98 results for: abilities
Examine the 10 key PHP functions I use frequently
PHP never ceases to surprise me with its built-in capabilities. These are a few of the functions I find most fascinating. 1. Levenshtein This function uses the Levenshtein algorithm to calculate the disparity or "distance" between two text strings. Named after its creator, Vladimir Levenshtein, it measures how identical two words or…
Category : Php 17-10-2023 by Silvia Mazzetta
Teaching ChatGPT to mimic your writing style
InChatGPT is an impressive conversational AI tool that showcases remarkable capabilities in various tasks. However, it also has limitations, such as occasional inaccuracies and a somewhat robotic and generic writing style. If you wish to train ChatGPT to imitate your writing style, there is a simple method you can follow.…
Category : Technology 08-06-2023 by Janeth Kent
Top best AI Image Generators: unlocking creativity with Artificial Intelligence
Artificial intelligence (AI) is revolutionizing not just business and healthcare, but also the creative industries by introducing a new era of AI-generated art. The accessibility of AI technologies and tools has paved the way for a whole new generation of artists. Contrary to the common misconception that AI will replace human…
Category : Technology 05-06-2023 by Janeth Kent
The Payment Request API: Revolutionizing Online Payments (Part 1)
The Payment Request API has emerged as the new standard for online payments, transforming the way transactions are conducted on the internet. In this two-part series, we will delve into the intricacies of this powerful API and explore how it simplifies the payment experience for both users and merchants. Part 1:…
Category : Javascript 12-06-2023 by Silvia Mazzetta
Android Hidden Codes: unveiling custom dialer codes and their functionality
In the world of Android smartphones, there exist numerous hidden codes that can unlock a treasure trove of functionalities and features. These codes, known as custom dialer codes, provide access to various settings, diagnostics, and information that are not readily available through regular menus. In this article, we will explore…
Category : Mobile 02-06-2023 by Janeth Kent
The Importance of Maintaining a Crisis-Ready Social Media Strategy: A Closer Look
Social media has revolutionized the way businesses connect with their audiences, allowing for instant communication and unprecedented reach. However, with great power comes great responsibility. As social media platforms continue to evolve, businesses must recognize the importance of being prepared for potential crises that may arise. In today's interconnected world,…
Category : Social networks 01-06-2023 by Janeth Kent
Artificial Intelligence (AI) and the Existential Threat to Humanity: Expert Perspectives
Artificial Intelligence (AI) has become an increasingly prevalent force in our modern world, revolutionizing industries and enhancing numerous aspects of our lives. However, alongside the promises and potential benefits, concerns have emerged about the potential risks associated with advanced AI systems. One of the most alarming worries is the possibility…
Category : Technology 31-05-2023 by Silvia Mazzetta
Mastering array sorting in JavaScript: a guide to the sort() function
In this article, I will explain the usage and potential of the sort() function in JavaScript. What does the sort() function do? The sort() function allows you to sort the elements of an array object. It can sort the elements in either the default ascending order or according to a custom sorting…
Category : Javascript 29-05-2023 by Janeth Kent
How artificial intelligence design the world
The image you see above was drawn especially for this article, but did not require any artistic skills or vein from its author. It was created by DALL-E, an artificial intelligence that can be asked to draw anything. To visually illustrate the point, the author of this article's lack of…
Category : Technology 17-05-2023 by Janeth Kent
Does Google's artificial intelligence have feelings?
