37 results for: identity
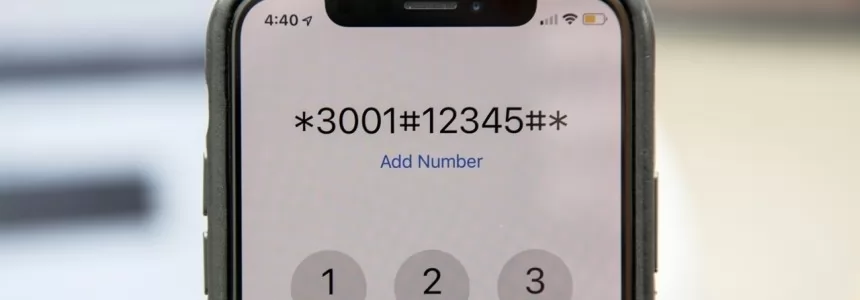
Android Hidden Codes: unveiling custom dialer codes and their functionality
In the world of Android smartphones, there exist numerous hidden codes that can unlock a treasure trove of functionalities and features. These codes, known as custom dialer codes, provide access to various settings, diagnostics, and information that are not readily available through regular menus. In this article, we will explore…
Category : Mobile 02-06-2023 by Janeth Kent
What is a JWT token and how does it work?
JWT tokens are a standard used to create application access tokens, enabling user authentication in web applications. Specifically, it follows the RFC 7519 standard. What is a JWT token A JWT token is a token that gives the user access to an application by certifying their identity. This token is returned to…
Category : Programming 08-03-2024 by Janeth Kent
Secret iPhone codes to unlock hidden features
We love that our devices have hidden features. It's fun to learn something new about the technology we use every day, to discover those little features that aren't advertised by the manufacturer. And unless you spend a lot of time playing around in the Phone app, you probably don't know, until…
Category : Security 22-10-2021 by Silvia Mazzetta
The ultimate cybersecurity checklist for programmers
In today's digital age, cybersecurity has become an essential concern for programmers. With cyber threats on the rise, it is crucial for programmers to adopt robust security practices to protect their code, data, and systems from malicious attacks. To assist programmers in this endeavor, we have compiled the ultimate cybersecurity…
Category : Security 02-06-2023 by Silvia Mazzetta
Network attacks and how to avoid them
Nowadays it is impossible to list all the different types of attacks that can be carried out on a network, as in the world of security this varies continuously. We bring you the most common ones according to the network attack databases, so that we can keep up to date…
Category : Security 03-05-2021 by Silvia Mazzetta
Cybersecurity and Data Privacy: Why It Is So Important
The internet has made it very easy for people all across the world to stay connected with one another. Access to information, services, and people is possible for pretty much anyone with an internet connection today. But while this has brought many positive changes to how people live and connect,…
Category : Security 26-02-2021 by Janeth Kent
Graphic design and its impact on Web Development
In today's article we will explain the concept of graphic design, its fundamentals and what it brings into web development. Graphic design is applied to everything visual, believe or not, it can aid in selling a product or idea, it's applied company identity as logos, colors, typography of the company…
Category : Web design 05-04-2021 by
Deepfakes Detection – An Emerging Technological Challenge
It is highly probable that while browsing the Internet, everyone of us has at some point stumbled upon a deepfake video. Deepfakes usually depict well-known people doing really improbable things – like the queen of England dancing on her table or Ron Swanson from Parks and Recreations starring as every…
Category : Technology 27-01-2021 by Iveta Karailievova
How to Use Bitcoin: mining, wallets, payments
You have certainly heard of Bitcoin, the virtual currency that periodically makes people talk about itself because of its innovative and particular nature. In this case, you have probably also wondered how it is possible to get and subsequently spend Bitcoins, and if it is something useful, as well as…
Category : Technology 10-12-2020 by Silvia Mazzetta
Google everywhere: anatomy of a massive giant
The alarm clock is going off. A hand floats over the bedside table groping for the source of the sound: probably a cell phone and maybe one of the more than 2.5 billion Android devices in the world. Alphabet's operating system (Google's matrix) concentrates 74.6% of the market and together with…
Category : Technology 03-12-2020 by Silvia Mazzetta
How to securely access the Dark Web in 15 steps. First part
The dark web can be a pretty dangerous place if you don't take the right precautions. You can stay relatively safe with a good antivirus and a decent VPN. However, if you want to be completely anonymous and protect your device, you'll need a little more than that. Here there are…
Category : Security 08-03-2024 by Silvia Mazzetta
How to Browse the Internet Anonymously: 6 tips
Most of the actions you take online are not as private as you might imagine. Nowadays, countless people and groups try to follow our online behaviour as closely as possible. Our ISPs, our network administrators, our browsers, search engines, the applications we have installed, social networks, governments, hackers and even the…
Category : Security 16-09-2020 by Silvia Mazzetta
How to recover an Instagram hacked account
You can't access your Instagram account. The cybercriminal who probably hacked your profile changed your password. Now what? What to do now? First try to stay calm: unfortunately these things can happen, but there is a solution to everything, and today we will explain how to solve this specific problem. In this…
Category : Social networks 16-07-2020 by Janeth Kent
A collection of interesting networks and technology aiming at re-decentralizing the Internet
The decentralised web, or DWeb, could be a chance to take control of our data back from the big tech firms. So how does it work? Take a look at this collection of projects aimed to build a decentralized internet. Cloud BitDust - is decentralized, secure and anonymous on-line storage, where only…
Category : Networking 27-08-2020 by Janeth Kent
Dark Web: how to access, risks and contents
You've probably heard of the Dark Web before, but do you really know what the Dark Web is, or what it consists of? Do you know its risks? Which users use the Dark Web? What content is published? Would you know how to access the Dark Web safely? If you are reading…
Category : Security 13-06-2020 by Silvia Mazzetta
What is Cyber Intelligence and how is it used?
