by Janeth Kent
71 Social Media Monitoring Tools
If you want to monitorize the "social world web" you need social media monitoring tools. Before you reach for your wallet and start to spend money try out some of the free social media monitoring services. We have collected Free social media monitoring tools. In the first group are the most popular Social Media Monitoring…
Category : Social networks 27-06-2013 by Janeth Kent