A Google employee claims that one of the company's artificial intelligence systems is conscious, and the news bounces around the world's media. Is he crazy or enlightened? It was last month's news: Blake Lemoine, an engineer working for Google's "AI Responsible" department, claims that one of the artificial intelligence (AI) systems…
Category : Technology 04-08-2022 by Janeth Kent
Open source web design tools alternatives
There are many prototyping tools, user interface design tools or vector graphics applications. But most of them are paid or closed source. So here I will show you several open source options for you to try and use the one you like the most. Penpot Penpot is the first open source design…
Category : Web design 03-06-2022 by Nadal Vicens
How to create a .onion domain for your website
The dark web, a hidden network accessed through the Tor browser, offers enhanced privacy and anonymity for websites. To establish a presence on the dark web, you can create a .onion domain for your website. A .onion domain is an address that can only be accessed through the Tor network.…
Category : Networking 06-06-2023 by Janeth Kent
Dates in local format with Javascript
In the articles we have about dates in JavaScript we were missing one about how to create dates in local format with JavaScript. That is to say, being able to internationalise (i18n) the date before printing it. Many of you may be saying, "we have already seen this using the…
Category : Javascript 10-06-2021 by Janeth Kent
The ultimate cybersecurity checklist for programmers
In today's digital age, cybersecurity has become an essential concern for programmers. With cyber threats on the rise, it is crucial for programmers to adopt robust security practices to protect their code, data, and systems from malicious attacks. To assist programmers in this endeavor, we have compiled the ultimate cybersecurity…
Category : Security 02-06-2023 by Silvia Mazzetta
Top JavaScript libraries and frameworks part 1
JavaScript libraries and frameworks make it easy to develop websites and applications with a wide variety of features and functionality, all with dynamic, flexible and engaging features. According to a 2020 StackOverflow survey, JavaScript remains the most widely used programming language (for the eighth year), with 67.7% of respondents using it. Its…
Category : Javascript 06-05-2021 by Janeth Kent
Network attacks and how to avoid them
Nowadays it is impossible to list all the different types of attacks that can be carried out on a network, as in the world of security this varies continuously. We bring you the most common ones according to the network attack databases, so that we can keep up to date…
Category : Security 03-05-2021 by Silvia Mazzetta
htaccess Rules to Help Protect from SQL Injections and XSS
This list of rules by no means is a sure bet to secure your web services, but it will help in preventing script-kiddings from doing some basic browsing around. MySQL injection attempts are one of the most common hacking attacks against PHP websites. If your website is hosted on a dedicated…
Category : Security 01-03-2021 by Janeth Kent
Top 7 Potential Tools for Automation Testing
Today's digital economy has significantly changed how organizations deliver products and services. Many organizations are gravitating towards smart methodologies and automated tools to spark customer interest in their products and increase revenue to ensure quality and speedy deliveries. These testing tools help organizations to determine the expected and actual product delivery…
Category : Web marketing 12-02-2021 by Janeth Kent
Graphic design and its impact on Web Development
In today's article we will explain the concept of graphic design, its fundamentals and what it brings into web development. Graphic design is applied to everything visual, believe or not, it can aid in selling a product or idea, it's applied company identity as logos, colors, typography of the company…
Category : Web design 05-04-2021 by
Python or Swift: Revealing Benefits and Drawbacks of Each Language and Their Differences
Programming languages constantly evolve to improve software performance and simplify developers’ lives. That’s why the programming languages’ ranking is so unstable. Popular languages change every year. While some become outdated and uninterested due to poor features, others get ahead of the ranking because of frequent updates and outstanding performance. There…
Category : Programming 04-03-2021 by
Security of Internet providers: can we trust it?
This year has been a time of many changes. Now, more people are connected to the Internet through their home routers for teleworking, shopping, or leisure. This is where the security of Internet operators becomes more important. The question is whether the ISP's security is good enough to be the only…
Category : Security 29-05-2023 by Janeth Kent
A beginner’s guide to software vulnerabilities
What are software vulnerabilities The number of devices connected to the Internet is growing every day. And among those devices we find not only computers and smartphones, but also an ever-rising number of cameras, smoke detectors, motion sensors, smart door locks, and let’s not forget that even plant pots. Many households…
Category : Security 17-11-2020 by Iveta Karailievova
The BleedingTooth vulnerability and other Bluetooth security risks
Have you ever heard of BleedingTooth? And we do not mean the really disturbing looking mushroom which goes by this name and is totally real (we double checked) but one of the lately discovered vulnerabilities in Linux systems. It had hit the tech news recently, when Andy Nguyen, a Google security…
Category : Security 10-11-2020 by Iveta Karailievova
Introduction to REGEX - Regular Expression
Today we are going to write about Regular Expressions known as regex or shortened regexp, a very useful concept of using search patterns. Surely you were in a situation when you need to replace some word for another or character for some else. This and more you can handle with Regular…
Category : Programming 23-10-2020 by
Network and port scanning with Zenmap
This article goes out to all the computer nerds who are, when it comes to networking, more on the noob-side of the crowd. It does not have to be complicated and everyone with patience and eagerness to learn something new can relatively quickly gain the knowledge necessary to feel more…
Category : Security 08-10-2020 by Iveta Karailievova
Google Dorks: How to find interesting data and search like hacker
Go the words Google and Hacking together? Well if you thought that we will learn how to use hack Google, you might be wrong. But we can Use Google search engine to find interesting data accidentally exposed to the Internet. Such a simple search bar has the potential to help you also…
Category : Security 03-12-2021 by
Popular DNS Attacks and how to prevent them
DNS services are essential for web browsing. However, it is one of the most vulnerable to attacks. This guide will detail the most dangerous DNS attacks and some actions that will protect the network infrastructure. One of the reasons why DNS services have some susceptibility to attack is the UDP transport…
Category : Security 20-07-2020 by Silvia Mazzetta
Awesome JavaScript Games and Js Software to create Games
Best sites js13kGames 2019 - Highlights from the js13kGames 2019 competition. js13kGames 2018 - 13 Games in ≤ 13kB of JavaScript. js13kGames 2017 - Build a game in 13kB or less with js13kGames. Adventure Triangle: Back To Home - You are lost in the cave. Try to get out and back to home. Sometimes it…
Category : Javascript 30-06-2020 by Janeth Kent
Is JavaScript good for machine learning?