What is Cyber-intelligence and what is it used for? This is a question that is usually asked by security, cyber-security and intelligence professionals. Cyber-intelligence is a hybrid concept between these three worlds and professional fields, and therefore it is an opportunity and a necessity to know what it is and what…
Category : Security 11-06-2020 by Silvia Mazzetta
How to find everything you need on the Deep Web and the Dark Web
How to find everything you need on the Deep Web and the Dark Web Best links, sites, markets what you can find on the Deep Web The Deep Web is also known as the Deep Internet is a sort of layer of content that is not indexed by the search engines…
Category : Security 10-05-2021 by Silvia Mazzetta
How to Stay Safe When Shopping Online
It can seem that not a day goes by when we don’t hear of some new hacking case or people who have had their sensitive date compromised via the internet. It’s true that cybercriminals are always coming up with new strategies to attempt to steal either money or information, but…
Category : News and events 08-01-2020 by Silvia Mazzetta
Is It Risky to Share Data While Surfing Online?
The internet is a fantastic place to learn, engage, and connect with people across the globe. From browsing social media to performing critical work tasks, the internet has become a regular, important part of our everyday lives. The average person spends almost 7 hours a day online. That's around half…
Category : Security 30-12-2019 by Janeth Kent
Unlock Hidden SmartPhone Features with these Secret Codes
Unstructured Supplementary Service Data (USSD), sometimes known as "quick codes" or "feature codes", is an extra-UI protocol, which allows people to access hidden features. This protocol was originally created for GSM phones, but can be found on CDMA devices as well (if that's a bunch of acronym gibberish to you,…
Category : Security 06-11-2022 by Janeth Kent
Level Up Your JavaScript Skills: 12 basic notions
If you are a developer at any level, understanding its basic concepts is crucial. This article highlights 12 basic concepts that are critical to understanding by any JS developer, but do not represent the full range of what a JS developer should know. 1. Value vs. Reference Variable Assignment To coding bug-free JavaScript,…
Category : Javascript 23-05-2020 by Janeth Kent
The Meaning of Colors in web Design. A little bit of psychology
Color psychology is one of the most talked about and interesting parts of psychology. The idea that some colors evoke feelings and emotions. In fact, this color helps buy the most attractive product. You invest a great deal of time and money to create a convincing website design to increase…
Category : Web design 05-08-2019 by Janeth Kent
How to Create a Brand Story through Video Marketing
Humans always have and probably always will turn to stories, be them in books or on screen, to both make sense of life and get a break from it at times, and you should be tapping into this instinctive fascination to draw people to your brand and ultimately to your…
Category : Web marketing 13-02-2019 by Janeth Kent
How to Become a Full Stack Developer in 2018
A full stack developer is someone who can work on the development of all layers of an app or program. That means that they are familiar with both the front end and back end aspects of programming. For example, full stack development would involve the development of the user interface, the…
Category : Programming 22-03-2018 by Janeth Kent
6 Reasons Why Marketing is Important for Every Business
The basis of marketing for any business is to build brand awareness, but it also contributes to a host of other factors necessary for business success. Building the foundations for a company, whatever the sector, is key to securing loyal customers and identifying yourself in a diluted marketplace. The elements…
Category : Web marketing 01-04-2020 by Janeth Kent
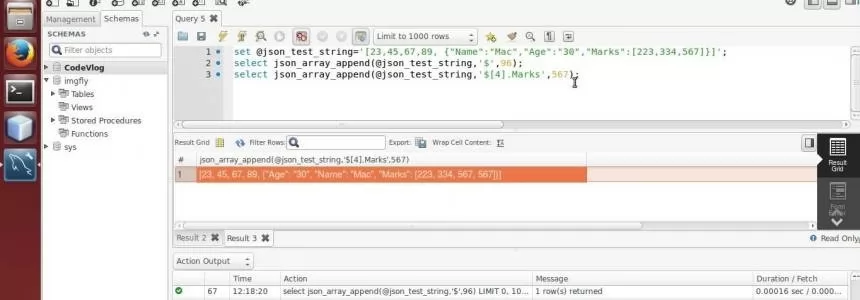
How JSON data types work in mysql
First introduced in MySQL 5.7.8, the JSON data type is a specialized binary column type, similar to a blob , but with added machinery to optimize the storage and retrieval of values from a column typed as json . Javascript Object Notation or more commonly known as JSON, is a modern…
Category : Databases 30-09-2019 by
PHP Libraries For Summer 2016
Here are our picks for the 12 most useful and interesting open-source PHP libraries that you should check out this summer! Monolog With Monolog you can create advanced logging systems by sending your PHP logs to files, sockets, databases, inboxes or other web services. The library has over 50 handlers for various…