One of the things you always hear when you are talking to someone related to the M.L. world is that, one must learn Python because the vast majority of the major libraries are in that technology. You're probably right, but I chose JavaScript as the metal of my sword and…
Category : Javascript 16-06-2020 by Silvia Mazzetta
What is Machine Learning ?
Artificial Intelligence or AI is a trend in technology and has been the main topic of many philosophical debates as to where this field will lead us as humanity. This time I'm going to focus on a subfield of Artificial Intelligence that is Machine Learning, which I am currently very passionate…
Category : Technology 16-06-2020 by Silvia Mazzetta
What is Cyber Intelligence and how is it used?
What is Cyber-intelligence and what is it used for? This is a question that is usually asked by security, cyber-security and intelligence professionals. Cyber-intelligence is a hybrid concept between these three worlds and professional fields, and therefore it is an opportunity and a necessity to know what it is and what…
Category : Security 11-06-2020 by Silvia Mazzetta
How to save and edit photos in WebP format in GIMP
GIMP (GNU Image Manipulation Program) is a powerful open-source image editing software that provides a wide range of features and tools. While GIMP initially lacked native support for WebP format, the latest versions have integrated WebP support, making it easier than ever to save and edit photos in this efficient…
Category : Web design 29-05-2023 by Silvia Mazzetta
Web shells as a security thread for web applications
Over the past two decades, web applications as an alternative to traditional desktop application have been on to rise. As their name suggests, they are installed on web servers and accessed via a web browser. This gives web apps a rather long list of advantages: multi-platform cross-compatibility, no installation required for…
Category : Security 04-05-2020 by Iveta Karailievova
Easy Face and hand tracking browser detection with TensorFlow.js AI and MediaPipe
In March the TensorFlow team has released two new packages: facemesh and handpose for tracking key landmarks on faces and hands respectively. This release has been a collaborative effort between the MediaPipe and TensorFlow.js teams within Google Research. The facemesh package finds facial boundaries and landmarks within an image, and handpose…
Category : Programming 09-04-2020 by Luigi Nori
Cross-Origin Resource Sharing (CORS) and examples of XSS and CSRF
Cross-Origin Resource Sharing (CORS) enables web clients to make HTTP requests to servers hosted on different origins. CORS is a unique web technology in that it has both a server-side and a client-side component. The server-side component configures which types of cross-origin requests are allowed, while the client-side component controls…
Category : Javascript 30-01-2020 by Luigi Nori
Future of Artificial Intelligence for Startups
With how far-reaching the scope of Artificial Intelligence (AI) is, it is bound to make an enormous impact in the lives of people — the realm of startups is no exception. Whether you’re looking to improve your omnichannel marketing or you want to make your website more accessible to people with…
Category : Technology 11-12-2019 by Silvia Mazzetta
The best Internet search engines used by hackers
Today, many users wonder what tools hackers use to look for different vulnerabilities on devices that are connected to the Internet. Normally, everyone uses specific tools, but there are search engines that are specifically designed for security researchers. Although many users think that a hacker is a hacker, the reality is…
Category : Security 07-01-2021 by Silvia Mazzetta
How They Can Hack You While Navigating: Protecting Your Digital Security
As technology continues to advance, navigation systems have become an integral part of our daily lives. From GPS-enabled smartphones to in-car navigation systems, we rely on these tools to guide us to our destinations efficiently. However, with the rise in cyber threats, it's important to understand the potential risks associated…
Category : Security 23-06-2023 by Silvia Mazzetta
10 Open source tools for security operations (SOC)
As we know, there are many moving parts to building a Security Operations Centre (SOC). From a technological point of view, it is very important to count on open source to identify threats and reduce costs. From a DiD (Defense in Depth) point of view, there are many devices and…
Category : Security 29-11-2019 by Janeth Kent
How to Secure Remote Access Using VPN
Using a VPN to get remote access allows users to connect to aSecure server via the internet. Rather than logging into the same server directly, uses instead first login to a VPN which allows them to connect to the server more securely. This goes a long way to protecting the…
Category : Networking 24-04-2020 by Luigi Nori
The best open source javascript template engines
Today we want to publish a resource that can generate an instant boost in your workflow, here we have a list of the Best JavaScript template engines to choose from, and each of them could make your development faster and easier. When you build a JavaScript application, you'll almost certainly use…
Category : Javascript 07-08-2019 by Janeth Kent
The Best Free Alternatives to Adobe Lightroom
Adobe applications are very important to people or professionals in video, image, and audio editing. Adobe Lightroom is a photography program developed for mobile phones, Mac OS and Windows, especially for photographers or digital imaging enthusiasts. The program works perfectly but is being very expensive for many people and today…
Category : Multimedia 15-07-2019 by Janeth Kent
Understanding the JavaScript language (guidelines for beginners)
What began in 1995 as a modest 10-day project is now one of the world's most commonly used programming languages. JavaScript is actually everywhere, thanks to more advanced JavaScript engines and the introduction of frameworks like Node, Apache Cordova, Ionic, and Electron that took the language beyond the simple web…
Category : Javascript 18-06-2019 by Janeth Kent
Invest In Future By Developing Next-Generation Leaders!
For many years, those born in the Baby Boomers generation have been held most of the top-level positions of several business firms across the world and lead the respective organizations and its stakeholders towards success with highly honed skills, vast experience, and accomplished leadership abilities. However, with the members of…
Category : Web marketing 08-05-2019 by Janeth Kent
How to Make the Most of Technology in Your Business
If you’ve decided not to make use of the available technology in your business, you’ll soon find yourself falling behind the competition. More and more businesses are using technology to serve their customers better and extend their abilities. As well as understanding the importance of technology in business it’s also…
Category : Technology 16-04-2019 by Janeth Kent
Best Node Js Resources, Courses and Tutorials.
NodeJS is a platform that enables developers to write high-performance and networked applications server side. And using good old Javascript as well. Why should you study NodeJS? To begin with, it never hurts to learn something new. But most importantly, it's great to learn NodeJS. With a focus on modern JavaScript and real-world application,…
Category : Javascript 10-05-2020 by Janeth Kent
How to Become an Automation Engineer
In today’s climate, IT professionals have just about as diverse a range of career options as anybody else. One such pathway that such a professional can take is automation engineering. If you have a passion for machinery, enjoy being detail oriented, and fancy making a boatload of cash, then this…
Category : Technology 08-02-2019 by Janeth Kent
The Absolute Beginner's Guide to Sass
You've probably heard about CSS preprocessors before, whether it's Sass, LESS or Stylus, and they're all great tools to maintain your CSS, especially when you work with large codebases. For "lay" (;-)) people: A CSS preprocessor is a program that allows you to generate CSS from the unique syntax of the…
Category : Css 05-02-2019 by Janeth Kent
Javascript: is this the origin of a new developing era?
Javascript is winding up increasingly more and more. It has for quite some time been utilized for substantially more than simply the Web. Is it true that we are toward the start of a Javascript era? Javascript was originally developed for the web browser. Content should be able to dynamically change without…
Category : Javascript 13-06-2020 by Janeth Kent
Six Ways to Make Your Design Brand Stand Out with a Portfolio
Design businesses have never been more needed than they are today. With an increasing number of individuals becoming entrepreneurs and starting their own online companies, the need for professional logos, web designs, social media designs and more is on the rise. This is great news for creative professionals, with the job…
Category : Ui/ux design 21-11-2018 by Janeth Kent
80 Linux Network Monitor Software & Tools for Managing & Monitoring Unix/Linux Systems
It’s hard work monitoring and debugging Linux performance problems, but it’s easier with the right tools at the right time. Finding a Linux Network Monitor tool or Software package for your Critical servers and services that are running on those systems in one of the most (if not the most)…
Category : Security 23-10-2018 by Janeth Kent
JavaScript Manual for Beginners
The JavaScript Manual shows you how to use JavaScript and gives an overview of the language. I GETTING STARTED ABOUT Created by Netscape in 1995 as an extension of HTML for Netscape Navigator 2.0, JavaScript had as its main function the manipulation of HTML documents and form validation. Before winning this name so…
Category : Javascript 04-09-2018 by Janeth Kent
Barriers To Overcome When Starting A Business
Life is never a straightforward road, and we all encounter bumps and dips along the way. If you have a dream to start your own business, some of those bumps and dips could affect your opportunities and chances of success. You may have already encountered difficulties that have made it…
Category : Web marketing 30-04-2018 by Janeth Kent
The Rise and Fall of Business-Related VoIP Platforms
Voice over Internet protocol (VoIP) was at one time ubiquitous within the office environment. It had been employed to make crystal-clear digital phone calls, to send large packets of proprietary information and to hold webinars with attendees from around the world. However, we have recently seen a shift in regards…
Category : Software 24-04-2020 by Janeth Kent
Useful technical SEO checklist for developers