Category : Php 11-08-2016 by Janeth Kent
Monthly News for Designers, November 2015
Today we inagurate our monthly design news post in which we will share our favorite design related articles, resources and freebies of the month. Free Icons & Templates Freebie: 100 Google Material Icons for Sketch. Freebie: Animaticons – Beautiful, Customizable Animated GIF Icons. Freebie: Branding Identity Mockup (PSD). Learning Resources, Tutorials & Tips Stretchy Navigation in CSS and jQuery by CodyHouse. Blueprint: Multi-Level Menu by…
Category : Web design 07-02-2019 by Janeth Kent
30 Best Graphic Design Books for Designers
30 Best Graphic Design Books for Designers In this collection we've listed 30 Best Graphic Design Books for Designers, these books covers a variety of topics like Typography, Workshops, Color, Layouts, References, History, Logo Design, Freelancing and Pricing. We hope these Graphic Design Books inspires you for your future design projects! Enjoy! 1. Creative…
Category : Web design 28-11-2013 by Janeth Kent
How Companies can Drive Engagement with Blogs: 50 tips
Companies can benefit by maintaining a blog: it helps drive engagement, can promote products and visibility in the market. A survey conducted by Hubspot, a marketing software company, indicates that more companies are adopting a blog and find it to be “critical” and “useful” to their business. Their survey has reported positive…
Category : Web marketing 21-08-2013 by Janeth Kent
Get Disqus Comments With Php
This script will create a configurable widget that will display the latest Disqus comments from your site. Note: You need to signup with Disqus and register a new application in order to use this script. Using the Script This script should work on any server running PHP v5+.I haven't tested it on PHPv4,…
Category : Programming 27-06-2013 by Janeth Kent
25 Useful HTML5 Tools For Web Designers & Developers
The latest version of HTML – HTML5, adds many new elements to the applications that are being developed. It's very important important for the web developers and web designers to learn and use the elements of HTML5 to develop web apps and sites. Here we have some fresh and news HTML5 resources which are…
Category : Web design 29-05-2013 by Janeth Kent
Google Wallet: your fast and secure digital wallet
Google Wallet is a convenient payment system offered by the company for Android users, previously known as Android Pay. What is Google Wallet, how does it work, and which banks support it? In 2018, Google revamped and rebranded its mobile and online payment services under the brand of Google Pay or G…
Category : Software 15-06-2023 by Janeth Kent
Facebook's top 10 social design secrets
Designing, building and growing successful social products requires a solid understanding of social behaviour and a willingness to adopt and embrace a development process that’s different to what most people are familiar with. Here are 10 principles that should get you onto the right path. Social insights Designing great social experiences starts…
Category : Social networks 17-05-2013 by Janeth Kent
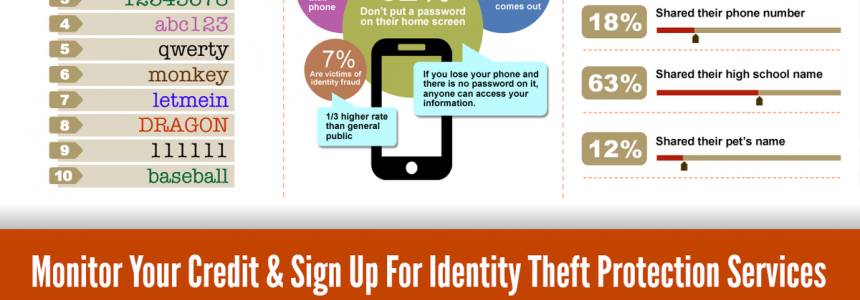
Don't become a victim of identity theft
Identity theft has always been a concern, but with more and more details of our private lives openly accessible on the Internet, it's easier than ever for cybercriminals to steal somebody's identity — which is worth $5,000. Criminals are also getting more sophisticated and tech savvy, but sometimes, we do most…
Category : Security 15-05-2013 by Janeth Kent
A Big Deal for Brands: Instagram Adds an Identity Layer
Your Instagram photos are about to get even more personal. Like its parent company, Facebook, Instagram plans to roll out an added layer of identity to its 100-million-strong photo-sharing service with the introduction of a new section and feature called “Photos of You.” It’s two things, primarily: One, it’s pretty much the introduction of…
Category : Web marketing 03-05-2013 by Janeth Kent
Install and Setup SSL in Webmin and Apache
SSL is a protocol for making secure, authenticated connections across an insecure network like the Internet. It encrypts network traffic, so that an attacker cannot listen in on the network and capture sensitive information such as passwords and credit card numbers. It allows servers to authenticate themselves to clients, so…
Category : Networking 11-04-2013 by Janeth Kent