Let's start from the beginning. What is SEO? When we talk about SEO we are talking about Search Engine Optimisation: we are talking about the organic positioning of a web page in search results. And when we say organic positioning we mean unpaid positioning. SEO is a discipline, strategy or set…
Category : Seo & sem 15-05-2023 by Janeth Kent
How to Choose a Laptop for Web Design and Development
Efficiency is important at work, no matter the type of job you do. The better the tools that you use, the more productive you are. So if you’re a web designer, you want a laptop that will be able to handle all your software with ease. However, how do you…
Category : Technology 16-12-2019 by Janeth Kent
7 JavaScript Libraries for Dashboards
Dashboard is a visual indicator of an objective or a business process. It is an invaluable tool for cutting through data clutter and getting down to the essentials. It helps you to evaluate information and allow to make the correct decision in a timely manner. Live visual dashboards consist of…
Category : Javascript 11-04-2013 by Janeth Kent
PHP 7.2 will be the first Programming Language to add Modern Cryptography to its Standard Library
Last week, the voting phase closed on an RFC to add libsodium to PHP 7.2. The result was unanimous (37 in favor, 0 against). When version 7.2 releases at the end of the year, PHP will be the first programming language to adopt modern cryptography in its standard library. What is Modern…
Category : Php 14-02-2017 by Janeth Kent
Ubuntu servers security: 25 security tools to armor your system
The Ubuntu repositories contain several useful tools for maintaining a secure network and network administration.This security tools include network scanning,attack detection,Virus Detection etc. 1) Wireshark -- network traffic analyzer Wireshark is a network traffic analyzer, or "sniffer", for Unix and Unix-like operating systems. It is used for network troubleshooting, analysis, software and…
Category : Servers 14-09-2016 by Janeth Kent
MySql: How to build a performant search engine
In content-heavy websites, it becomes increasingly important to provide capable search possibilities to help your users find exactly what they’re looking for. The most obvious solution is searching your MySQL database directly, but implementing a generic MySQL search is not at all trivial. Here’s how to avoid those pitfalls and…
Category : Databases 10-09-2016 by Janeth Kent
SQLMAP installation and usage in Ubuntu and Kali linux
Let's talk about the penetration testing using one of the KALI linux tool called SQLMAP. What is SQLMAP? sqlmap is an open source penetration testing tool that automates the process of detecting and exploiting SQL injection flaws and taking over of database servers. It is a open source tool to use sql injection…
Category : Security 13-08-2016 by Janeth Kent
What is a DDOS attack and tools used
A DOS attack is an attempt to make a system or server unavailable for legitimate users and, finally, to take the service down. This is achieved by flooding the server’s request queue with fake requests. After this, server will not be able to handle the requests of legitimate users. The denial…
Category : Security 04-05-2021 by Janeth Kent
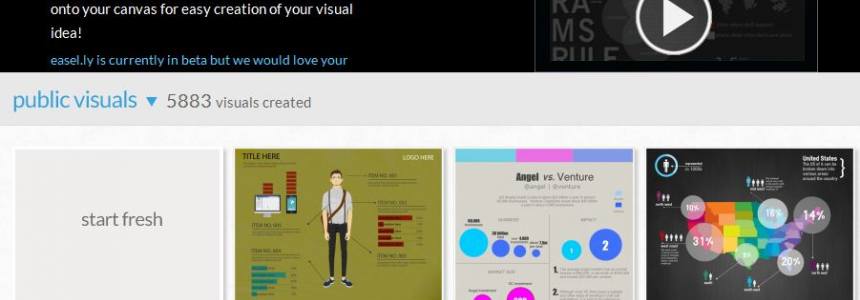
Best tools for creating infographics
Creating infographics using online tools has never been easier. In the last few years some tools have emerged that allow anyone to create great visual content. Whether you are working on a project for work, personal use, or social media, each new project will starts with a visual template. In this article, we…
Category : Web marketing 04-05-2021 by Janeth Kent
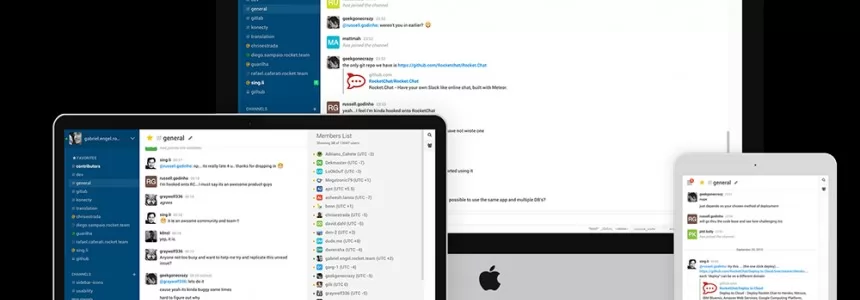
Open source alternatives to Slack
Here are some full-featured Slack alternatives that are open-source software, which means you can download it and run it on whatever server you want. That implies that you’re in charge of security, for better or worse, instead of, say, Slack. Friends This tool emerged earlier this year, Friends stands out for its…
Category : Development 02-12-2019 by Janeth Kent
PHP: list of best awesome PHP libraries
It is an exciting time to be a PHP developer. There are lots of useful libraries released every day, and with the help of Composer and Github, they are easy to discover and use. Here is a complete list of the coolest that We’ve come across. Package Management Libraries for package and…
Category : Php 27-04-2014 by Janeth Kent
Isomorphic JavaScript: a new paradigm
Spike Brehm, in a article written for http://venturebeat.com, explains that at Airbnb, they have learned a lot over the past few years while building rich web experiences by dividing into the single-page app world in 2011 with their mobile web site, launching Wish Lists and their newly-redesigned search page. Each of these is a…
Category : Javascript 27-11-2013 by Janeth Kent
PHP: Getting started with Object Oriented Programming in PHP5
This is a tutorial covers some main concepts of OOP in PHP5 with usable examples (however useless the something may be). The tutorial only covering a few fundamental subjects, all subjects are complete in and of themselves. What is OOP? Object Oriented Programming, referred to as OOP is a way to efficiently…
Category : Php 12-08-2013 by Janeth Kent
The Best Project Management Tools For Planning
Project management tools are one of the essentials when it comes to having a project run successfully. Whether you are a freelancer, or simply an owner of a small business, it comes in handy to know what is required and needed in order to manage a client’s project successfully. Programmers and engineers…
Category : Software 02-08-2013 by Janeth Kent
Learning web design: 13 e-books
E-books are great way to learn more about web design. E-books can truly provide you a fountain of knowledge of information and there’s a lot to be learnt. There are now e-books available on almost every aspect of design, from planning your business and managing your time, to designing web applications.…
Category : Web design 06-11-2015 by Janeth Kent
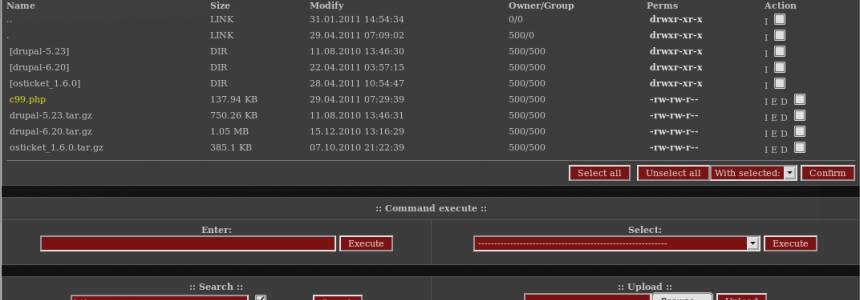
How to detect r57 and c99 Shells in your server
When malicious intruders compromise a web server, there's an excellent chance a famous Russian PHP script, r57shell, will follow. The r57 and C99 shell PHP script gives the intruder a number of capabilities, including, but not limited to: downloading files, uploading files, creating backdoors, setting up a spam relay, forging…
Category : Security 26-07-2013 by Janeth Kent
The best code editor for web developers
Every web developer requires the right tools to do their job, therefore the choice of a source code editor shouldn’t come lightly. This is where we spend most of our development time and where productivity is gained or lost on a grand scale. But which is the best Code Editor? To determine the best source code editor, we…
Category : Software 25-07-2013 by Janeth Kent
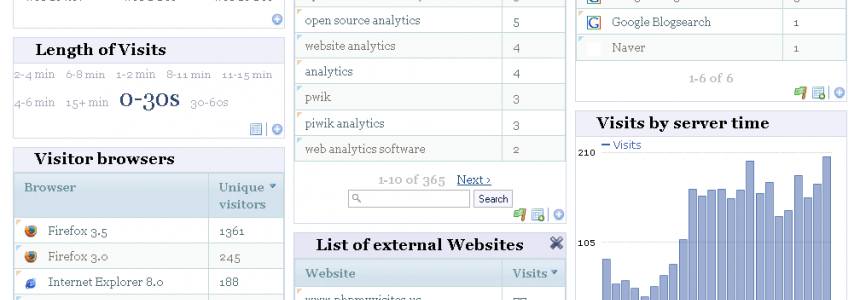
The definitive list of analytics and metrics tools
Lately I had a little problem with Google Analytics. Live results wasn't counting perfectly the number of live users online. Obviously, I am a little disappointed about it, and basically, the amount of time to research a solution or alternative would make the original content stale. Now, i want to…
Category : Software 22-07-2013 by Janeth Kent
A Collection of Essential WordPress Plugins
With so many plugins available, finding the best WordPress plugins can be hard and time-consuming! That is my motivation for gathering this comprehensive collection of Essential WordPress plugins. Enjoy! WP DB Backup WP DB Backup is an easy to use plugin which lets you backup your core WordPress database tables just by…
Category : Web design 21-08-2020 by Janeth Kent
10 Best Free Ecommerce Solutions On The Market
As the digital landscape continues to evolve, ecommerce has become an essential part of businesses worldwide. Entrepreneurs, small businesses, and even established enterprises are seeking robust and costeffective solutions to set up their online stores. In this article, we will explore the ten best free ecommerce solutions available on the…
Category : Software 21-07-2023 by Janeth Kent
Becoming a Web Professional: 19 online resources
The web education industry (designers, developers, graphics,seo,sem...) has exploded from a small niche to a powerful, continually expanding force. Countless people all over the planet are interested in learning about web design,web development, seo, sem, gamification, web marketing, and tons of companies are cropping up promising the ultimate solution. The good…
Category : News and events 18-07-2013 by Janeth Kent
Visualize Your Data: 25 Javascript Visualization Libraries
You have a huge amount of data that you need to present to your website visitors in a clear and concise way. First of all, you have to organise that data so that it's understandable to everyone in some way, right? That's where graphics come in. In web design, graphs…
Category : Javascript 03-05-2021 by Silvia Mazzetta
Top 15 Free Hacking Tools for Ethical Hackers
Intrusion tests, known as "Penetration Analysis" or "Ethical Hacking", are now a common practice to know the level of security a website has. These tests assess the type and extent of system and network vulnerabilities in terms of confidentiality and integrity. They check the security of the network and empirically verify…
Category : Security 19-06-2020 by Silvia Mazzetta
PHP 5.5: Introduction To The New Functionalities
PHP 5.5.0 has been released, bringing with it a host of new features and fixes. Here we post a review; Generators are now available Generators provide a simple way to iterate through data without having to write a class implementing the Iterator interface. Just like any other function a generator is defined with…
Category : Programming 02-07-2013 by Janeth Kent
Mastering JavaScript: Top Resources to Propel Your Learning Journey
Learning JavaScript is a valuable decision if you're interested in coding and pursuing a career in the tech industry. JavaScript holds the top spot as the most popular programming language on GitHub and is widely used by professional developers, as indicated by the Stack Overflow Developer Survey. It's worth noting that…
Category : Javascript 23-06-2023 by Janeth Kent
Google Officially Buys Waze
Today Google announced it had acquired Waze. Brian McClendon, said Waze product development would remain in Israel as a separate team, for now. “We’re excited about the prospect of enhancing Google Maps with some of the traffic update features provided by Waze and enhancing Waze with Google’s search capabilities” McClendon said. The deal was worth $1…
Category : News and events 11-06-2013 by Janeth Kent
Streamline your business with the top Invoicing Software Solutions
Top Invoicing Software for Freelancers Freelancers have to juggle multiple aspects of their business, including finding clients, maintaining a client base, invoicing, and following up on payments. Despite the challenges, it's crucial to stay organized and efficient, especially when it comes to invoicing. In this article, we will explore the best invoicing…
Category : Web marketing 14-06-2023 by Janeth Kent
A List of Best Free SQL Injection Scanners and Tools
We’ve compiled a list of free SQL Injection Scanners we believe will be of a value to both web application developers and professional security auditors. Checking for SQL Injection vulnerabilities involves auditing your web applications and the best way to do it is by using automated SQL Injection Scanners. SQLbftools –…
Category : Databases 03-06-2013 by Janeth Kent
The Best Free Online Photo Editors
Online photo editors offer a quick and effective way to edit images and allows the everyday person to take their photos one step further without having the technical knowhow that a photographer would. Today we are sharing 10 online photo editors for all of your quick fix photography needs. PIXLR Pixlr is an…
Category : Software 22-07-2021 by Janeth Kent
Big Data and Hadoop: an explanation
Our world is a potential treasure trove for data scientists and analysts who can comb through massive amounts of data for new insights, research breakthroughs, undetected fraud or other yet-to-be-discovered purposes. But it also presents a problem for traditional relational databases and analytics tools, which were not built to handle…
Category : Databases 24-05-2013 by Janeth Kent
Google Hacking Secrets: The Hidden Codes Of Google
No need for an introduction, Google is quite possibly the more powerful search engine used today, even used sometimes to check our connectivity; except that the power of the single search bar on the top of Google has become a source of concern for many, and if not they should…
Category : Security 08-04-2021 by Janeth Kent
30 HTML5 Tutorials for All Skill Levels
HTML5 is the next evolution in website development so whether you’re a web developer or a serious game developer wanting to explore the web as a new platform, HTML5 has something for each of you. If you want to learn or improve your web design skills and make the most of…
Category : Web design 17-05-2013 by Janeth Kent
50 Top Tools for Social Media Monitoring, Analytics, and Management
To start a business that will succeed in today's connected world, we need to build a community around our company, brand, and products. It can be noticed how, the last decade, social media monitoring has become a primary form of business intelligence, used to identify, predict, and respond to consumer behavior. Listening to what our…
Category : Social networks 15-05-2013 by Janeth Kent
Open Compute Project To Develop An Open Switch
In the realm of data centers and networking, the Open Compute Project (OCP) has emerged as a driving force for innovation and collaboration. Founded by Facebook in 2011, the OCP aims to accelerate the development and adoption of open hardware and data center designs. With its mission to make data center…
Category : Networking 29-05-2023 by Janeth Kent
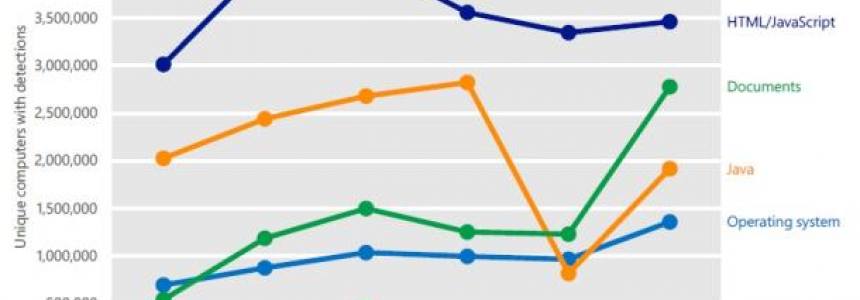
How to improve security in Firefox, Chrome, and IE
Malware is most likely to reach your computer via your browser, according to the most recent Microsoft Security Intelligence Report. (Credit: Microsoft Security Intelligence Report, Vol. 14) Like their counterparts in the real world, computer criminals are always looking for vulnerabilities they can exploit. Instead of an open window or unattended wallet,…
Category : Security 07-05-2013 by Janeth Kent
Preview the new Chrome packaged apps
A few months ago, we announced the developer preview of Chrome packaged apps and the Chrome App Launcher. That preview enabled you to to upload your Chrome packaged apps to the Chrome Web Store and test the app install flow. However, a Chrome packaged app was discoverable only if you had a direct link…
Category : Software 01-05-2013 by Janeth Kent
How to Get Started with your Freelance Branding
It is natural to be preparing so many things when you have just started doing something. When we speak of freelancing, there is also lots of preparation to do. Part of that is getting yourself ready to face the many challenges you may face in the freelance world. You also…
Category : Web marketing 02-10-2020 by Janeth Kent
Modular CSS with Media Queries and Sass
Most developers nowadays are recognizing that if you’re developing large applications that have different views and states, it is best to take a modular or object-oriented approach to your CSS development. When you throw media queries into the mix, however, the you can lose some of the benefits of modularity…
Category : Web design 23-08-2019 by Janeth Kent
6 Things to Consider when Choosing a Framework
When embarking on your next application development project, opting for a framework is a smart choice. If you're already well-versed in a particular framework, it's natural to lean towards using it. However, it's crucial to ensure that the chosen framework is truly suitable for the task at hand. To help…
Category : Programming 28-06-2023 by Janeth Kent
Free Tools For JavaScript Developers
JavaScript is one of the most widely used programming languages in the world, powering countless web applications and websites. As a JavaScript developer, having access to the right tools can greatly enhance your productivity and efficiency. In this article, we have compiled a list of free tools that every JavaScript…
Category : Javascript 21-06-2023 by Janeth Kent
SEO Basics: 8 Essentials When Optimizing Your Site
Basic search engine optimization (SEO) is fundamental. And essential. SEO will help you position your website properly to be found at the most critical points in the buying process or when people need your site. What are search engines looking for? How can you build your website in a way that…
Category : Web marketing 11-04-2013 by Janeth Kent
10 Tools for Evaluating Web Design Accessibility
Web design accessibility plays a vital role in ensuring that websites are inclusive and usable for all users, regardless of their abilities or disabilities. Evaluating the accessibility of web design is crucial to identify and address potential barriers that may hinder users' access to information and services. Thankfully, there are…
Category : Web design 29-05-2023 by Janeth Kent
Top 10 Alternatives for Whatsapp
Are you a user of the messaging app WhatsApp? If you are part of the crowd who don’t like paying for messaging apps, we’ve got 10 awesome alternative free messaging apps you can try. Recommended Reading: Send & Receive SMS On Computer With Mysms App 1. Line Line is developed by NAVER. It is a…
Category : Software 11-04-2013 by Janeth Kent
Install ISPCONFIG 3 in UBUNTU 12.04
Note: This is work in progress! You should probably test this in a virtual machine first and play around with various settings. There are a lot of tutorials over the Internet about how to configure an Ubuntu server for ISPConfig. I usually follow them, after all there aren’t so many variations on…
Category : Networking 11-04-2013 by Janeth Kent